Neo4j Single Sign-On (SSO) configuration
Neo4j supports SSO authentication and authorization through identity providers implementing the OpenID Connect (OIDC) standard. This page features detailed examples of how to configure Single Sign-On (SSO) for several identity providers. It also presents frequently asked questions and solutions to common problems encountered when configuring SSO.
|
The following configurations are crafted for a Neo4j Browser served on Therefore, when reproducing them in the identity providers, you must modify the redirect URI to include the URI serving your Neo4j Browser application. For example:
|
SSO works in the following way:
-
The server (Neo4j DBMS) contacts the identity provider (Okta, Entra ID, Google, etc.) and fetches the JSON Web Keys (JWKs) from the provider.
-
The client (e.g., Bloom, Neo4j Browser, etc.) asks the user for credentials and contacts the identity provider.
-
The identity provider responds with a JSON Web Token (JWT), a JSON file containing fields (claims) relative to the user (email, audience, groups, etc.).
-
The client provides the server with the JWT, and the server verifies its signature with the JWKs.
JWTs must always contain a value for
subeven when using a different claim forusername. It is the only claim guaranteed to be unique and stable. Other claims, such asemailorpreferred_usernameare less secure and may change over time. They should not be used for authentication. Neo4j may assign permissions to a user based on this username value in a hybrid authorization configuration. Thus, changing the username claim fromsubis not recommended.
Okta
Access token
This example shows how to configure Okta for authentication and authorization using access tokens.
-
Configure the client with the appropriate redirect URI. You can skip the group assignments in this step:
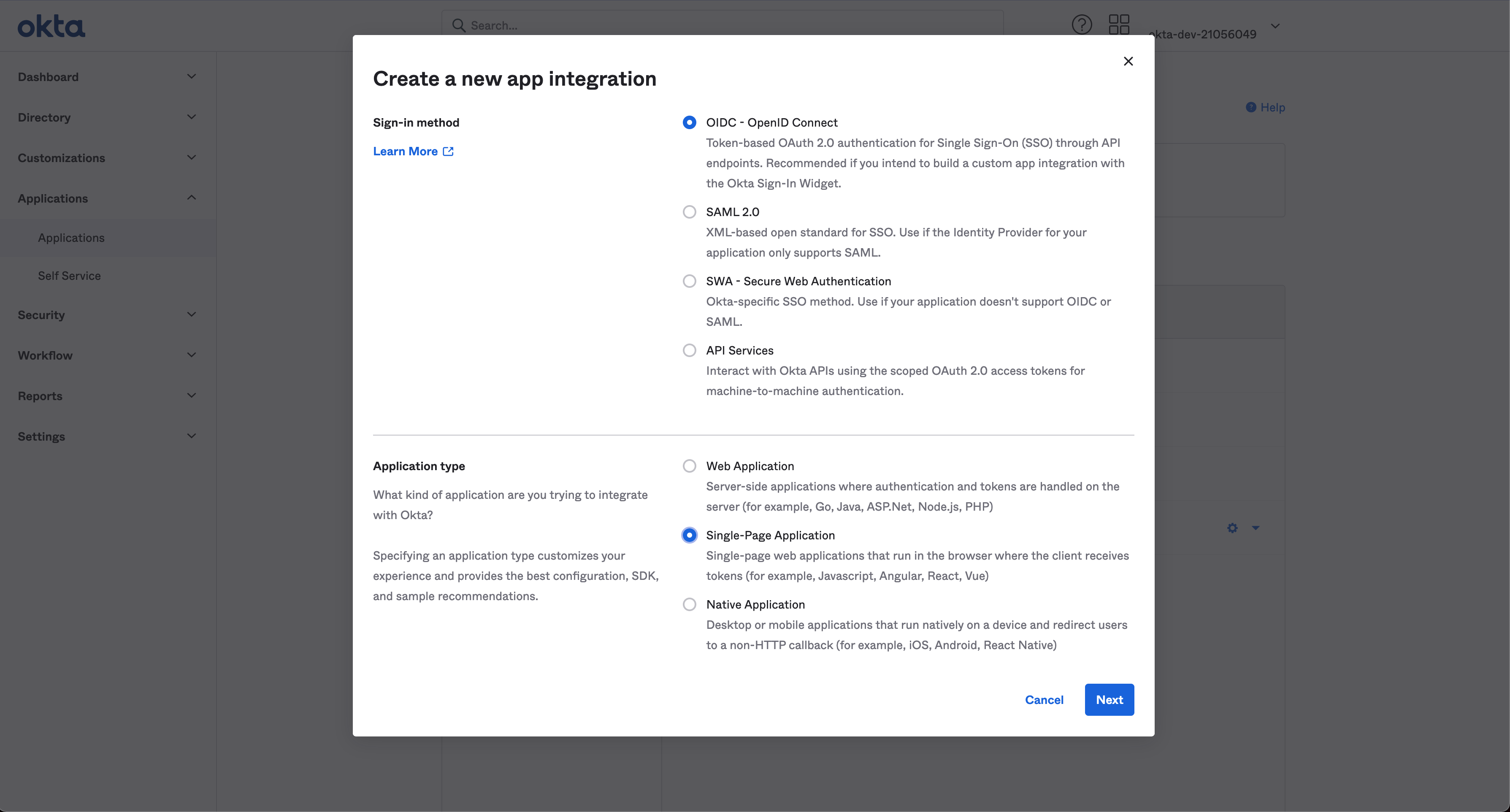 Figure 1. Okta OIDC client creation
Figure 1. Okta OIDC client creation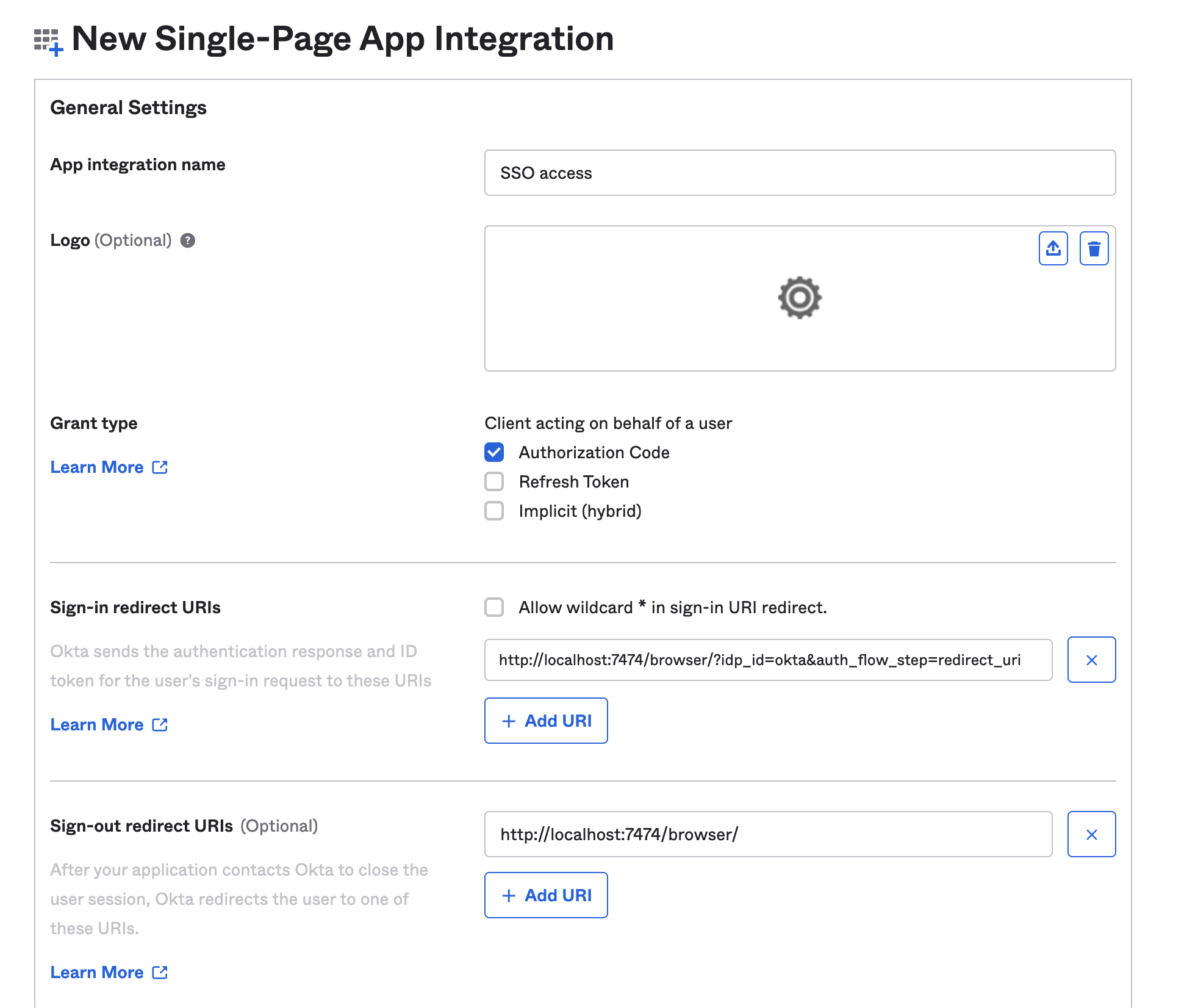 Figure 2. Okta OIDC client configuration
Figure 2. Okta OIDC client configuration -
Take note of the Client ID and the Okta domain. You will need them later when configuring the Okta parameters and the Well-known OpenID Connect endpoint in the neo4j.conf file:
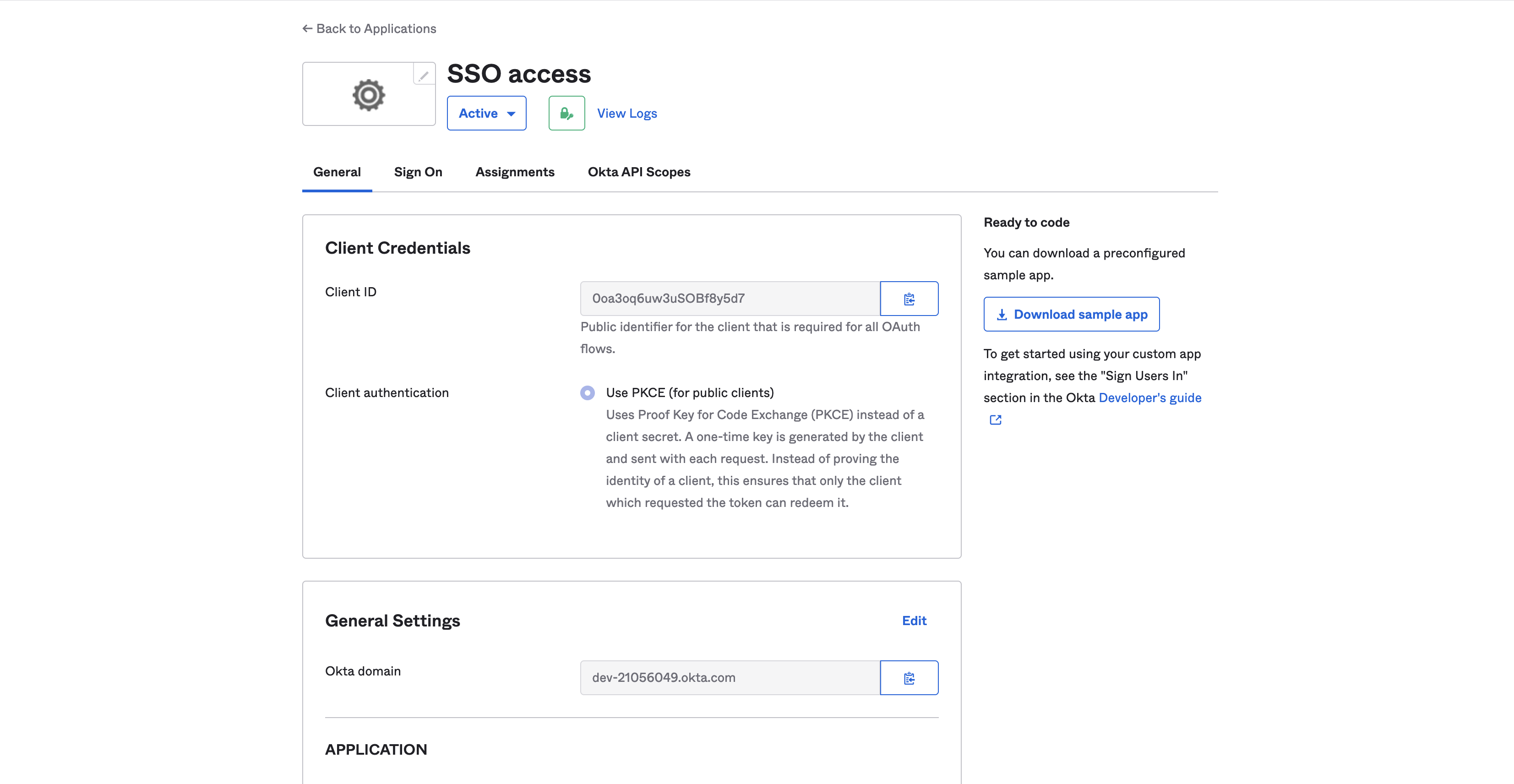 Figure 3. Okta OIDC client configuration
Figure 3. Okta OIDC client configuration -
Create groups in Okta, assign users to them (the user can be added to a group either on user creation or editing the group), and map them in the
neo4j.confto native groups: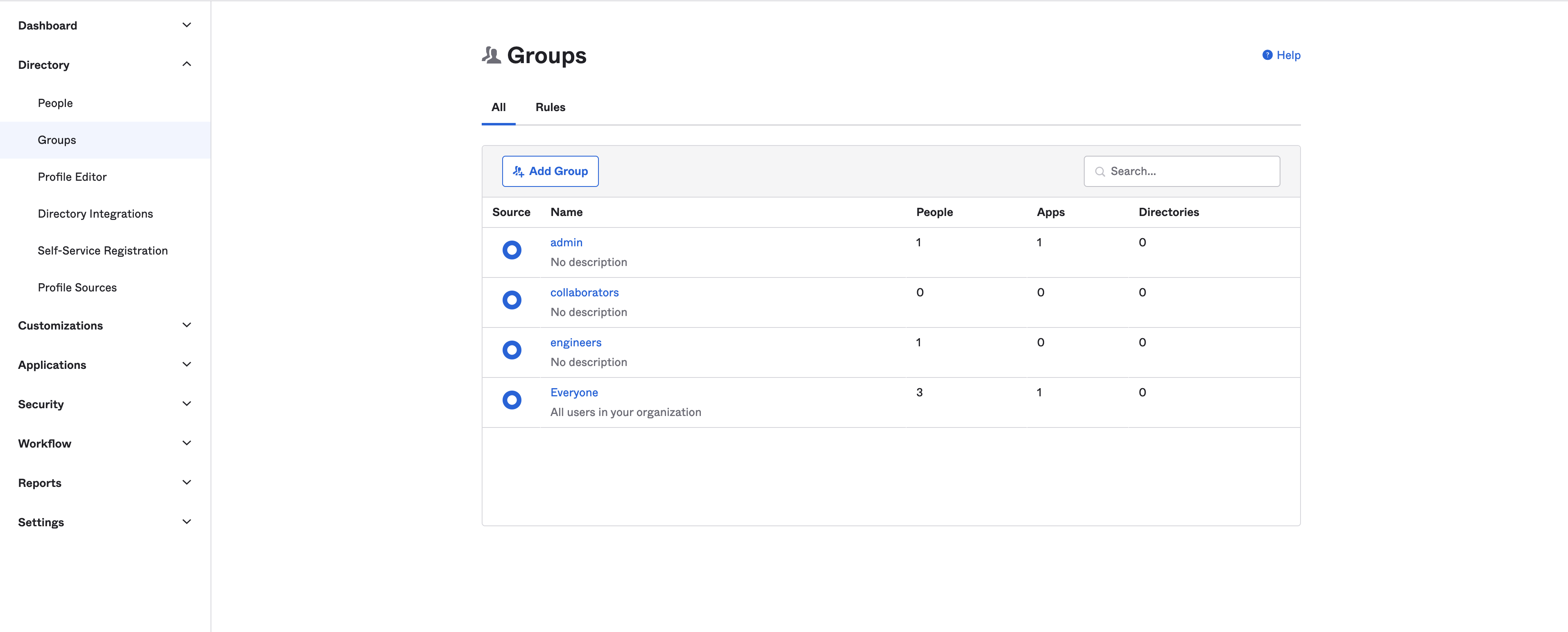 Figure 4. Okta OIDC server groups
Figure 4. Okta OIDC server groups -
Configure the default authorization server (the one that shows
