Build a Private Network Path to Aura on AWS, Azure, and Google Cloud Using Terraform

Technical Support Engineer at Neo4j
7 min read
A Neo4j Aura instance can be publicly available, completely private, or configured to allow both public and private access.
Using secure connections on Aura is important for:
- Data protection: Secure connections help protect data in transit from being intercepted or tampered with. This is particularly crucial when dealing with sensitive information.
- Performance: By routing traffic through private network paths within your virtual private cloud (VPC), you eliminate unnecessary internet hops, reducing query latency and improving throughput.
For more information about secure connections and network access configurations, refer to Aura Secure Connections.
This blog demonstrates how to configure private connectivity to Aura using Terraform, an open-source Infrastructure as Code (IaC) tool.
Terraform allows you to define, version, and automate cloud infrastructure through code.
Prerequisites
- Terraform (v1.3 or higher)
- Neo4j AuraDB/AuraDS Virtual Dedicated Cloud (VDC) account
- Access to the cloud console and permissions to create networking resources
- Optional: CLI authentication (
az login,aws configure,gcloud auth login)
Cloud-Specific Implementations
Each cloud has a different mechanism for achieving private connectivity, but the goal is the same: Route all traffic privately between your environment and Aura.
Below, you’ll find the minimum Terraform configuration required for each platform, along with a GitHub repository for each cloud provider that includes a full template for provisioning all the necessary resources.
Follow the steps in Aura Secure Connections to create the New network access configuration.
AWS PrivateLink
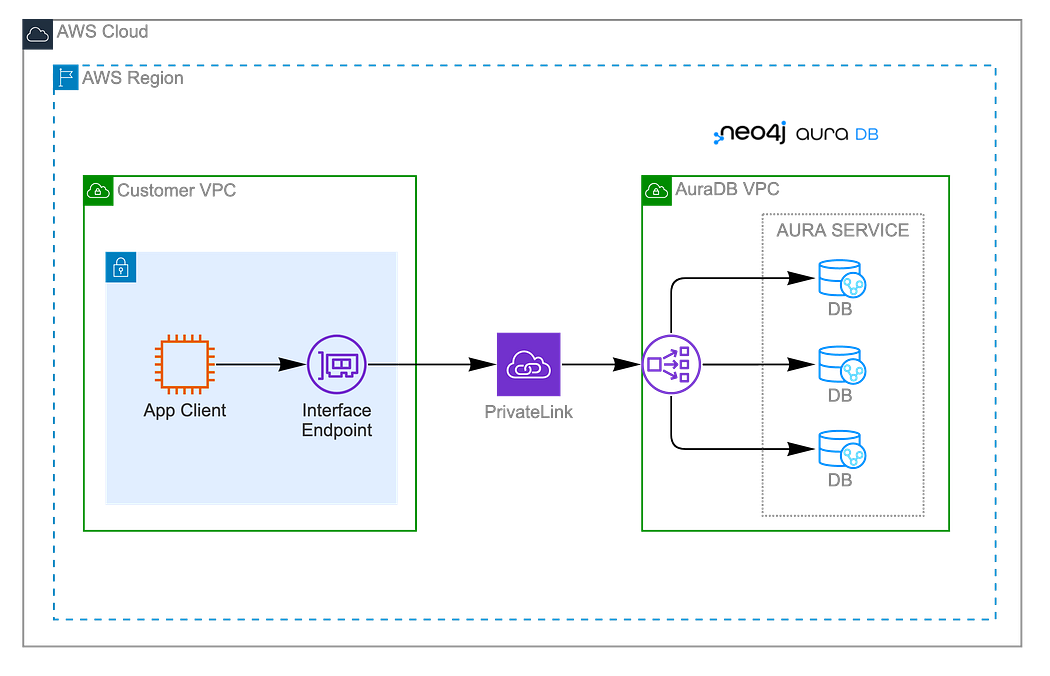
Requirements
- Existing
vpc_idandsubnet_ids - Security group that allows inbound traffic on ports 80, 443, and 7687
Security group:
resource "aws_security_group" "aura" {
name = "aura-privatelink-endpoint"
description = "SG for Neo4j Aura PrivateLink endpoint"
vpc_id = var.vpc_id
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
}
resource "aws_vpc_security_group_ingress_rule" "http" {
security_group_id = aws_security_group.aura.id
cidr_ipv4 = var.vpc_cidr
from_port = 80
to_port = 80
ip_protocol = "tcp"
}
resource "aws_vpc_security_group_ingress_rule" "https" {
