Role-Based Access Control in Neo4j Enterprise Edition [Security Series, Part 1]

Director of Product Management
3 min read
Neo4j has broken new ground in database applications with the introduction of the native graph database and the dominant labeled property graph model.
As Neo4j has matured, it has inevitably found its way into demanding enterprises who value security alongside the productivity benefits of the graph data model. As such, Neo4j’s security engine and surface have been completely revamped in the latest release.
In this series on database security and access control, we’ll explore all of the different facets and features available in Neo4j Enterprise Edition to keep your data secure. This week, we’ll take a closer look at role-based access control in Neo4j.
An Introduction to Security & Access Control in Neo4j
As we add new functionality to Neo4j, we make sure that database security and access controls keep pace with our advances in our graph query language, graph visualization, performance and usability.
Why is this so important? Because as technology solutions move increasingly into the public cloud, every organization wants the confidence of knowing their data is both protected from unauthorized users and easily accessible to authorized users under their existing security regime. CIOs regularly cite Enterprise Security and Cloud solutions as top priorities, and they are expected to hold that opinion for years to come.
Robust security starts with doing the little things right. For many years, Neo4j has required users to change their default password when they first login. In previous versions of Neo4j, developers could only access Neo4j data through REST/HTTP(s) endpoints. For this reason, we introduced server-side plugins called server authorization rules to enforce authentication and authorization of those endpoints.
For example, using server authorization rules, our partners at GraphAware built a production-ready integration of Spring Security and Neo4j.
The Enterprise Edition of Neo4j raises the bar for safeguarding data and meeting compliance requirements. It supports the concept of multiple users and a new role-based access control framework. It also introduces an LDAP connector for integrating with Active Directory or openLDAP services. Finally, Neo4j 3.1 debuts a new plugin architecture for building and deploying your own authentication and authorization controls. We’ll explore most of these features in the coming weeks.
Let’s take a closer look at role-based access control.
Role-Based Access Control
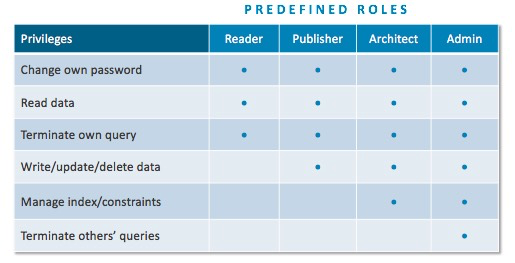
Neo4j 3.1 Enterprise Edition supports multiple users and adds a role-based access control (RBAC) framework with four predefined graph-global data-access roles: reader, publisher, architect and admin. Each role includes a set of authorized actions (read, write, etc.) permitted on the Neo4j data graph and its schema.
| Role | Privileges |
|---|---|
| reader | Read-only access to the data graph (all nodes, relationships and properties) |
| publisher | Read-write access to the data graph |
| architect | Read-write access to data graph and set/delete access to indexes and any other future schema constructs |
| admin | Read-write access to data graph and set/delete access to indexes and any other future schema constructs and view/terminate queries |
Users with no assigned roles have no data graph access, not even read privileges. Users assigned more than one role have a union of all privileges for those roles.
Neo4j includes pre-built support for three different authentication and authorization options:
- Built-in native users repository (enabled by default)
- LDAP connector to Active Directory or openLDAP
- Custom authentication/authorization provider plugin(s)
More granular permissions are readily supported via User-Defined Procedures.
Conclusion
This has been a brief overview of the new role-based access control features in Neo4j Enterprise Edition. In the coming weeks, we’ll take a closer look at native users, federated users (via the LDAP connector), query management, security event logs, custom plugins, user-defined procedures and more. In the meantime, download the enterprise security white paper below to dive into more details.








