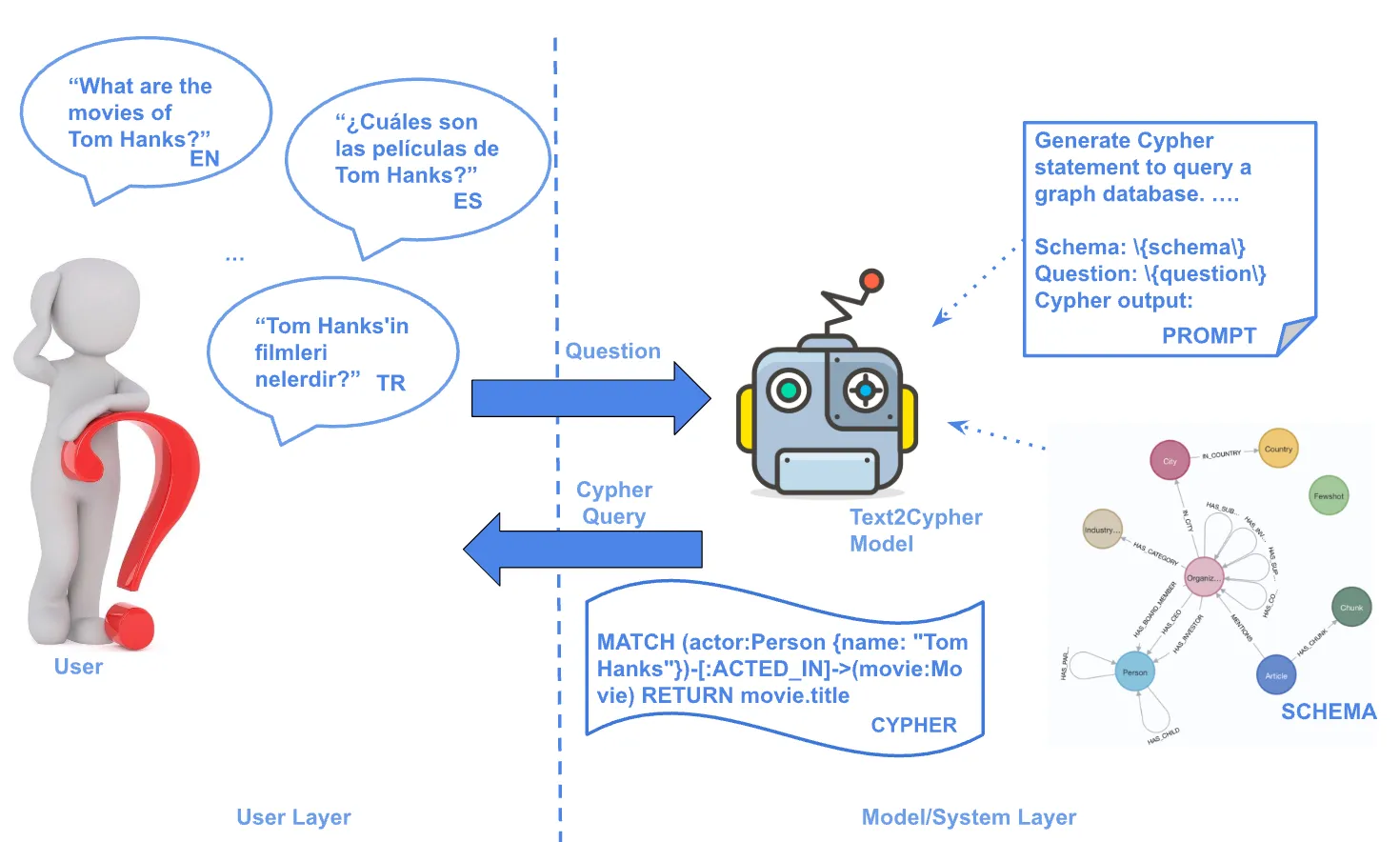
Network Security & CMDBs: Why Graph Visualization Is Essential

IT Associate
4 min read

You’re a security auditor. Your job is to secure your company’s network – you might as well be assigned to single handedly defend the entire Western Front. But unlike the armies of the Great War, you have an amazing tool: logs. Hundreds and hundreds of log files provide insight to every little crevice of your network.
Unfortunately you have to slave over all of these logs – no small task. Line by line, your eyes will eventually tire, increasing the chance you’ll miss a something. Hours after your shift ended you ask yourself why your company invested in a single networked standing lamp conveniently located in the downstairs storage closet. And no, they won’t let you disconnect it. You soon question all your life choices.
IT Management in the Internet of Things: No Easy Feat
Last month we posted an article on the Internet of Things (IoT), and how it’s spiraling into reality. As the number of devices on a given network increases, so does the difficulty of managing that network.
Even if you were an accountant in another life, the time where Excel sheets were ample tools for managing IPs is over. But even with their infinite insight, logs are also losing utility simply due to their sheer number. The use of graphical network utilities is becoming ever more necessary.
And while visualizing that data is important, just as critical is how the data is stored. Unless your network is somehow physically cabled out in a perfect grid, excel and traditional databases won’t well represent your network, no matter how detailed or complex.
Graph Databases as CMDBs
Welcome to the age of graph databases. Below, we have a small graph representing the devices of a small family. The idea is simple: each person owns devices.
The data storage is just as simple. Each person is stored as a node (Person), which has a directed relationship (OWNS) to another type of node (Device). Each node can also have properties, allowing for attributes to be set:
Now image the network of the family business. Actually, you don’t have to imagine anything, just keep scrolling.
You can see how this can grow a little difficult to manage, even for a small family business! But like any other database, the real power lies in queries. Let’s say I want to find all devices owned by Alice. I simply run the one-lined query MATCH (a:Person {name:"Alice"})-[:OWNS]->(b) RETURN b.
I could also run more complex queries, such as “give me all IPs tied to Alice”
match (a:Person {name:"Alice"})-[r:OWNS]-(b) return b.ip
or “which devices do Alice and Bob share.”
match (a:Person {name:"Alice"}) match (b:Person {name:"Bob"}) match (a)-[:OWNS]->(c),(b)-[:OWNS]->(c) return c
By leveraging this type of database, overlying CMDB (configuration management databases) applications would be relatively simple, simply running native queries.
Graph Databases and Network Security Audits
Graph databases also benefit you, the security auditor. Looking back to log examination, suppose you need to find ports that shouldn’t be open.
Instead of looking at rows and rows of dumped text, you could simply run a query for open ports. Of course, any database could accomplish this. Let’s expand our company business graph to the port level and isolate Alice’s macbook air:
MATCH (a:Person {name:"Alice"})-[:OWNS]->(b:Asset)-[:HAS_PORT]->(c) RETURN a,b,c
Actually, since Alice is the only one with a MacBook Air, we can simplify our query:
MATCH(a:Asset {model:"MacAir"})-[:HAS_PORT]->(b) RETURN a,b
With a graph database, one could also find all the devices connected to said suspicious port. One can then find the IPs of these devices, flagging them as risks and possibly blocking them. Each of these actions would only take a single query each, like the one below, which returns the IP address of any asset with open ports.
MATCH(a:Asset)-[:HAS_PORT]->(b:Port {isOpen:"1"}) RETURN a.ip,b.number
Thankfully, only Alice’s computer has any open ports that are suspicious.
Conclusion: All Data Is Connected
We naturally imagine our data to be connected. In fact, many models in our world are simple graphs, such as IT networks.
By storing data exactly how it’s diagramed, you can not only visualize a network better, but also catch discrepancies more easily. Why should we tire over translating and making sense of globs and globs of data when we can represent its natural state of existence?
Click below to read this white paper, How Graph Databases Solve Problems in Network & Data Center Management and dive deeper into how graph databases transform your data center and network management operations.