How Graph Databases Stop E-commerce Fraud in Real Time
7 min read

As our lives become increasingly digital, a growing number of financial transactions are conducted online.
Fraudsters have been quick to adapt to this trend, and to devise clever ways to defraud online payment systems. While this type of activity can and does involve criminal fraud rings, a well-educated fraudster can create a very large number of synthetic identities on his or her own and use these to carry on sizeable schemes.
Fortunately, graph database technology is able to detect the patterns that arise around these e-commerce fraud scenarios and put an end to them in real time – before a fraudster can inflict significant damage.
In this series on fraud detection, we’re going to take a closer look at how graph databases help detect and mitigate three types of fraud:
- First-party bank fraud
- Insurance fraud
- E-commerce fraud
This week, we’ll take a closer look at e-commerce fraud detection.
A Typical E-commerce Fraud Scenario
Consider an online transaction with the following identifiers:
- User ID
- IP address
- Geo location
- A tracking cookie
- Credit card number
One would typically expect the relationships between these identifiers to be fairly close to one-to-one. Some variations are naturally to be tolerated to account for shared machines, families sharing a single credit card number, individuals using multiple computers and the like.
However, as soon as the relationships begin to exceed a reasonable number, e-commerce fraud is often at play. For example: A large numbers of users may have transactions originating from the same IP, large numbers of shipments to different addresses may use the same credit card, or a large numbers of credit cards may all use the same address.
In each of these scenarios, it is the pattern inside the graph – discovered by walking the relationships between disparate pieces of information – that can serve as strong indicating signals of an e-commerce fraud event.
The more interconnections exist amongst identifiers, the greater the cause for concern. Large and tightly-knit graphs are very strong indicators that fraud is taking place.
How Graph Databases Help with E-commerce Fraud Detection
As in the first-party bank fraud and insurance fraud examples from previous weeks, graph databases are designed to carry out pattern discovery in real time across precisely these kinds of datasets.
By putting checks into place and associating them with the appropriate event triggers, such schemes can be uncovered before they are able to inflict significant damage. Triggers can include events such as login, placing an order or registering a new credit card.
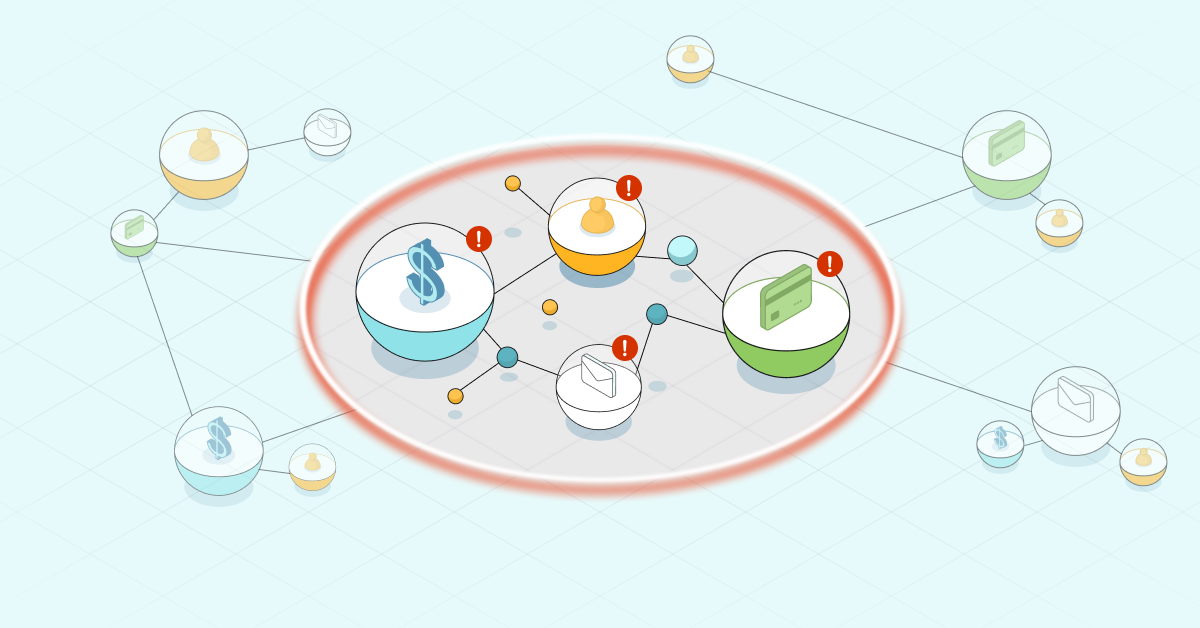
The graph below shows a series of transactions from different IP addresses. IPx represents distinct IP address, CCx distinct Credit Card number, IDx represents the UserID used to carry out the online transaction and CKx refers to a specific cookie stored in the system.
In this example, there is a likely e-commerce fraud event occurring from IP1, which has carried out multiple transactions using five credit cards, one of which (CC1) is used by multiple IDs, where two cookies (CK1 and CK2) each share two IDs.
Graph databases are the ideal enabler for efficient and manageable fraud detection solutions. From fraud rings and collusive groups, to educated criminals operating on their own, graph databases uncover a variety of important e-commerce fraud patterns – and all in real time.
Want to learn more about how graph databases improve fraud detection? Download this white paper, Fraud Detection: Discovering Connections with Graph Databases.
Catch up with the rest of the fraud detection series: