Single Sign-On (SSO)AuraDB Business CriticalAuraDB Virtual Dedicated CloudAuraDS Enterprise
|
If you’re planning to use Single Sign-On (SSO), keep in mind that SSO does not retroactively apply to existing instances. It only applies to instances created after SSO is configured. Therefore, plan accordingly. |
Single Sign-On (SSO) enables organization owners and organization admins to use your organization’s identity provider (IdP) to authenticate users so they can access the Aura console and Aura instances.
Aura supports SSO authentication and authorization using Microsoft Entra and Okta as IdPs, implementing the OpenID Connect (OIDC) protocol.
As the service provider, Neo4j Aura redirects authentication requests to the configured IdP using the OpenID Connect (OIDC) protocol. Aura also supports authenticating with Google as the identity provider. When a user attempts to log in, Aura generates a redirect URL with authentication parameters and sends the user to the IdP for authentication. After successful authentication, the IdP redirects the user back to Aura with a secure token, allowing Aura to establish an authenticated session.
Required roles
The person setting up SSO needs an Organization Owner or Organization Admin role.
For information on how to assign roles see User management.
SSO levels
-
Use as a log in for the Organization: Login with SSO to the Aura console. Allows org admins to control how users log in when they are trying to access the organization.
-
Use as login method for instances with Projects in this Org: The SSO log in will be on the instances. Impacts new database instances created within that project. It ensures users logging in with SSO have access to the database instances within the project. It does not give access to edit the project settings, for example to edit the project name, network access, or to edit the instance settings such as to rename an instance, or pause and resume. It depends on RBAC if the user can access and view or modify data within the instances themselves. For this level, the role mapping may be used to grant users different levels of access based on a role in their IdP.
Log-in methods
Log-in methods are different for each SSO level. Administrators can configure a combination of one or more of the log-in methods.
Supported log-in methods at the organization-level:
-
Email/password
-
Okta
-
Microsoft Entra ID
-
Google SSO (not Google Workspace SSO)
At the organization-level, admins can disable email/password and Google SSO if one other custom SSO provider is configured.
Supported log-in methods at the project-level:
-