api://defaultas audience) to return thegroupsclaim in access tokens: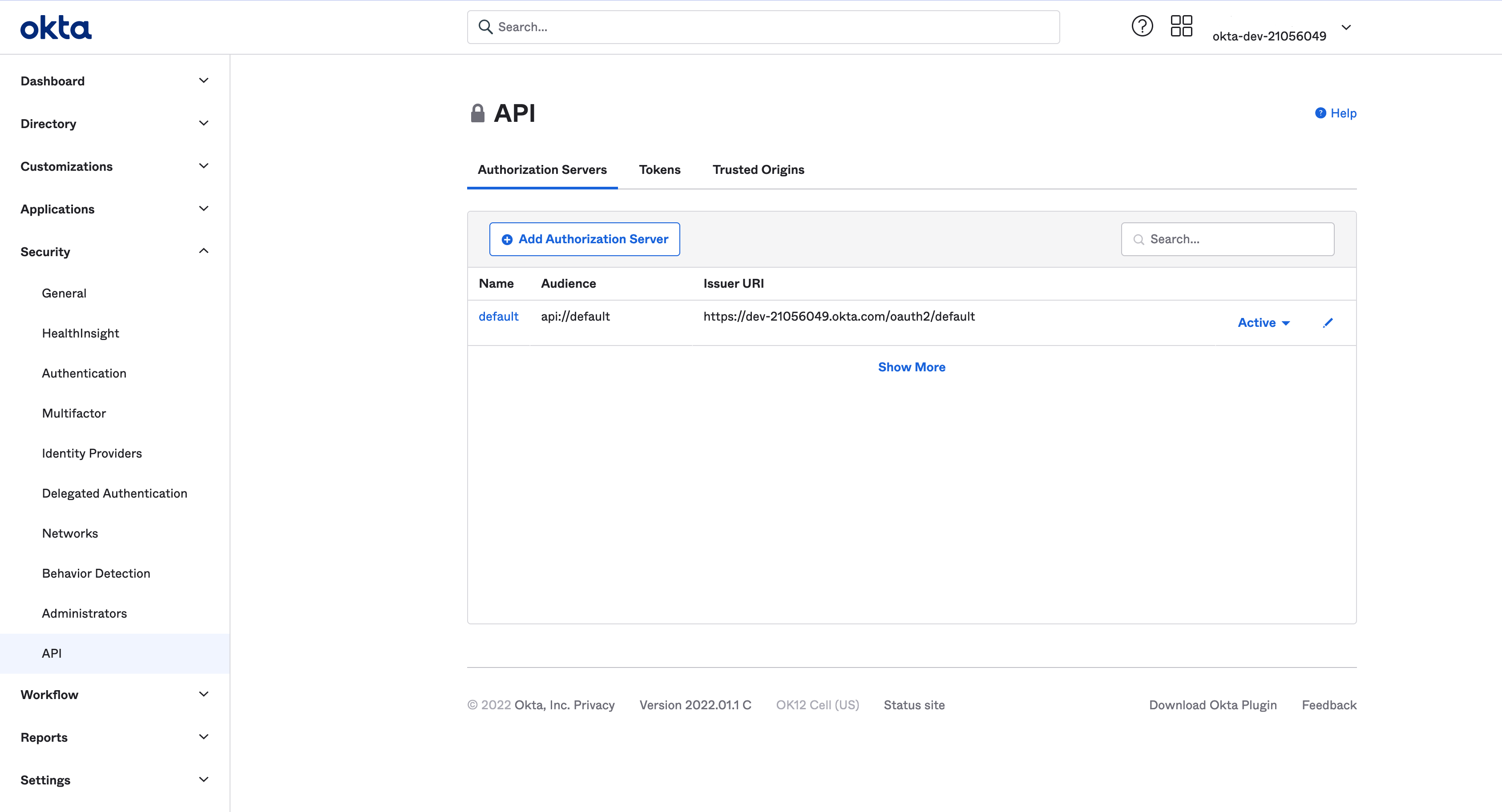 Figure 5. Okta OIDC authorization server
Figure 5. Okta OIDC authorization server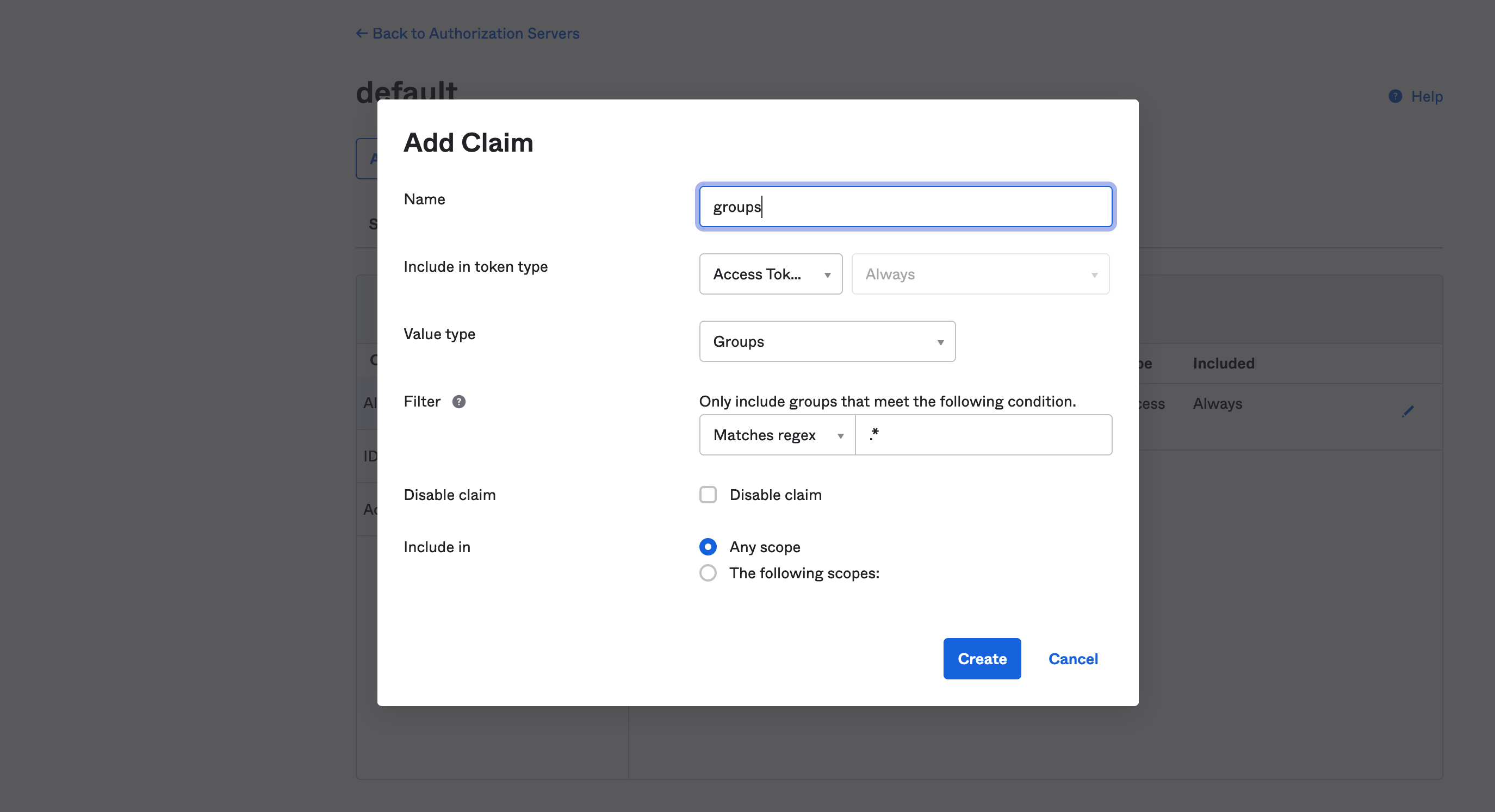 Figure 6. Okta OIDC server claims
Figure 6. Okta OIDC server claims -
Configure Neo4j to use Okta authentication by configuring the following settings in the neo4j.conf file:
dbms.security.authentication_providers=oidc-okta dbms.security.authorization_providers=oidc-okta dbms.security.oidc.okta.display_name=Okta dbms.security.oidc.okta.auth_flow=pkce dbms.security.oidc.okta.well_known_discovery_uri=https://dev-21056049.okta.com/oauth2/default/.well-known/openid-configuration dbms.security.oidc.okta.audience=api://default dbms.security.oidc.okta.claims.username=sub dbms.security.oidc.okta.claims.groups=groups dbms.security.oidc.okta.params=client_id=0oa3oq6uw3uSOBf8y5d7;response_type=code;scope=openid profile email dbms.security.oidc.okta.authorization.group_to_role_mapping= "engineers" = admin; \ "collaborators" = readerThe
token_type_principaland thetoken_type_authenticationare omitted, meaning access tokens are used instead. -
Log in with your Okta SSO credentials using the email of an
engineerrole user that results in anadminrole in the database: Figure 7. Okta OIDC successful login
Figure 7. Okta OIDC successful login
ID token
This example shows how to configure Okta for authentication and authorization using ID tokens.