security_group_id = aws_security_group.aura.id
cidr_ipv4 = var.vpc_cidr
from_port = 443
to_port = 443
ip_protocol = "tcp"
}
resource "aws_vpc_security_group_ingress_rule" "bolt" {
security_group_id = aws_security_group.aura.id
cidr_ipv4 = var.vpc_cidr
from_port = 7687
to_port = 7687
ip_protocol = "tcp"
}PrivateLink Endpoint:
resource "aws_vpc_endpoint" "aura" {
vpc_id = var.vpc_id
service_name = var.service_name # e.g. "com.amazonaws.vpce.us-east-1.vpce-svc-0a0b02030n1n2j3k4h"
vpc_endpoint_type = "Interface"
private_dns_enabled = var.enable_private_dns
subnet_ids = var.subnet_ids
security_group_ids = [aws_security_group.aura.id]
}The Endpoint Service Name is displayed under the second step when creating a Private Endpoint Connection in the Aura Console.
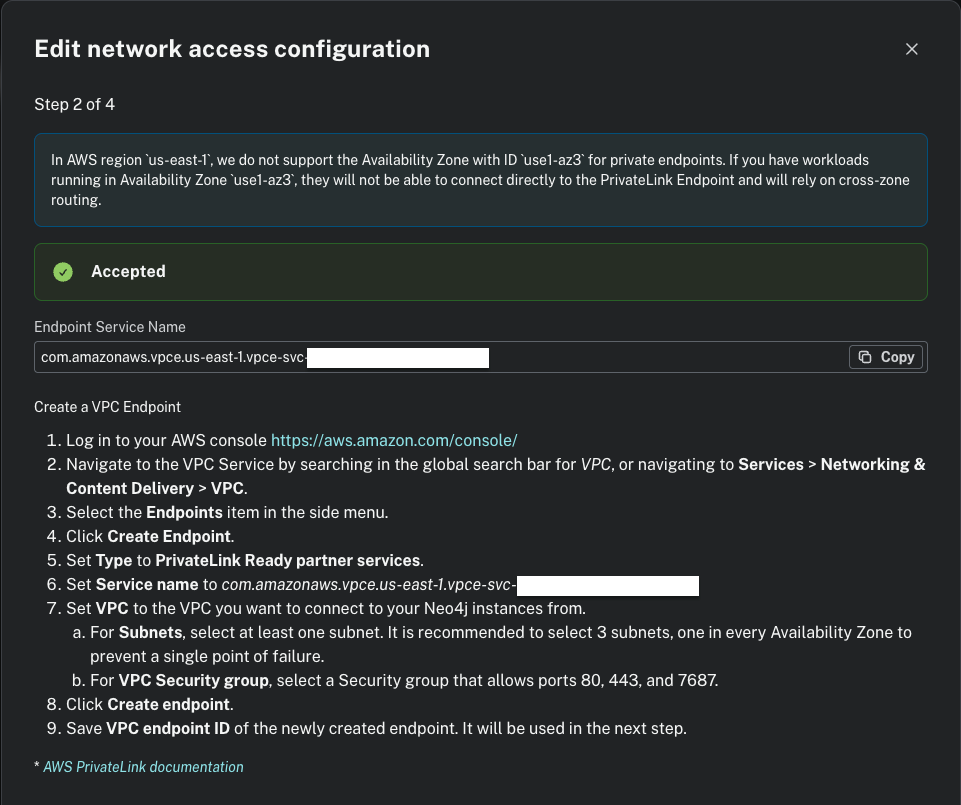
The private link enablement in AWS requires a two-step DNS setup because the endpoint connection needs to be accepted by Aura. Follow these steps:
- Apply
enable_private_dns = falsein the terraform.tfvars - Create the resources with terraform apply -auto-approve
- Accept the endpoint in the Aura console: Project > Settings > Private Endpoints > Next until you reach step 3 > Accept the new Endpoint Connection Requests
