
Top 10 Graph Database Use Cases (With Real-World Case Studies)
21 min read
Neo4j as an Embedded Database: The Key Use Cases of Graph Databases
7 min read
Top 10 Use Cases: Identity and Access Management
4 min read
Identity and Access Management: 5-Minute Interview with Seyed Hossein Ahmadinejad
1 min read
Using GraphQL for Digital Identity & Access Management
14 min read

Connecting the Complexity of Identity and Access Management
4 min read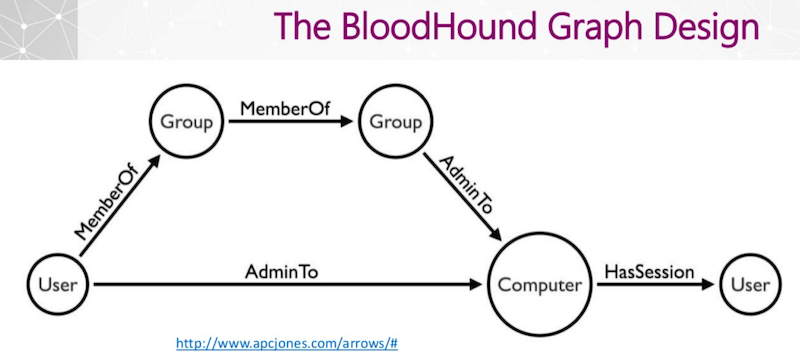
BloodHound: How Graphs Changed the Way Hackers Attack
15 min read