-
Follow the first two steps from the instructions for Access token.
-
Create the claims as indicated:
Figure 8. Okta claim creation panelIn the case of access tokens, a default sub is already provided automatically. However, for ID tokens, the name you give to your claim needs to be also indicated in the configuration
dbms.security.oidc.okta.claims.username=userid. -
Configure the default authorization server (the one that shows api://default as audience) as indicated:
dbms.security.authentication_providers=oidc-okta, native dbms.security.authorization_providers=oidc-okta dbms.security.oidc.okta.display_name=Okta dbms.security.oidc.okta.auth_flow=pkce dbms.security.oidc.okta.well_known_discovery_uri=https://trial-2696363.okta.com/oauth2/default/.well-known/openid-configuration dbms.security.oidc.okta.audience=0oa42hwrygsUCFlLO697 dbms.security.oidc.okta.claims.username=userid dbms.security.oidc.okta.claims.groups=groups dbms.security.oidc.okta.params=client_id=0oa42hwrygsUCFlLO697;response_type=code;scope=openid profile email dbms.security.oidc.okta.authorization.group_to_role_mapping="admin_group" = admin; dbms.security.oidc.okta.config=token_type_principal=id_token;token_type_authentication=id_token -
You should now find the audience under Okta’s sign-on tab:
Figure 9. Okta’s sign-on tab
Microsoft Entra ID (formerly Azure Active Directory)
Access token
This example shows how to configure Entra ID for authentication and authorization using an access token.
-
Set parameters to be
access_token:dbms.security.oidc.azure.config=principal=unique_name;code_challenge_method=S256;token_type_principal=access_token;token_type_authentication=access_token -
Add the following parameter:
dbms.security.oidc.azure.token_endpoint=https://login.microsoftonline.com/54e85725-ed2a-49a4-a19e-11c8d29f9a0f/oauth2/v2.0/tokenThe GUID is the directory (tenant) ID. You can find it on the app registration page:
-
Include the issuer:
dbms.security.oidc.azure.issuer=https://sts.windows.net/54e85725-ed2a-49a4-a19e-11c8d29f9a0f/As previously mentioned, the GUID here is also the directory (tenant) ID. Make sure you add the trailing slash (
/) at the end or this operation might fail. -
Go to the "Expose an API" tab and click "Add a Scope" to include the following statement:
dbms.security.oidc.azure.params=client_id=4376dc8b-b5af-424f-9ada-c1c1b2d416b9;response_type=code;scope=openid profile email api://4376dc8b-b5af-424f-9ada-c1c1b2d416b9/access-token -
Add the value in the scope column to the scopes in the configuration. Note that the audience parameter for access tokens are typically set with` api://` at the front.
ID token
This example shows how to configure Entra ID for authentication and authorization using ID tokens.
Register the application
-
Log in to the Azure portal.
-
Navigate to Microsoft Entra ID > Overview.
-
From the Add dropdown menu, select App registration and fill in the following information to create your SSO application:
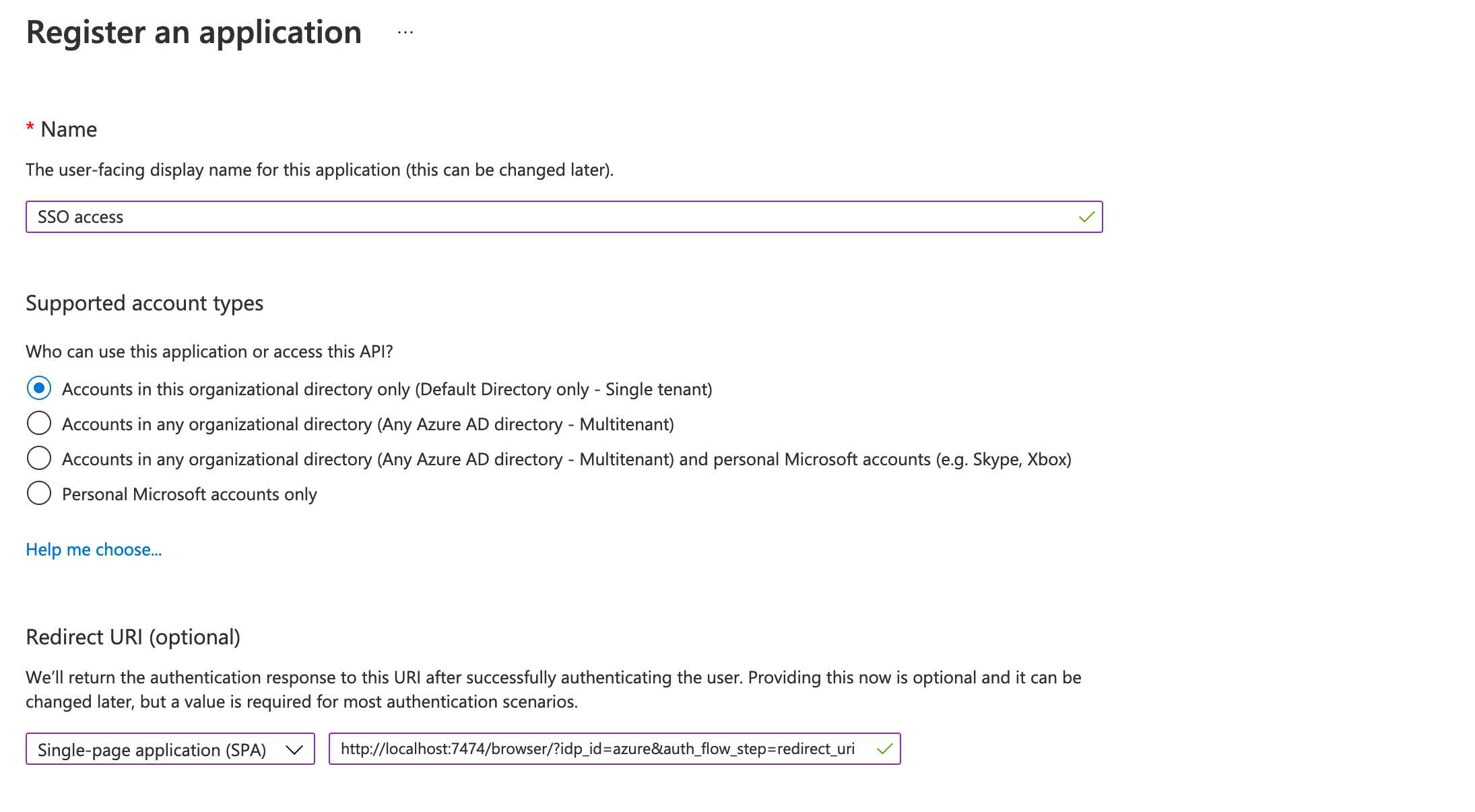 Figure 10. Entra OIDC client creation
Figure 10. Entra OIDC client creationThe redirect URI
http://localhost:7474/browser/?idp_id=azure&auth_flow_step=redirect_uriis the URI that will accept returned token responses after successful authentication. -
Click Register.
Configure Neo4j
-
After the successful app creation, on the app’s Overview page, find the Application (client) ID value. Use it to configure the following properties in the neo4j.conf file.