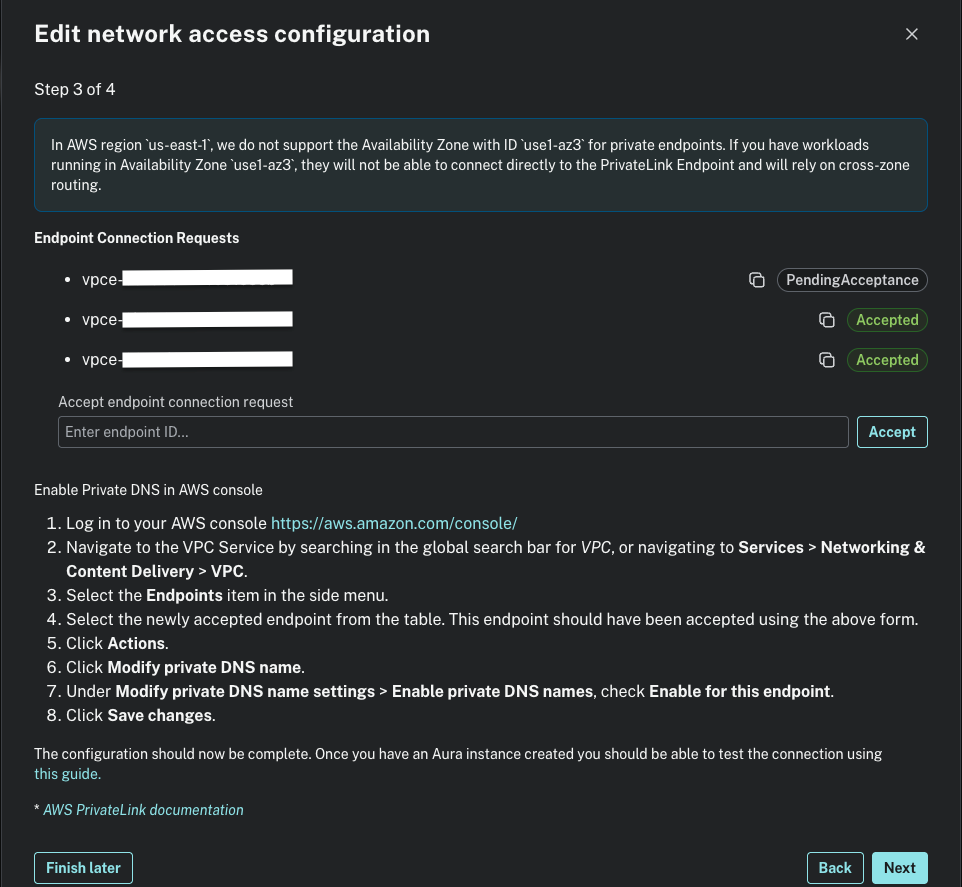
4. Change the enable_private_dns = true in the terraform.tfvars and run terraform apply -auto-approve
5. Test connectivity through the private endpoint
Azure Private Link
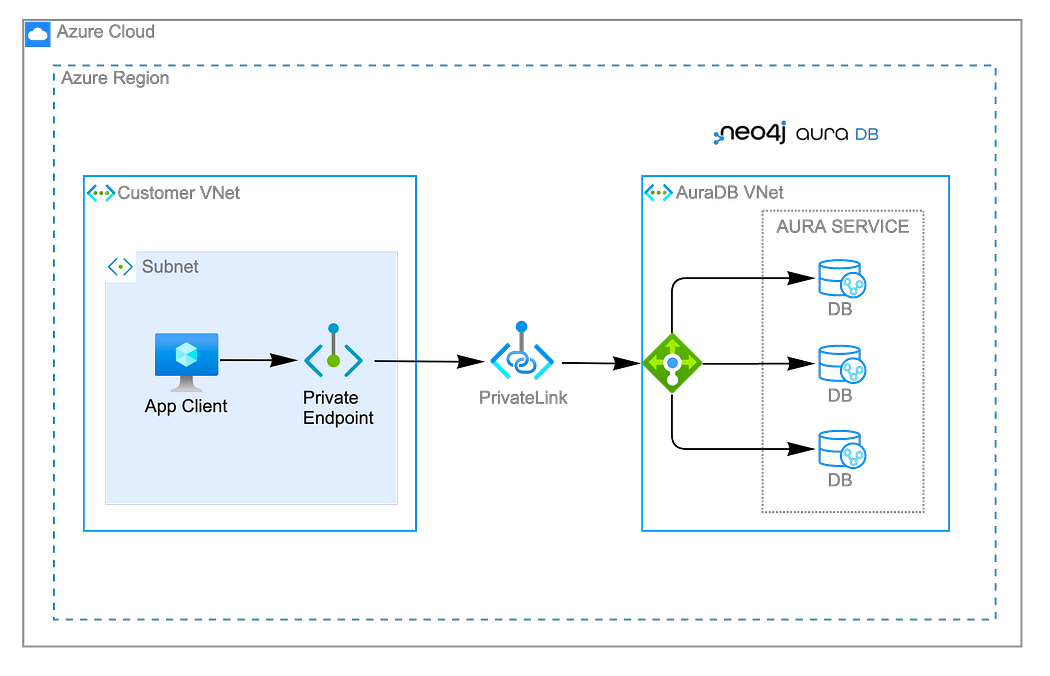
Requirements
- Resource group name and location
- Existing subnet ID
- VNet ID
- Aura Private Link service name
- Private DNS zone name
Private endpoint:
resource "azurerm_private_endpoint" "aura" {
name = "pep-neo4j-aura"
location = var.location
resource_group_name = var.resource_group_name
subnet_id = var.private_endpoint_subnet_id
private_service_connection {
name = "pep-neo4j-aura-connection"
is_manual_connection = true
private_connection_resource_alias = var.aura_private_link_service_alias
request_message = "Private endpoint request from Aura"
}
}The PrivateLink Service Name used under aura_private_link_service_alias can be achieved on the Aura console > Project > Settings > Private Endpoints > Next until you reach step 2.
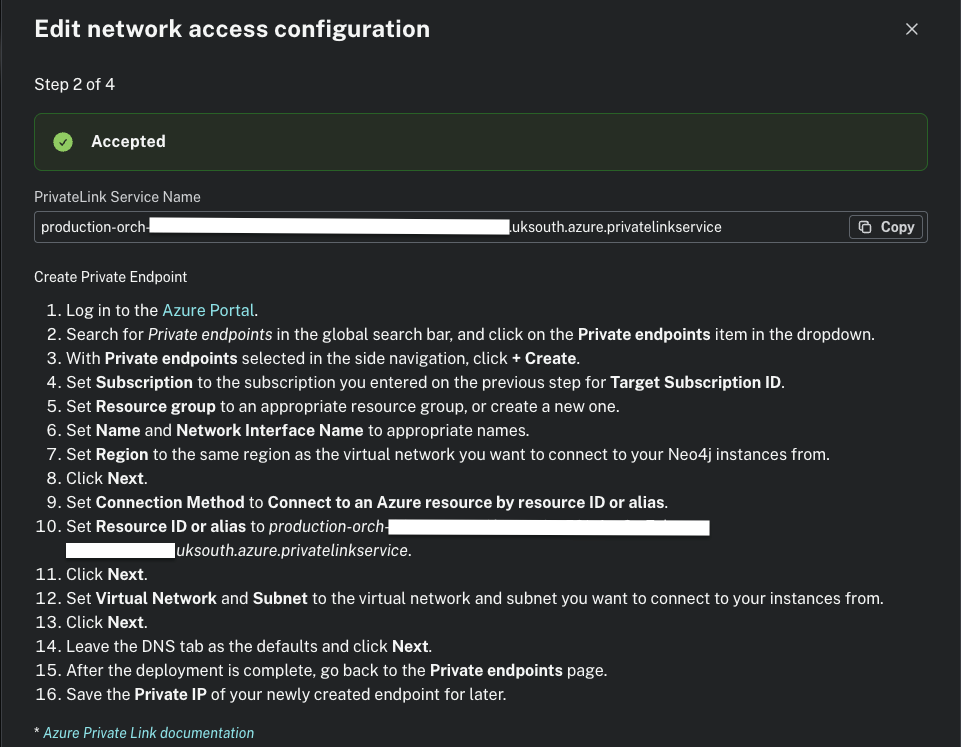
Private DNS zone and wildcard record:
resource "azurerm_private_dns_zone" "aura" {
