Fraud Detection Using Graph Technology

Content Manager, SpringPeople
4 min read

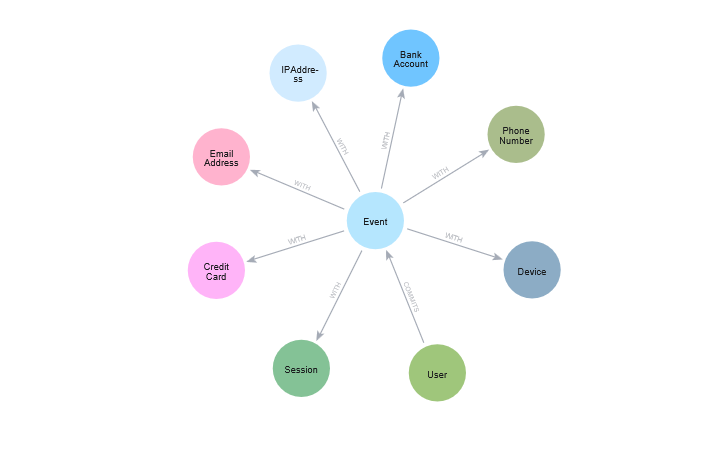
Graph technology refers to the storage, management and querying of data graphical representation. Here, your indices become vertices and your relationships are converted into edges. Through analysis of the fine-grained relationships, by using graph analysis, you can find out oddities with the help of algorithms and queries.
A primary advantage of graph databases is that they are indexed naturally by relationships. With graph technology, users are able to include data without having to do much modeling in advance. All of this makes graph technology very useful for keeping up with the deception and speed of fraudsters.
Anomaly Detection with Graph
In fraud detection, usually analysis is categorized in two ways: discrete and connected data analysis.
In discrete data analysis, individual actions, users and accounts are evaluated. Whereas in connected data analysis, integrated behaviors and relationships help in detecting the fraud. Graph modeling and analysis especially proves beneficial for connected data analysis.
With the help of connected data and graph technology, users are empowered to:
- Merge and correlate information on organizations
- Project the results like a connected graph
- Discover insights by applying social network and link
Now, let’s see how enterprises can employ connected data analysis to resolve real-world business issues.
Locating Bot Accounts in Social Media Networks
Social media is increasingly influencing today’s world and marketers are busy needling out the latest trends from this platform.
For instance, if selling a specific product, they’ll want to estimate what is popular in that product category. Marketers want to know how their product stands as compared to their competitors, public perception about their product and what people are saying about them in social media.
This kind of information is extremely valuable. However, it’s useless if the data is incorrect or altered by the amount the company’s competitors are ready to spend on bots. Fake bots give skewed details regarding popularity. To boost the popularity of some target accounts, these bots will retweet them.
In order to correctly find out the authenticity of these accounts, a given user can depict a graphical representation of the accounts, with retweet counts as the edge weights, to accurately determine the number of times these accounts retweet their neighboring accounts.
Here, marketers can clearly see that popular accounts show different features from unnaturally popularized accounts.
During analysis of these accounts, we can see some accounts with unnatural deviation. It is possible to find more bots by using graphs and relationships in these ways:
- Identifying accounts with a large retweet count
- Determining the way in which other account retweets them
- Locating accounts that are retweeted only from these bots
Circular Payment
Circular money transfer is one common pattern that is traceable in most financial crimes. In this pattern, the person sends money to themselves and conceals it as a legitimate money transfer between “normal accounts.” These accounts are, in fact, fake accounts.
Usually, they share certain details as they are created from stolen identities (email addresses and similar info). This kind of information makes graph analysis the perfect tool to locate them.
In this kind of use case, graphic representation can be created by depicting a graph from transitions between entities that share certain details like addresses, passwords, email addresses and the like. After a user creates a graph using this information, all that is left is to write a basic question and run it to search for people with accounts featuring similar kinds of details.
Financial Fraud and Money Laundering
In money laundering, dirt money is circulated around in order to jumble it with real, legitimate money, which is then converted to hard assets. These types of tax-evading schemes depend on brokers and false resellers who apply for tax refunds that enable them to get around payment.
Using a graph database gives users relationship models that let the user apply classification, machine learning, pattern recognition and statistical analysis to these models for a more effective examination, at scale, against big volumes of data sets.
Let’s Look at Case Correlation
When transactions are made that, according to regulations, are deemed suspicious, they get a close examination by investigators. The primary aim in this case is to ensure each and every individual activity is subjected to separate investigation, rather than all the suspicious activities grouped together according to connections that are known beforehand.
To determine these correlations with the help of a graph-based technique, users can implement this flow with the help of common graph machines, as well as with connected component graph algorithms with filters and patterns matching query (path finding).
When a company uses this method, they are freed from having to build their customized case correlation engine. Instead, they could employ graph technology that has enhanced flexibility.
Conclusion
Without any doubt, scammers today are getting more advanced. However, technology is also not behind in this race. Technologies like a graph database are a good way to find truth from data. Globally, this technology has been gradually gaining relevance and is an important tool for all business.