dbms.security.oidc.azure.audience=c2830ff5-86d9-4e38-8a2b-9efad6f3d06d dbms.security.oidc.azure.params=client_id=c2830ff5-86d9-4e38-8a2b-9efad6f3d06d;response_type=code;scope=openid profile email -
Navigate to Endpoints, to find the OpenID Connect metadata document. Use it to configure the
well_known_discovery_uriin the neo4j.conf file.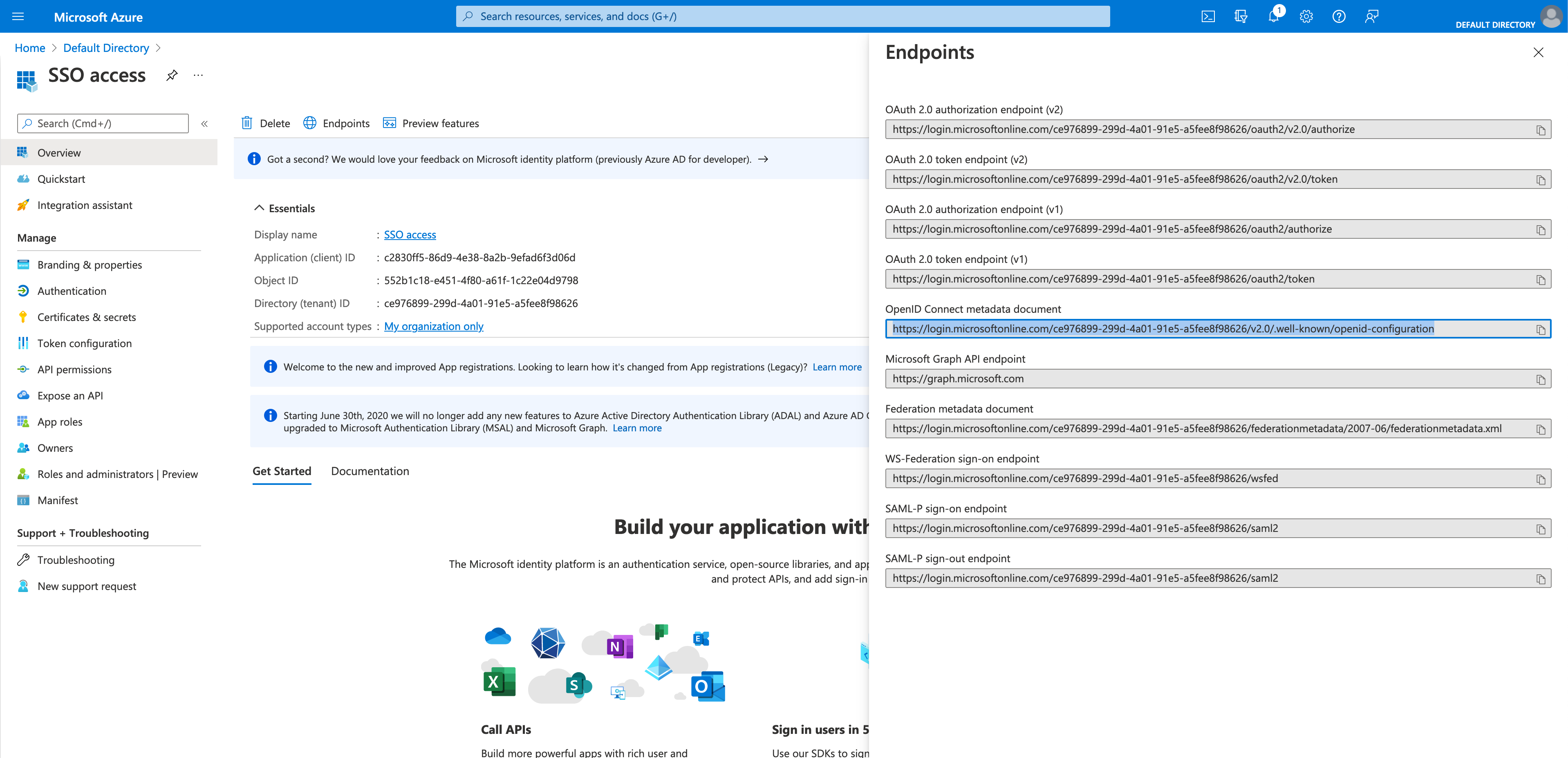 Figure 11. Entra OIDC client config
Figure 11. Entra OIDC client configdbms.security.oidc.azure.well_known_discovery_uri=https://login.microsoftonline.com/ce976899-299d-4a01-91e5-a5fee8f98626/v2.0/.well-known/openid-configuration -
Configure Neo4j to use Entra ID authentication by configuring the following settings in the neo4j.conf file:
dbms.security.authentication_providers=oidc-azure dbms.security.authorization_providers=oidc-azure dbms.security.oidc.azure.display_name=Azure dbms.security.oidc.azure.auth_flow=pkce dbms.security.oidc.azure.config=token_type_principal=id_token;token_type_authentication=id_token -
Configure which JWT claim should be used for usernames. Possible values are
sub,email, orpreferred_username.subis the only claim guaranteed to be unique and stable. For details, see Microsoft documentation as well as the OpenId spec.dbms.security.oidc.azure.claims.username=sub
Map Entra groups to Neo4j roles
Decide whether you want to use Entra groups directly or Entra App Roles.
Using Entra groups directly might be convenient if you already have users assigned to those groups and want to perform Group-to-Role mapping in Neo4j settings.
Entra App Roles allow a layer of separation between Neo4j roles and groups. When App Roles are used, only the roles relevant to Neo4j are sent in the JWT token. This prevents leaking permissions between applications. JWT tokens also have a limitation of 200 roles per token per user, which can be avoided by sending only the relevant App Roles.
Details about Entra ID App Roles can be found in the Microsoft documentation.
Using Entra groups directly
-
Configure the server to return the Group Object IDs in the JWT identity tokens. To do this, set
groupMembershipClaimstoSecurityGroupin the Manifest of the registered application: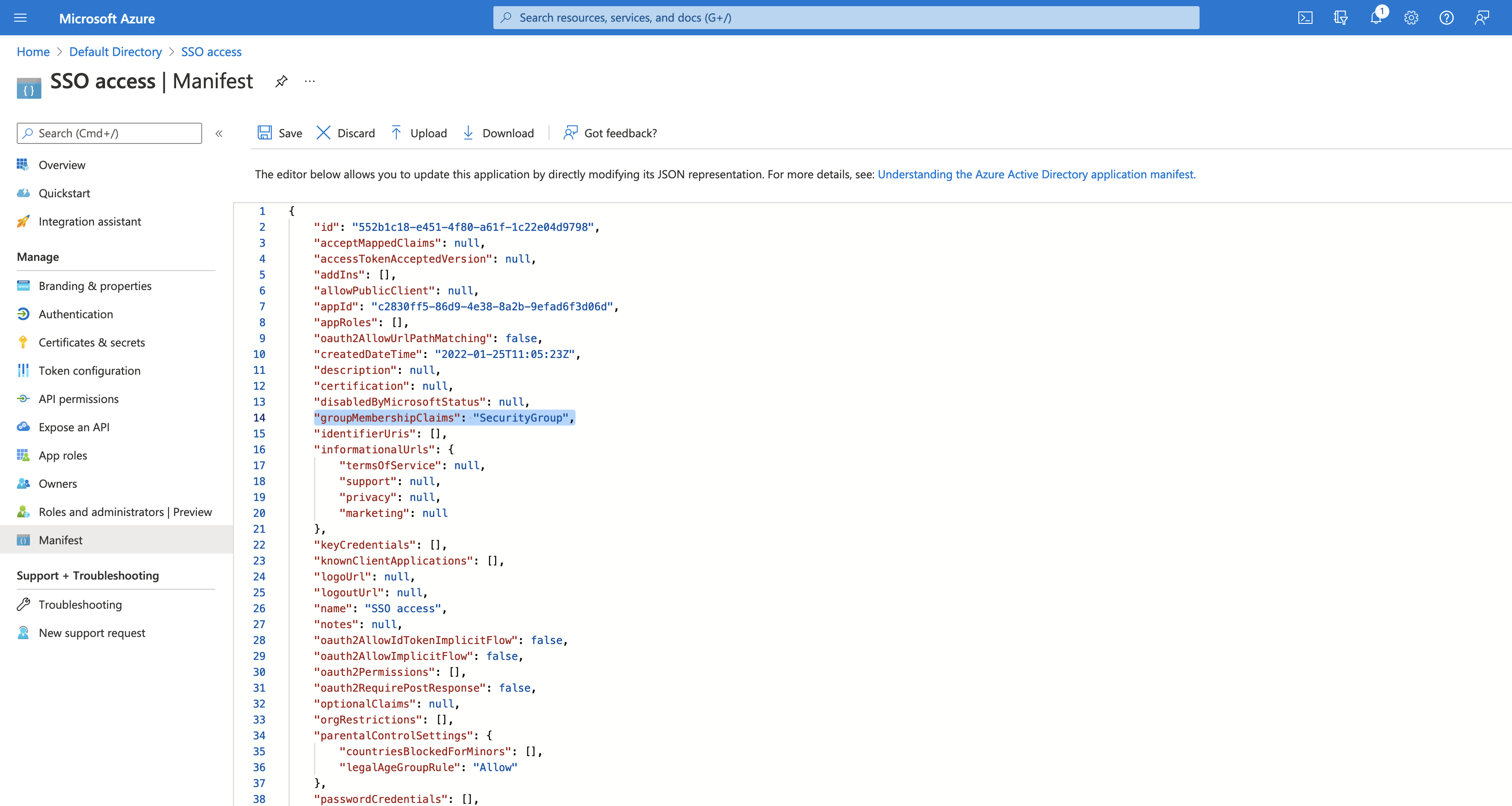 Figure 12. Entra OIDC server claims
Figure 12. Entra OIDC server claims -
Create groups in the Entra AD console and assign users to them. Take note of the Object Id column. In the next step, you must map these to user roles in the Neo4j settings.