User/password
-
Okta
-
Microsoft Entra ID
At the project-level, admins cannot disable user/password.
Setup requirements
Accessing Aura with SSO requires:
Aura requires the Authorization Code Flow, an OAuth2 authentication method that involves redirecting users to a publicly accessible IdP server for login.
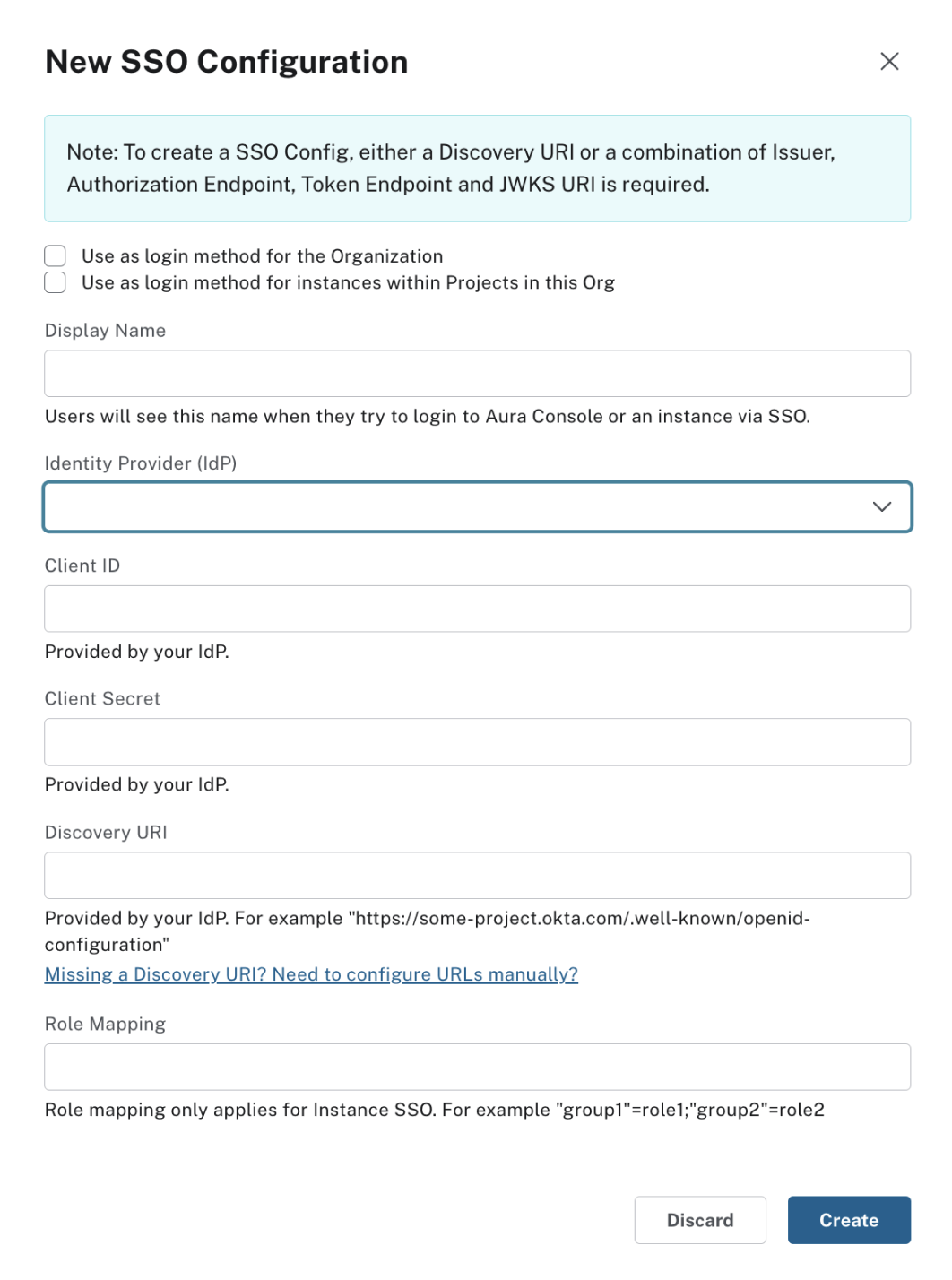
To create an SSO Configuration, either a Discovery URI or a combination of Issuer, Authorization Endpoint, Token Endpoint, and JWKS URI is required.
Create a new SSO configuration
-
Go to Organization > Security > Single Sign-On to set up a new SSO configuration.
-
The checkboxes Use as a log in for the Organization and Use as login method for instances with projects in this Org define whether SSO should be only on organization-level, only on project-level, or both.
-
The required basic SSO configuration information can be retrieved from the IdP. Entering the Discovery URI pre-fills the fields below. If this is not known these fields can be completed manually.
|
If you want users to authenticate with SSO for both the Aura Console and your database instances, make sure to select both of the following checkboxes during setup:
|
Log-in link
After setting up SSO, the Organization sso login link can be found in the organization summary page in the Aura console.
Role mapping
Role mapping links a user’s identity from an identity provider (such as Okta or Microsoft Entra ID) to a specific Aura role, based on attributes passed during authentication, like group or department.
When SSO is enabled at the project level, Aura uses role mapping to determine what access a user should have based on their IdP group membership.
This access then applies to all newly created instances the user has access to.
Instance-level SSO support
Customer support can assist with:
-
Adding SSO just for a specific instance
-
Updating SSO settings on existing instances
-
Role mapping specific IdP groups to a single database instance, instead of all instances which is the default behavior.
-
Creating custom claims beyond
groups
Ticket template
To request assistance, contact Support and raise a ticket using the following template:
Instance ID (Aura-only): [Insert]
Project ID (Aura-only): [Insert]
IdP name: [e.g., Okta, Azure]
SSO update for existing instance? Yes / No
Role mappings? Yes / No
If yes: [Insert details]
Custom claim? Yes / No
If yes: [Insert details]Instance ID (also known as DBID) can be found at instance details. Project ID can be found at project settings.
Microsoft Entra ID SSO
-
In the Azure Portal, go to App Registrations and then New Registration.