name = var.private_dns_zone_name
resource_group_name = var.resource_group_name
}
resource "azurerm_private_dns_a_record" "aura" {
name = "*"
zone_name = azurerm_private_dns_zone.aura.name
resource_group_name = var.resource_group_name
ttl = 300
records = [azurerm_private_endpoint.aura.private_service_connection[0].private_ip_address]
depends_on = [azurerm_private_endpoint.aura]
}
resource "azurerm_private_dns_zone_virtual_network_link" "aura" {
name = "dns-link-neo4j-aura"
resource_group_name = var.resource_group_name
private_dns_zone_name = azurerm_private_dns_zone.aura.name
virtual_network_id = var.vnet_id
registration_enabled = false
depends_on = [azurerm_private_dns_zone.aura]
}The above DNS zone and wildcard record creation are required for network reachability, as described in Neo4j support and in the Neo4j documentation.
After planning and applying the Azure resources, the last step is to accept the Endpoint Connection Requests by accessing the Aura console > Project > Settings > Private Endpoints > Next until you reach step 3.
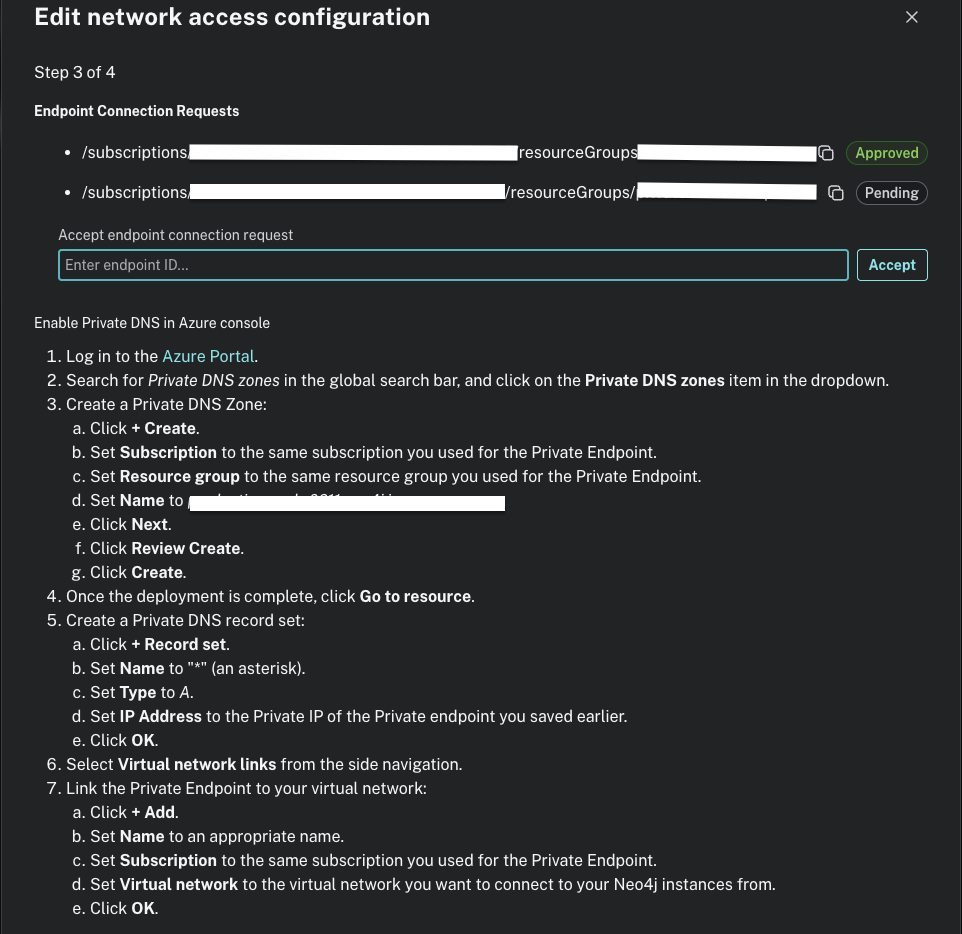
Once the Endpoint Connection Request changes to Approved, test connectivity through the private endpoint.