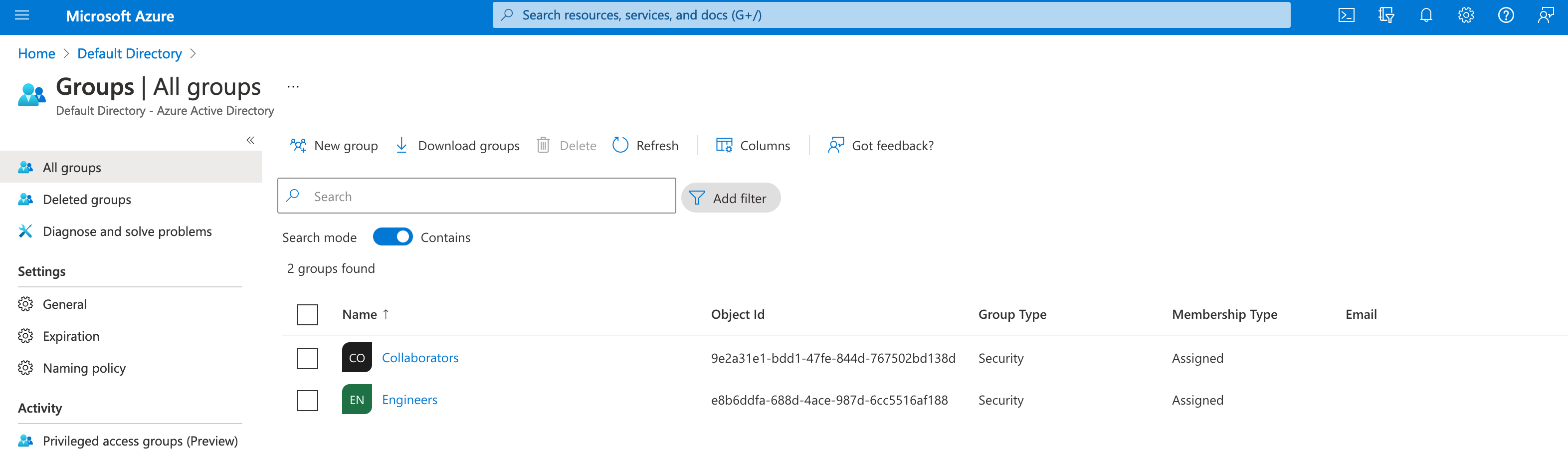 Figure 13. Entra OIDC server groups
Figure 13. Entra OIDC server groups -
Configure a mapping from Entra Group Object IDs to Neo4j roles. For details, see Map the Identity Provider Groups to the Neo4j Roles.
dbms.security.oidc.azure.authorization.group_to_role_mapping= "e8b6ddfa-688d-4ace-987d-6cc5516af188" = admin; \ "9e2a31e1-bdd1-47fe-844d-767502bd138d" = reader -
Configure Neo4j to use the
groupsfield from the JWT token.dbms.security.oidc.azure.claims.groups=groups
Using Entra ID App Roles
-
On the app’s home page, navigate to App roles and add the Neo4j roles to the Microsoft Entra ID.
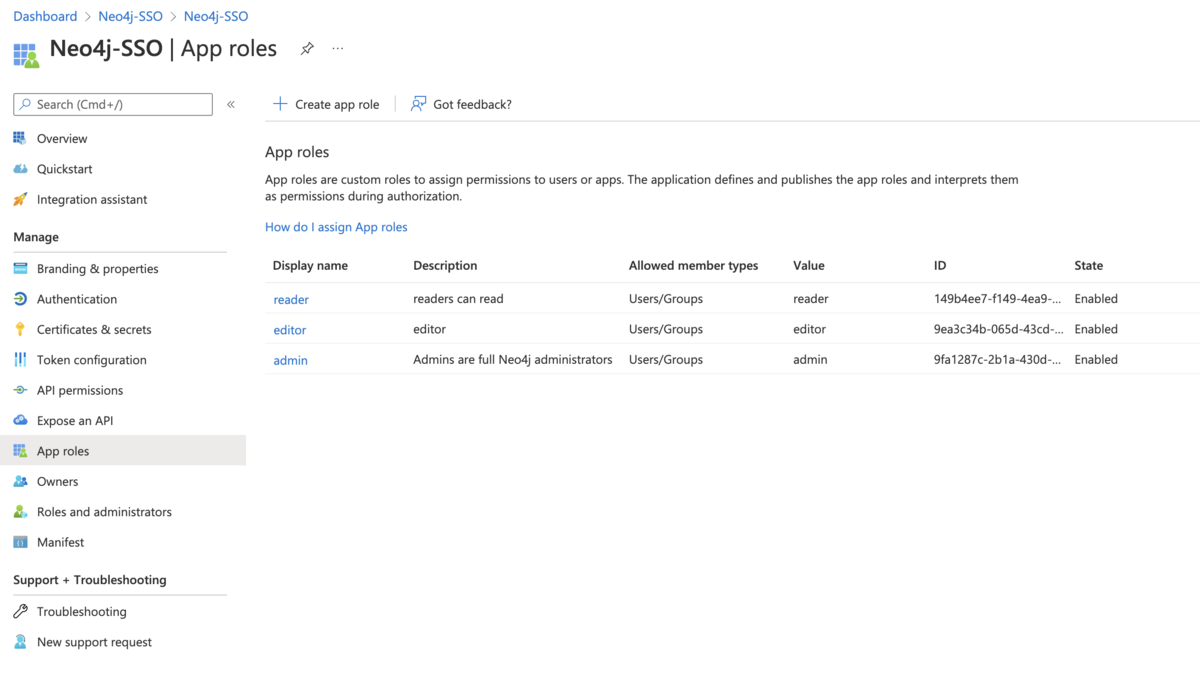 Figure 14. Entra OIDC app roles config
Figure 14. Entra OIDC app roles config -
The Value column in the App roles config must either correspond to Neo4j Roles or be mapped in the neo4j.conf file. For details, see Map the Identity Provider Groups to the Neo4j Roles.
dbms.security.oidc.azure.authorization.group_to_role_mapping= "managers" = admin; \ "engineers" = reader -
Configure Neo4j to use the
rolesfield from the JWT token.dbms.security.oidc.azure.claims.groups=roles
This example shows how to use Google OpenID Connect for authentication using ID tokens in conjunction with native authorization.
