Neo4j Blog
Is Traditional SaaS Behind Us? The Graph + GenAI Revolution
The shift to an AI Tier requires rethinking how enterprise data is organized. Klarna and others are finding that graph create the foundation for AI to deliver real business value.
9 min read
Featured Voices



Most Recent

From the Neo4j Community: April 2016
4 min read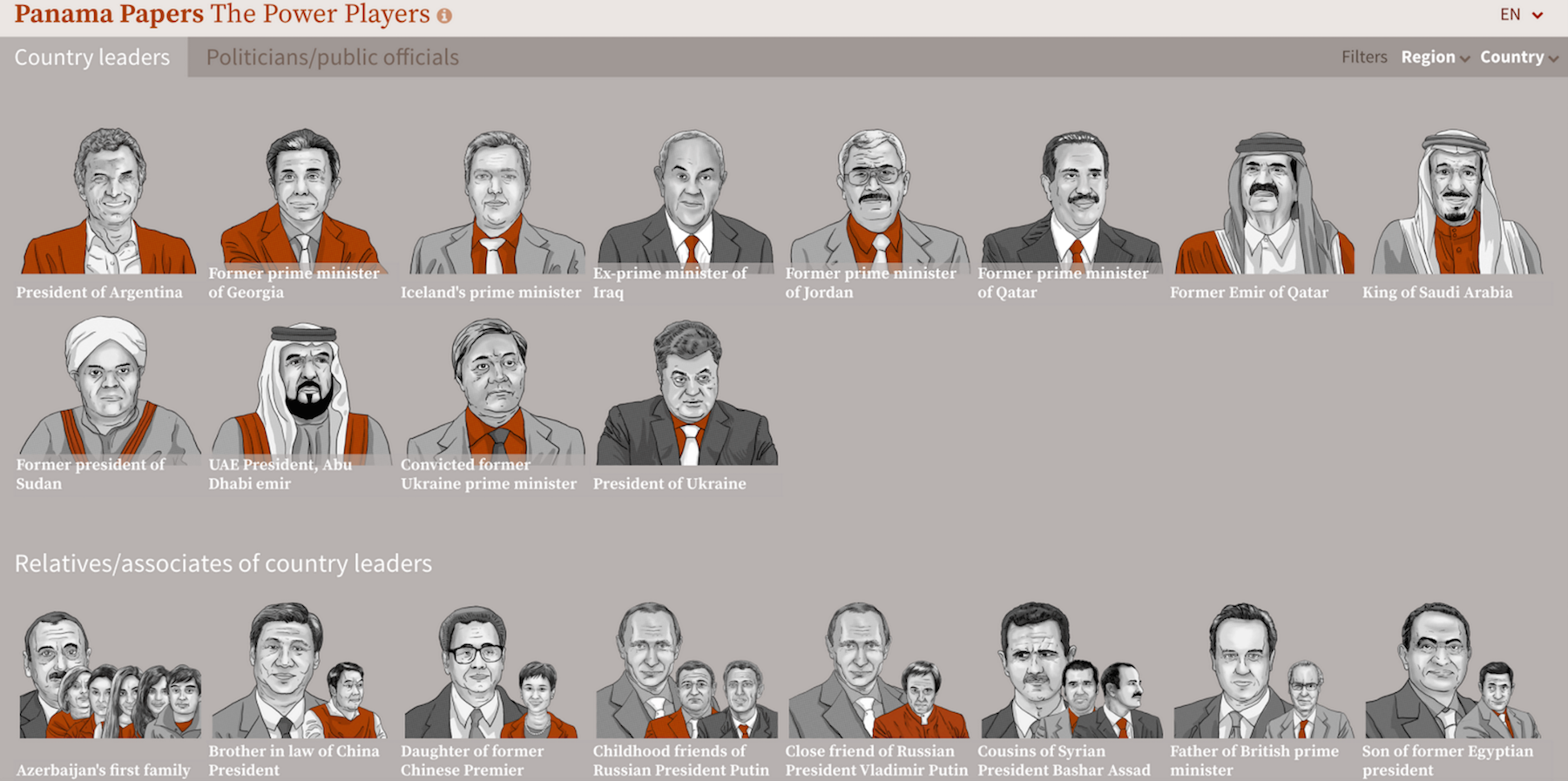
How the ICIJ Used Neo4j to Unravel the Panama Papers
14 min read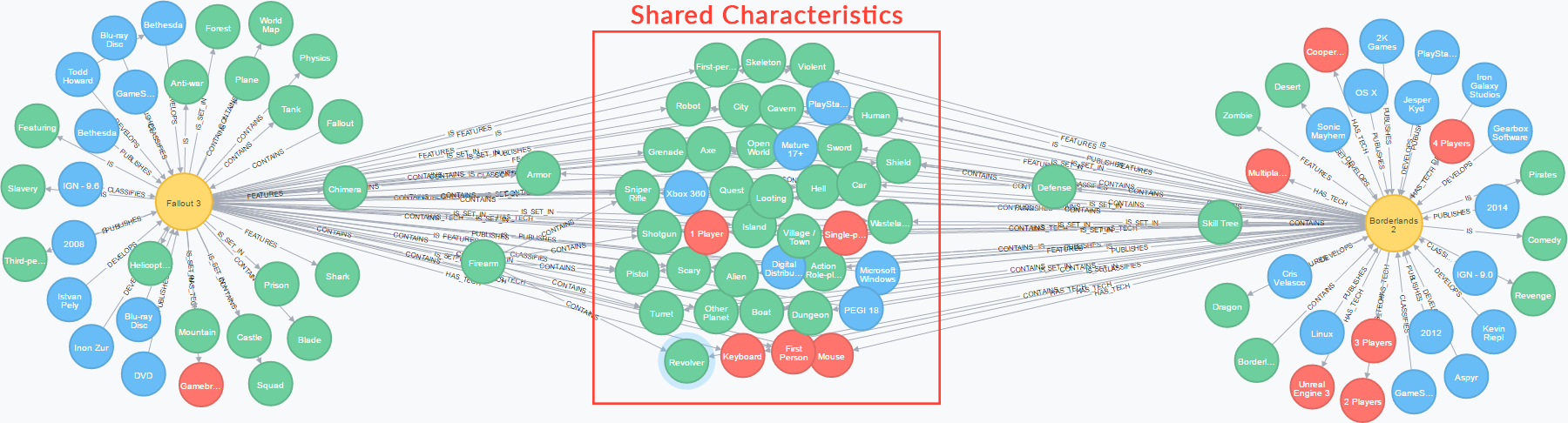
Game Discovery: A Recommendation Algorithm for Video Games [Community Post]
3 min read
From Good to Graph: Choosing the Right Database
12 min read



