Beyond the Patching Treadmill with Exposure Management
1. The Problem Domain: Vulnerability Fatigue
Modern enterprises are drowning in security alerts. Traditional Vulnerability Management (VM) relies on flat lists and spreadsheets, often leading to "CVSS Fatigue"—a state where everything is labeled "Critical," yet resources to fix them are limited.
-
Lack of Context: A
CRITICALvulnerability on an isolated, air-gapped server is treated with the same urgency as one on an internet-facing gateway. -
Static Scoring: CVSS scores tell you how "bad" a bug is in a vacuum, but not how "dangerous" it is to your specific business.
-
Siloed Data: Infrastructure teams, AppSec teams, and Cloud Architects work in different tools, making it impossible to see how a single library flaw could lead to a "Crown Jewel" data breach.
2. The Solution: Vulnerability Prioritization and Exposure Management (VPEM)
Neo4j transforms reactive patching into proactive Exposure Management. By building a Security Knowledge Graph, organizations can unify disparate data sources into a single, navigable map of their digital estate.
The VPEM approach integrates: 1. Infrastructure Data: Compute instances, S3 buckets, and Network Interfaces. 2. Software Supply Chain: Applications, Libraries (SBOMs), and Build Artifacts. 3. Threat Intelligence: Real-time feeds like the CISA KEV (Known Exploited Vulnerabilities). 4. Identity & Access (IAM): The "connective tissue" that determines what an attacker can actually do once they are inside.
3. The Graph Advantage: Seeing the Paths, Not Just the Points
Relational databases struggle with deep path analysis. Neo4j excels at it. By modeling security data as a graph, security architects and CTOs gain three distinct advantages:
3.1. 1. Reachability Analysis
Is the vulnerable library actually reachable? If a server has a critical CVE but no PUBLIC_IP and no RESOLVES_TO relationship from an external endpoint, the immediate risk is lowered.
3.2. 2. Blast Radius & Impact Analysis
If an attacker exploits an Application, what can they access? By traversing the relationship (:Identity)-[:ASSUMES]→(:IAMPolicy)-[:HAS_ACCESS_TO]→(:CloudService), Neo4j can instantly identify if a vulnerability provides a path to sensitive PII or financial databases.
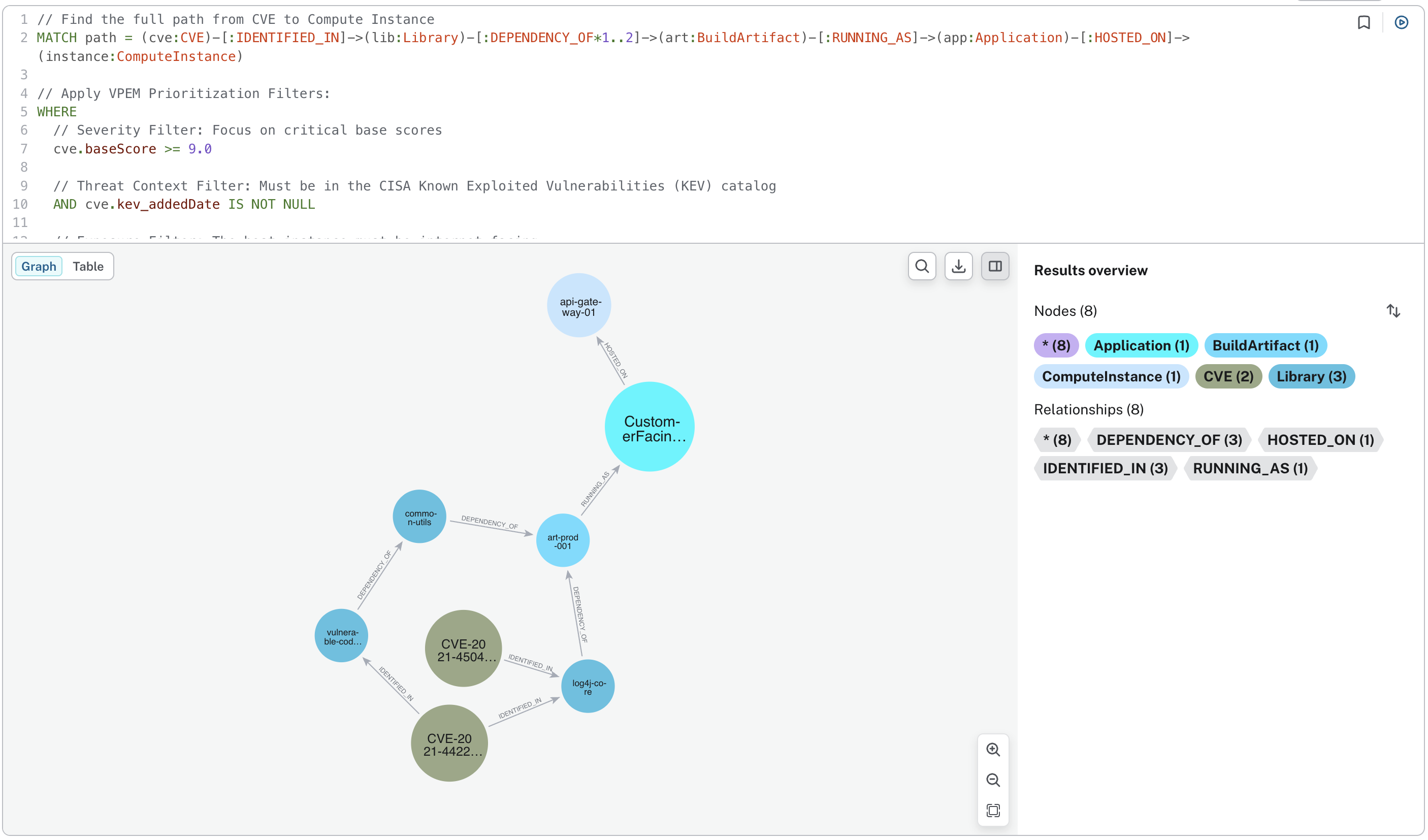
3.3. 3. Strategic Remediation
Instead of fixing 1,000 disconnected bugs, the graph identifies Choke Points. Upgrading one single Library might remediate the highest aggregate risk across the entire production environment.