-
Configure the client and the redirect URI:
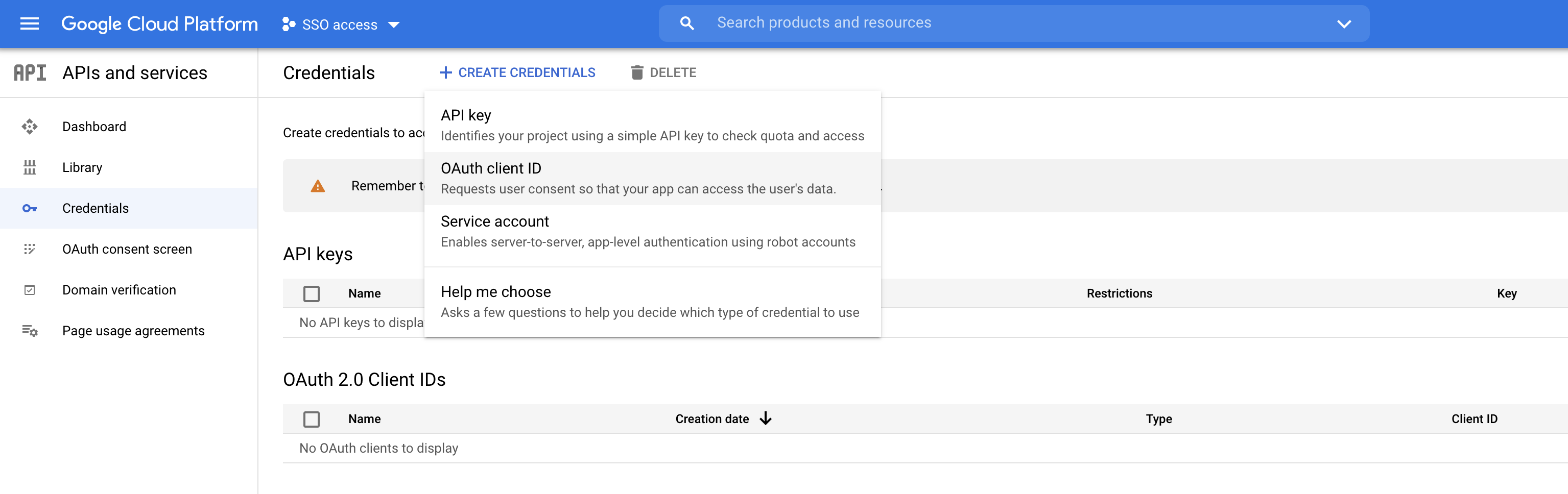 Figure 15. Google OIDC client creation
Figure 15. Google OIDC client creation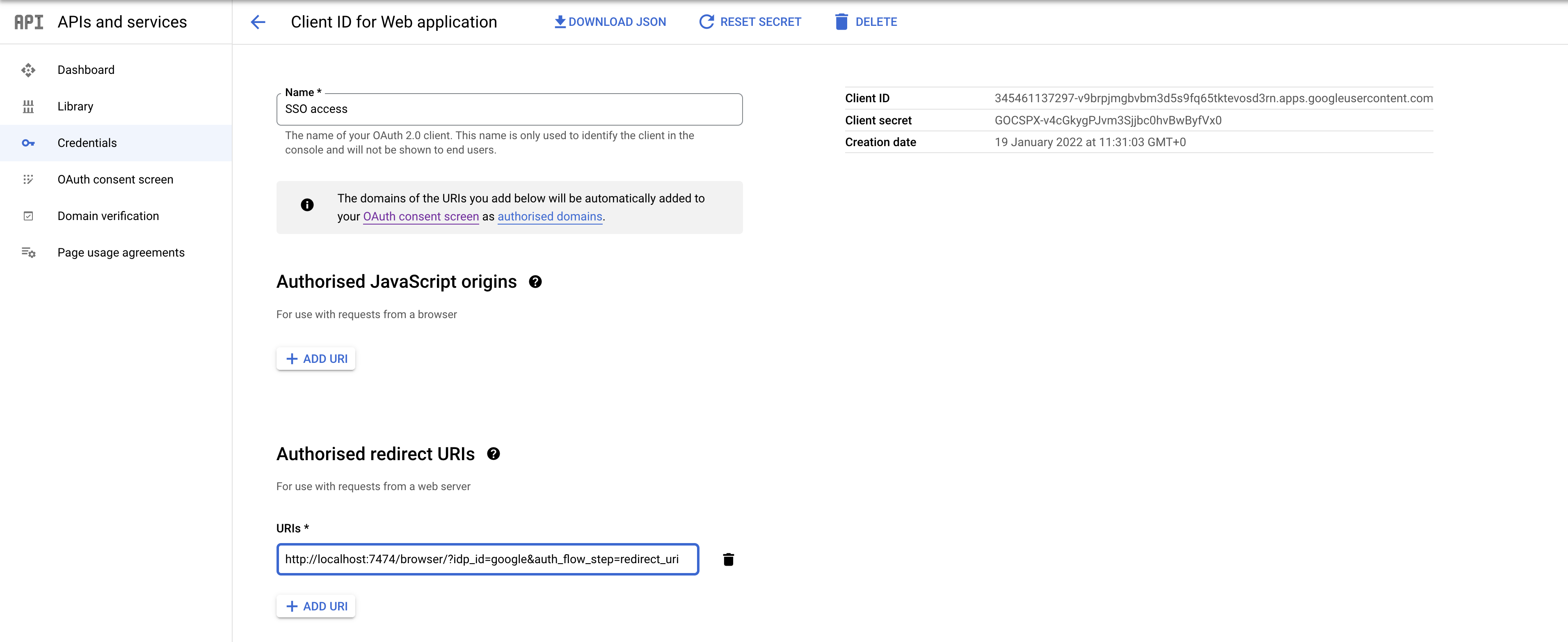 Figure 16. Google OIDC client configuration
Figure 16. Google OIDC client configurationSSO authorization does not work with Google, as the JWT returned by Google does not contain information about the groups that a user belongs to, and cannot be configured to. Therefore, it is recommended to use native (or another flavor) authorization by creating a native version of the user in Neo4j.
-
The role assigned to the email used to log in with SSO, in this case,
alice@neo4j-test.com, must haveGRANT ROLEpermissions in the database (nativeauthentication temporarily enabled):CREATE USER `alice@neo4j-test.com` SET PASSWORD 'secretpassword'; GRANT ROLE admin to `alice@neo4j-test.com`; -
Configure Neo4j to use Google authentication by configuring the following settings in the neo4j.conf file:
dbms.security.authentication_providers=oidc-google dbms.security.authorization_providers=native dbms.security.oidc.google.display_name=Google dbms.security.oidc.google.auth_flow=pkce dbms.security.oidc.google.well_known_discovery_uri=https://accounts.google.com/.well-known/openid-configuration dbms.security.oidc.google.audience=345461137297-v9brpjmgbvbm3d5s9fq65tktevosd3rn.apps.googleusercontent.com dbms.security.oidc.google.claims.username=email dbms.security.oidc.google.params=client_id=345461137297-v9brpjmgbvbm3d5s9fq65tktevosd3rn.apps.googleusercontent.com;response_type=code;scope=openid profile email dbms.security.oidc.google.token_params=client_secret=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 dbms.security.oidc.google.config=token_type_principal=id_token;token_type_authentication=id_token -
Log in with your Google SSO credentials using the email address and get the
adminrole when doing so: Figure 17. Entra OIDC successful login
Figure 17. Entra OIDC successful loginThe native authentication is disabled to prevent someone from logging in to alice@neo4j-test.com with the set password.
FAQ
When should pkce be used as auth flow?
Assuming the client (Neo4j Browser or Bloom) can be accessed through the public internet, always use pkce auth-flow rather than implicit because the latter requires the client’s secret to be available to the public client.
In general, if both flows are available, it is recommended to opt for pkce because it is more secure than implicit.
Is Google authentication secure if it has a client secret listed in the config?
Yes.
Google uses the pkce flow, but identity providers sometimes also use a client secret to ensure the client asking for a token is the one using it (pkce does not guarantee that).
The client secret does not add any additional security as it is public but the pkce flow provides sufficient security.
Could not parse JWT of type "access_token"
When getting the message Failed to get credentials: Could not parse JWT of type "access_token" on Browser, it probably means the provider only accepts ID tokens.
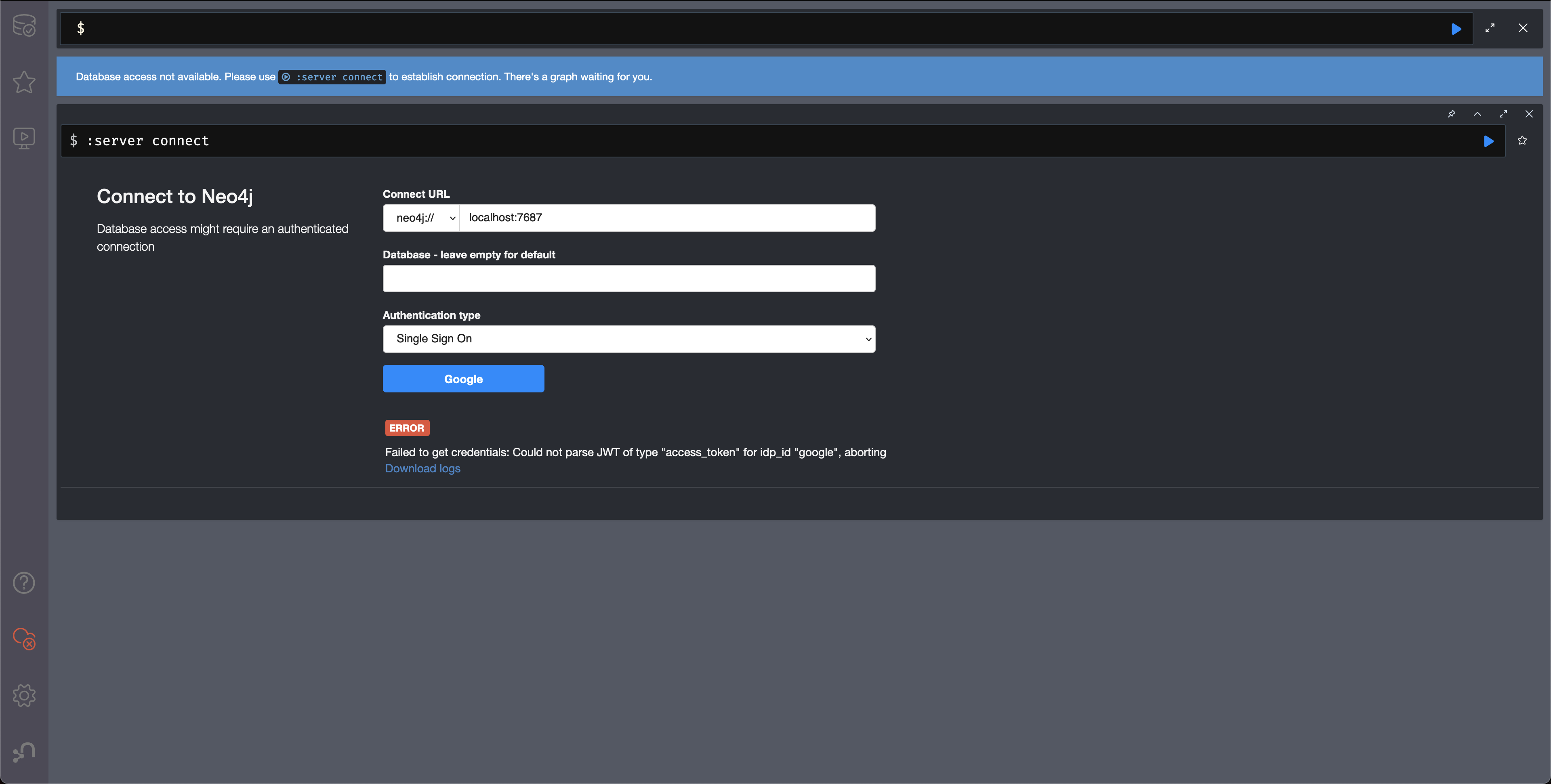
Change to ID tokens in your neo4j.conf:
dbms.security.oidc.{{provider}}.config=token_type_principal=id_token;token_type_authentication=id_tokenWhen should identity tokens vs. access tokens be used?