-
Add a name for the new app registration and select Register. Skip redirect URI’s for now.
-
On the app overview page, take note of the Application (client) ID.
-
Select the Client Credentials link to open the client credentials page.
-
Create a new secret and copy the Value field, it won’t be visible after leaving the page.
-
Go back to the App Overview page and open the App Endpoints and take note of the OpenID Connection metadata document URI
-
Under Authentication in the left-hand navigation, setup redirect URLs:
-
Adding a new Web platform
-
Enter
https://login.neo4j.com/login/callbackas the redirect URI.
-
-
In the Aura console, go to Organization > Security > Single Sign On > New configuration
-
Select how you want the SSO configuration to be applied in Aura:
-
Use as a log in method for the organization applies to organization-level logins (which acts as a login to the Aura console).
-
Use as a login method for instances within Projects in this Org applies to the project-level and you can select specific projects within the organization (where login is on the instance).
-
Or, select both.
-
-
For IdP Type select Microsoft Entra ID.
-
For Client ID enter the Application (client) ID from the Azure app.
-
For Client Secret enter the client secret value (not secret id) from the secret you created in the Azure app.
-
For Discovery URI enter the OpenID Connect metadata document URI.
-
Configure any additional settings as needed:
-
For organization-level SSO, no additional settings needed.
-
For project-level SSO, enter role mappings if applicable.
-
-
Select Create.
-
Select the additional log in methods:
-
For Organization-level testing it is recommended to keep the Email/password or Google log-in method enabled, so that if SSO fails, you can still access the Aura console and adjust the configuration.
-
For Project-level testing the user/password login is always available on the instance, so if SSO isn’t working, the instance is still accessible.
-
Token request scopes
When requesting the token from Azure, the scopes Aura sends are:
-
openidaccess to a unique identifier to identify the user. -
profileaccess to basic profile information. -
emailcontains the user’s email address.
This will result in Azure asking for consent to display details related to these scopes. For more information, see OpenID Connect Scopes
Okta SSO
-
In the Okta admin portal go to Applications and then Create App Integration.
-
For Sign-in method select OIDC - OpenID Connect.
-
For Application type select Web Application.
-
Select Next.
-
For Grant type select Authorization Code.
-
For Sign-in redirect URIs add https://login.neo4j.com/login/callback as the redirect URI.
-
Save.
-
In the Aura console, go to Organization > Security > Single Sign On > New configuration.
-
Select how you want the SSO configuration to be applied in Aura:
-
Use as a log in method for the organization applies to organization-level logins (which acts as a login to the Aura console).
-
Use as a login method for instances within Projects in this Org applies to the project-level and you can select specific projects within the organization (where login is on the instance).
-
Or, select both.
-
-
For IdP Type select Okta.
-
For Client ID enter the Okta Client ID.
-
For Client Secret enter the Client Secret.
-
Select discovery method:
-
For Discovery URI take the domain from your Okta portal which should be something like https://dev-123-admin.okta.com/ and add
.well-known/openid-configuration. The final URL should look similar tohttps://dev-123-admin.okta.com/.well-known/openid-configuration. -
Alternatively, you can select Manual Configuration and enter the values separately, including Issuer, Authorization Endpoint, Token Endpoint and JWKS URI.
-
-
Configure any additional settings as needed:
-
For organization-level SSO, no additional settings needed.
-
For project-level SSO, enter role mappings if applicable.
-
-
Select Create.
-
Select the additional log in methods:
-
For Organization-level testing it is recommended to keep the Email/password or Google log-in method enabled, so that if SSO fails, you can still access the Aura console and adjust the configuration.
-
For Project-level testing the user/password login is always available on the instance, so if SSO isn’t working, the instance is still accessible.
-
FAQ
Can users get roles added to them in Aura console via SSO and a group to role mapping?
No, users must be granted the role on the organization via Aura console invites and access management like with any other organization.
Why am I unable to connect to the instance after completing the SSO login, the connection is showing as unconnected?
Ensure that the email field is provided on your user in Microsoft Entra ID. If it already is, contact support for further assistance.