3.4. The VPEM Schema
The power of this solution lies in its extensible schema, connecting code to cloud.
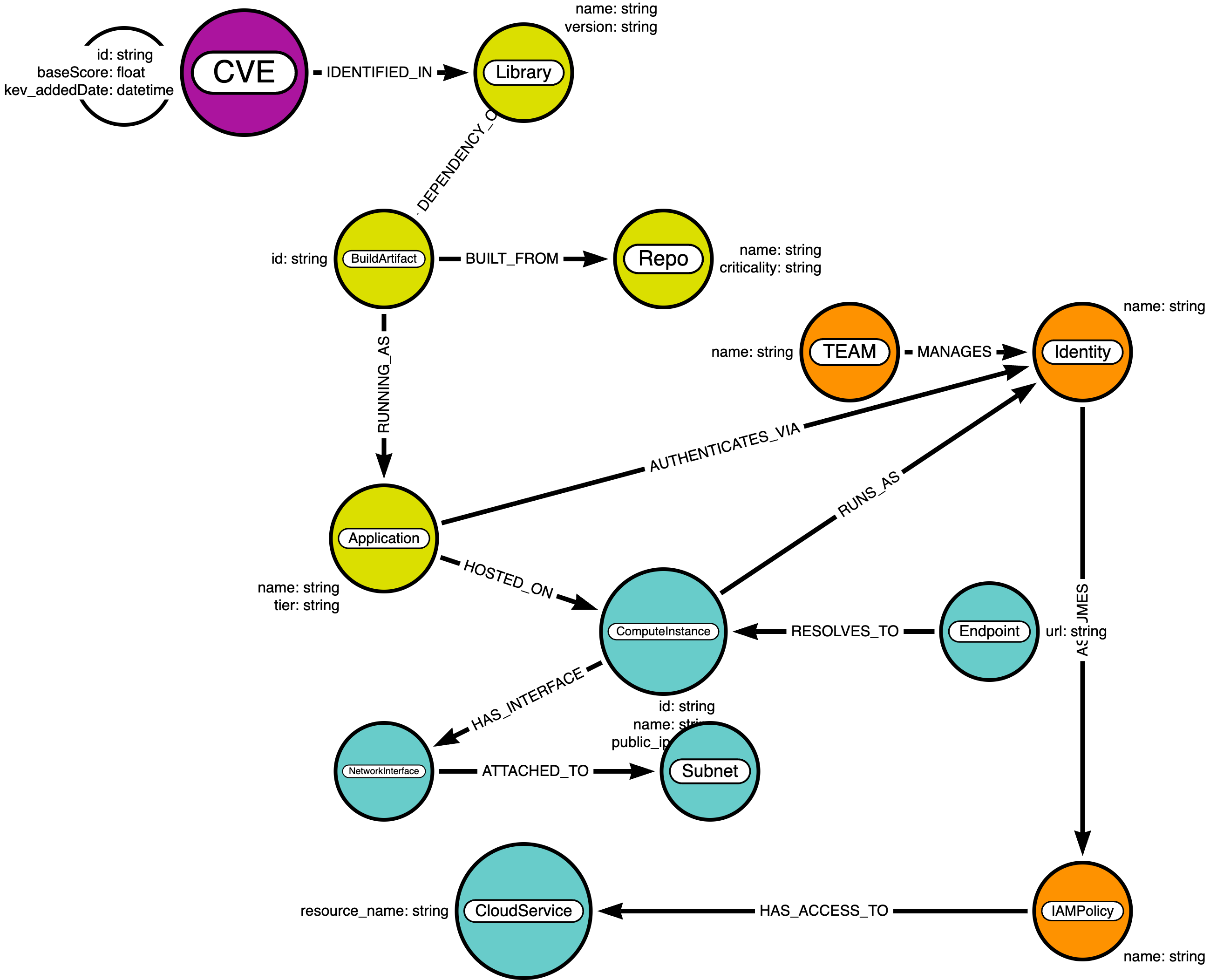
| Relationship | Business Value |
|---|---|
|
Links CVEs directly to specific Products and Vendors. |
|
Connects the Application layer to Identity, exposing lateral movement risks. |
|
Cross-references internal bugs with the CISA KEV to prioritize "in-the-wild" threats. |
4. Next Steps: Moving Toward Maturity
Transitioning to a graph-based security posture allows organizations to move from "Patching Everything" to "Fixing What Matters."
-
Assess your SBOMs: Start by ingesting your Software Bill of Materials into Neo4j.
-
Map your Attack Paths: Use our Attack Path Analysis (APA) framework to simulate adversary movement.
-
Automate Remediation: Integrate Neo4j with Jira or GitHub Actions to create tickets only for vulnerabilities that have a verified
CAN_REACHpath to critical assets.
For a deep dive into the implementation, explore the loader.ipynb and vpem.ipynb notebooks in the Cyber-VPEM Repository.