It is generally safer to use access tokens when possible due to being shorter-lived. If authorization permissions change on the identity provider, Neo4j will fail authorization. Neo4j Browser will try to reconnect and reflect the changed permissions faster than if ID tokens were used.
Debug logging of JWT claims
While setting up an OIDC integration, it is sometimes necessary to perform troubleshooting.
In these cases, it can be useful to view the claims contained in the JWT supplied by the identity provider.
To enable the logging of these claims at DEBUG level in the security log, set dbms.security.logs.oidc.jwt_claims_at_debug_level_enabled to true and the security log level to DEBUG.
|
Make sure to set dbms.security.logs.oidc.jwt_claims_at_debug_level_enabled back to |
How to debug further problems with the configuration
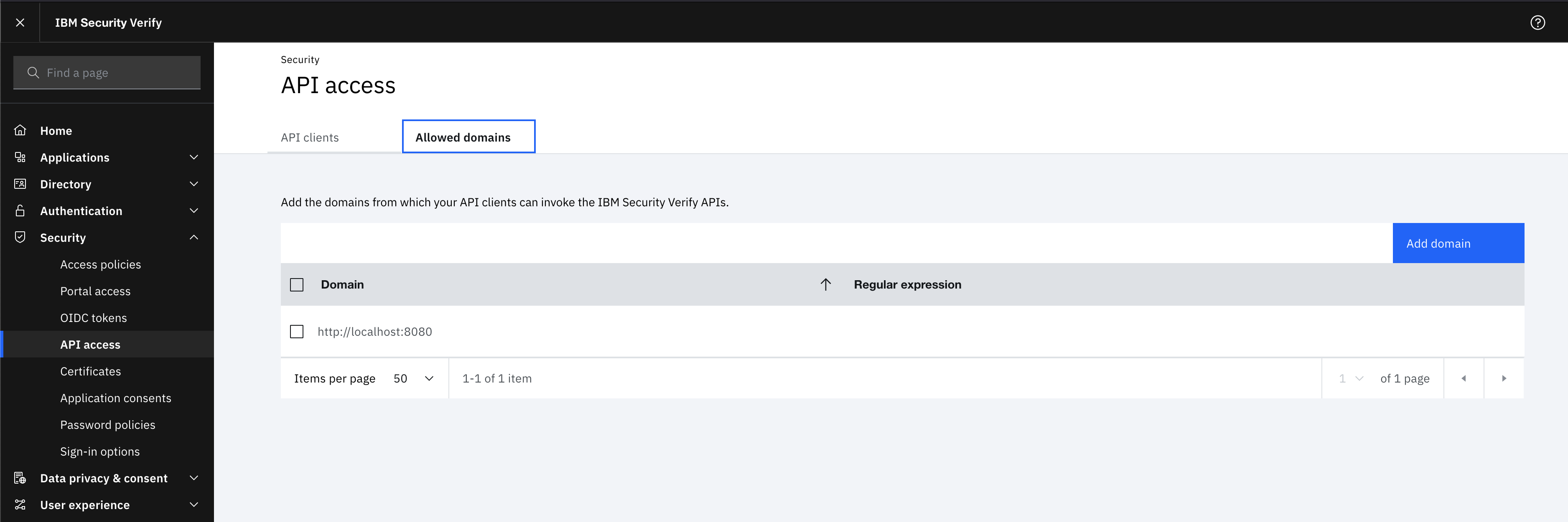
Apart from the logs available in logs/debug.log and logs/security.log in the Neo4j path, you can also use the web-development console in your web browser when doing the SSO authentication flow with Bloom or Neo4j Browser. This could reveal potential problems, such as the one presented below with an example identity provider and the Cross-Origin Request policy:
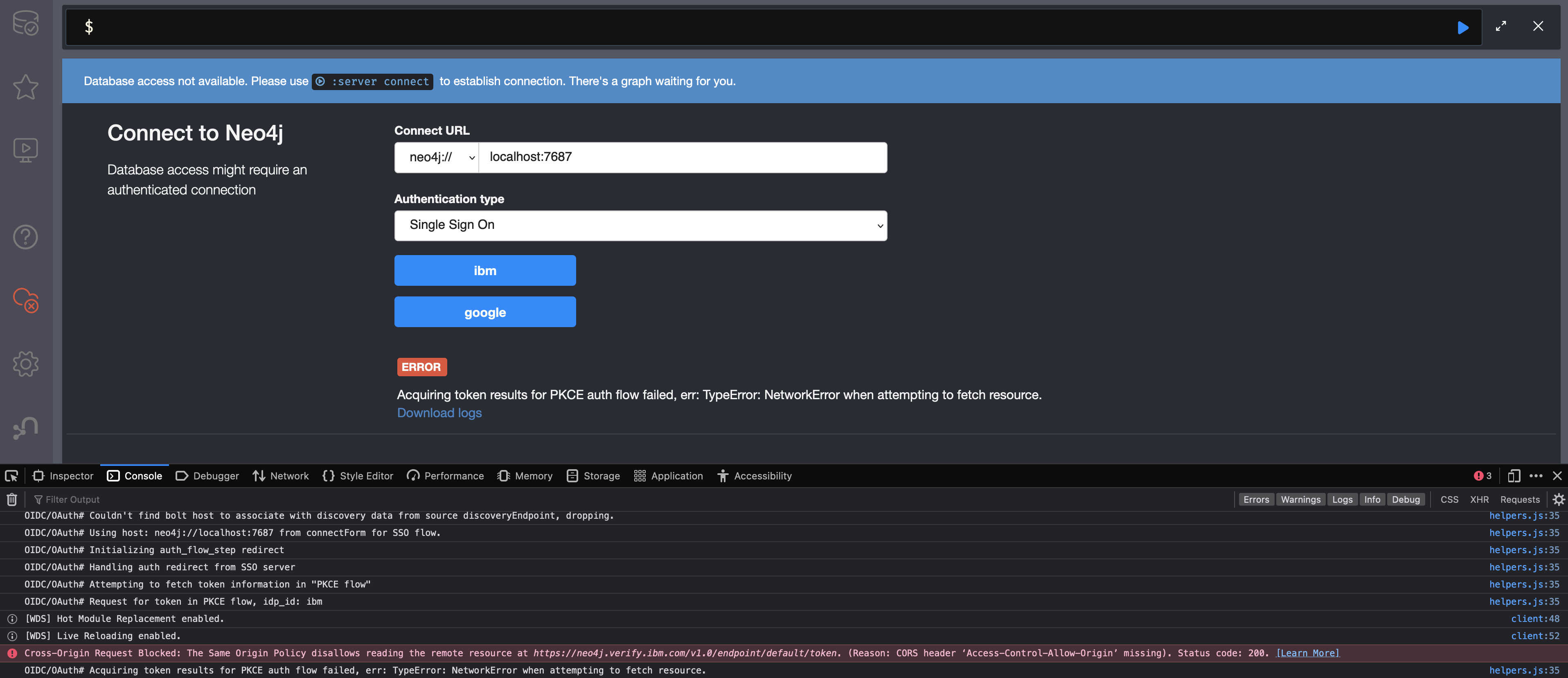
The solution involves adding the redirect domain to the list of allowed domains in the provider (in this case, localhost:8080):