Google Cloud Private Service Connect
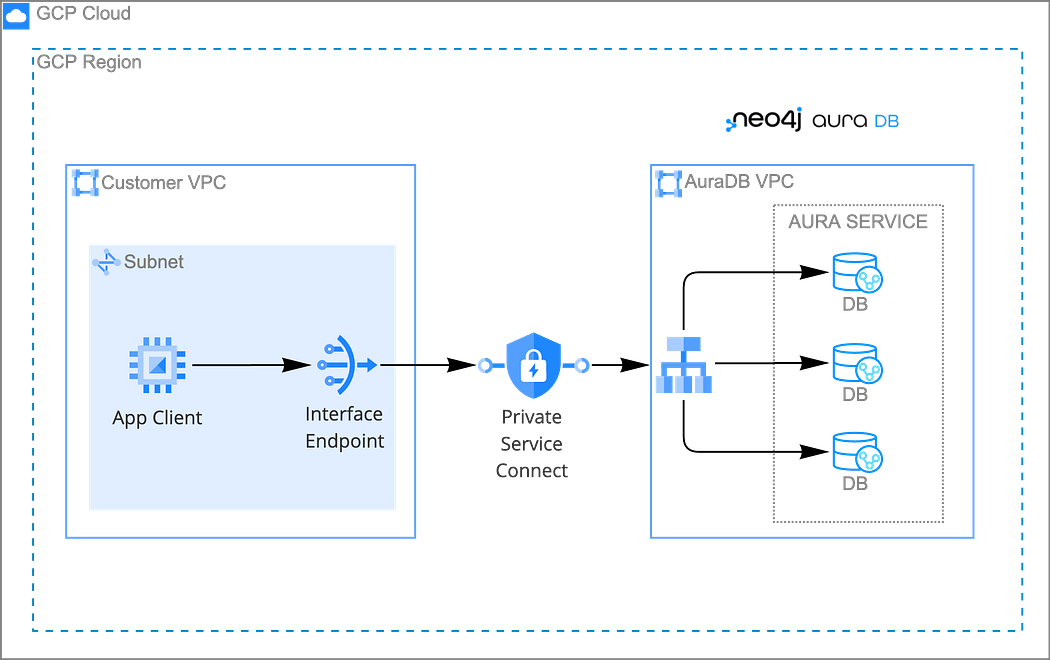
Requirements
- Existing VPC and subnet in the same region as the Aura service attachment
- Aura’s
serviceAttachmentURL - Aura’s FQDN for DNS override
Enable APIs and reserve internal IP:
resource "google_project_service" "compute_api" {
project = var.project_id
service = "compute.googleapis.com"
}
resource "google_project_service" "dns_api" {
project = var.project_id
service = "dns.googleapis.com"
}
resource "google_compute_address" "psc_ip" {
name = "psc-endpoint-ip"
region = var.region
address_type = "INTERNAL"
purpose = "GCE_ENDPOINT"
subnetwork = <YOUR_SUBNETWORK_SELF_LINK>
}PSC forwarding rule and DNS response policy:
resource "google_compute_forwarding_rule" "psc_endpoint" {
name = "psc-endpoint-aura"
region = var.region
network = <YOUR_VPC_ID>
subnetwork = <YOUR_SUBNETWORK_SELF_LINK>
ip_address = google_compute_address.psc_ip.self_link
load_balancing_scheme = ""
target = var.aura_service_attachment
}
resource "google_dns_response_policy" "neo4j_policy" {
response_policy_name = "neo4j-aura-policy"
networks {
network_url = google_compute_network.vpc.id
}
depends_on = [google_project_service.dns_api]
}
resource "google_dns_response_policy_rule" "neo4j_rule" {
response_policy = google_dns_response_policy.neo4j_policy.response_policy_name
rule_name = "neo4j-aura-localdata"
dns_name = var.aura_fqdn
local_data {
local_datas {
name = var.aura_fqdn #e.g. "*.production-orch-xxxx.neo4j.io."
