Fine-Grained Access Control for Better Security and Privacy
Secure Your Applications Data With Comprehensive Data Access Controls
Neo4j is committed to discovering new ways graph technology can strengthen application security. Data security is a critical priority for all organizations. With rapid changes in application development, today’s graph database must enforce rigorous enterprise security rules, while remaining easy to deploy and manage. Some of the top security needs we focus on include role-based, confidentiality, privacy, legal, and compliance.
Schema-Based Security
The data in a graph database is not the only thing that needs protection. The structure of the relationships and nodes in a graph are themselves information. Our security takes this into account. Neo4j’s schema-based security makes it easy to enforce a deeper level of protection by controlling users' ability to traverse and read from different parts of the graph. This ensures that only authorized users have access to the data they need to protect sensitive data.
Identity and Access Control
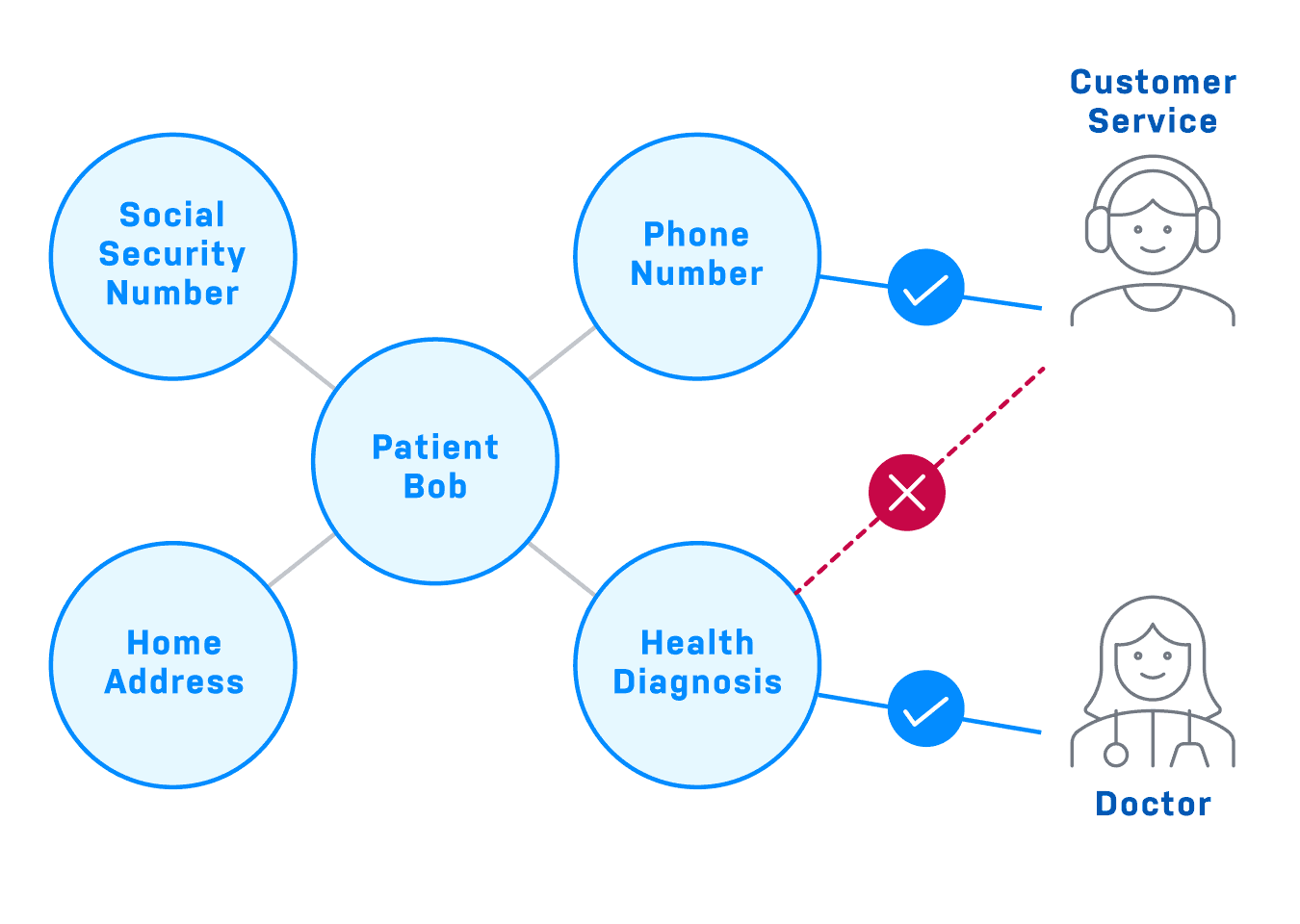
Neo4j provides a secure platform that offers granular security, down to individual objects and their properties. This includes controls permission to traverse, read or write data based on node labels, relationship types, and database and property names. With a role-based access control approach, you can apply these restrictions to roles assigned to users at any level of granularity throughout the graph. This greatly simplifies the task of assigning permissions and helps ensure that your data is secure.
Data Privacy
Neo4j's multi-database capabilities make it easy for organizations to adhere to privacy and security regulations by enabling tenant isolation. For example, you can restrict who has access to personally identifiable information (PII) within an organization. Building security into the database simplifies secure application development. Rather than tasking developers with security, they can focus on writing applications against a scalable and secure Neo4j database. This approach enables organizations to confidently develop applications in a secure environment while maintaining the high performance and availability required.
Resources