type = "A"
ttl = 300
rrdatas = [google_compute_address.psc_ip.address]
}
}
}The Aura Service Attachment URL used on var.aura_service_attachment and the FQDN used for var.aura_fqdn can be acquired while setting up the Private Endpoint in the Aura console > Project > Settings> Private Endpoints > Next until you reach step 2.
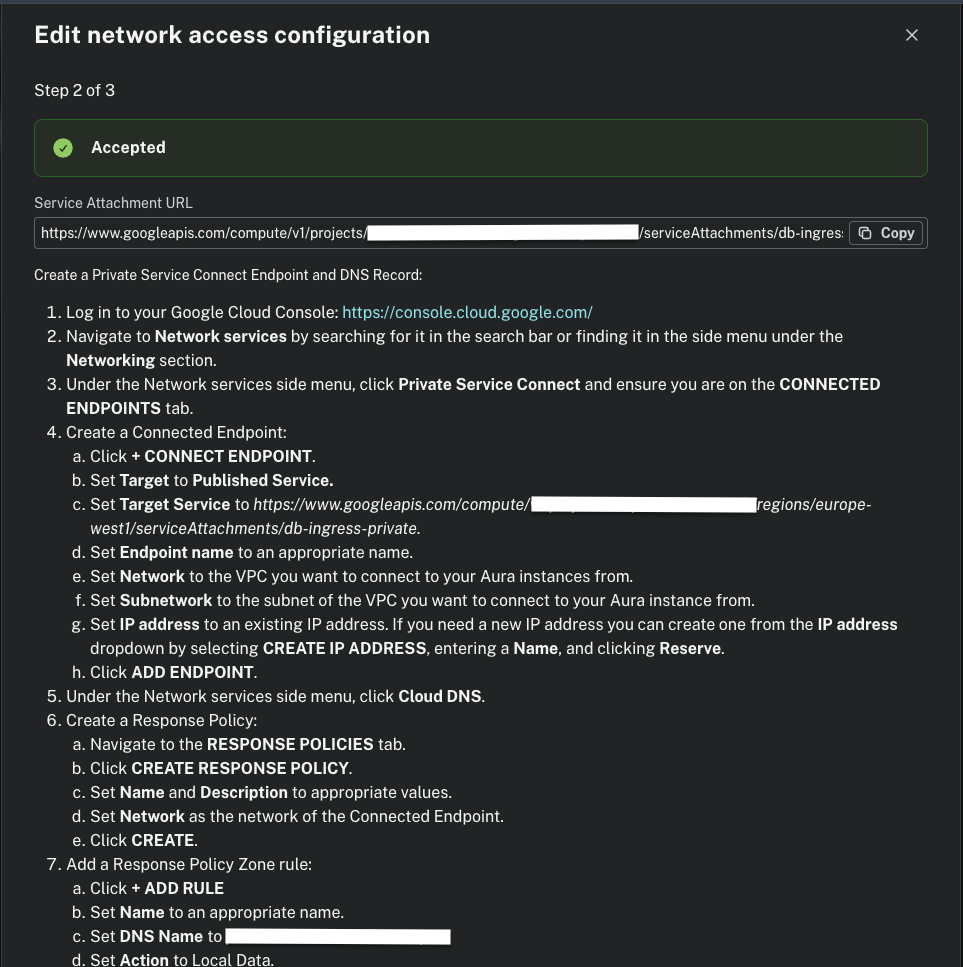
After all resources are created, test connectivity through the private endpoint.
Summary
Secure connections help protect data in transit from being intercepted or tampered with. And by routing traffic through private network paths within your virtual private cloud (VPC), you eliminate unnecessary internet hops, reducing query latency and improving throughput.
We’ve demonstrated how to configure private connectivity to Aura on AWS, Azure, and Google Cloud using Terraform, an open-source IaC tool.