Fine-grained access control
When creating a database, administrators may want to establish which users can access certain information.
As described in Built-in roles and privileges, Neo4j already offers preset roles configured to specific permissions (i.e. read, edit, or write). While these built-in roles cover many common daily scenarios, it is also possible to create custom roles for specific needs.
This tutorial walks you through a healthcare use case that illustrates various aspects of security and fine-grained access control.
Healthcare use case
To demonstrate the application of these tools, consider an example of a healthcare database which could be relevant in a medical clinic or hospital.
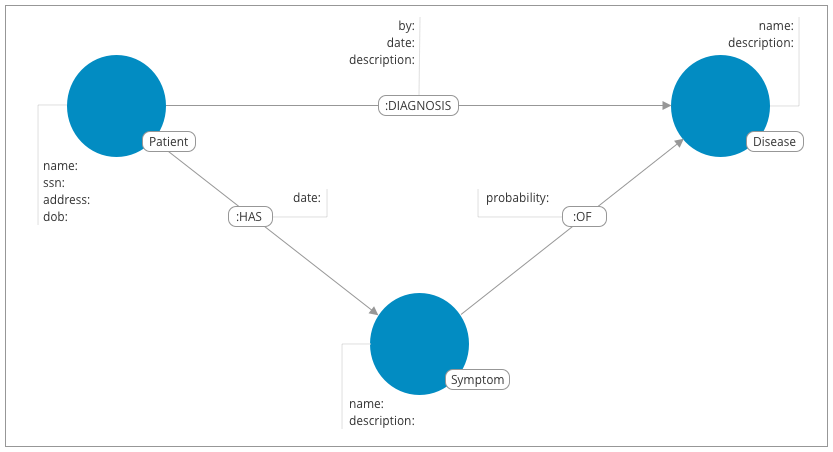
For simplicity reasons, only three labels are used to represent the following entities:
(:Patient)-
Patients that visit the clinic because they have some symptoms. Information specific to patients can be captured in properties:
-
name -
ssn -
address -
dateOfBirth
-
(:Symptom)-
A set of symptoms found in a catalog of known illnesses. They can be described using the properties:
-
name -
description
-
(:Disease)-
Known illnesses mapped in a catalog found in the database. They can be described using the properties:
-
name -
description
-
These entities are modelled as nodes, and connected by relationships of the following types:
(:Patient)-[:HAS]→(:Symptom)-
When a patient reports to the clinic, they describe their symptoms to the nurse or the doctor. The nurse or doctor then enters this information into the database in the form of connections between the patient node and a graph of known symptoms. Possible properties of interest on this relationship could be:
-
date- date when symptom was reported.
-
(:Symptom)-[:OF]→(:Disease)-
Symptoms are a subgraph in the graph of known diseases. The relationship between a symptom and a disease can include a probability factor for how likely or common it is for people with that disease to express that symptom. This will make it easier for the doctor to make a diagnosis using statistical queries.
-
probability- probability of symptom matching disease.
-
(:Patient)-[:DIAGNOSIS]→(:Disease)-
The doctor can use the graph of diseases and their symptoms to perform an initial investigation into the most likely diseases to match the patient. Based on this, and their own assessment of the patient, the doctor may make a diagnosis which they would persist to the graph through the addition of this relationship with appropriate properties:
-
by: doctor’s name -
date: date of diagnosis -
description: additional doctors' notes
-
This same database would be used by a number of different users, each with different access needs:
-
Doctors who need to diagnose patients.
-
Nurses who need to treat patients.
-
Receptionists who need to identify and record patient information.
-
Researchers who need to perform statistical analysis of medical data.
-
IT administrators who need to manage the database, to create and assign users for example.
To create the database, start by creating the nodes and relationships that represent the entities described above.
Create the healthcare database
The following steps assume that you have installed Neo4j Enterprise edition and it is running. For details, see Installation.
-
Using Cypher Shell, log into the
systemdatabase as theneo4juser:cypher-shell -u neo4j -p my-password -d system -
Create the
healthcaredatabase:CREATE DATABASE healthcare; -
Set the
healthcaredatabase as the default database:CALL dbms.setDefaultDatabase("healthcare");+----------------------------------------------------------------------+ | result | +----------------------------------------------------------------------+ | "Old default database unset. New default database set to healthcare" | +----------------------------------------------------------------------+ 1 row ready to start consuming query after 9 ms, results consumed after another 4 ms
Import data into the healthcare database
Create the nodes and relationships that represent the entities described above in section Healthcare use case.
-
Switch to the
healthcaredatabase::use healthcare; -
Create some data for symptoms:
WITH ['Itchy','Scratchy','Sore','Swollen','Red','Inflamed','Angry','Sad','Pale','Dizzy'] AS symptoms UNWIND symptoms AS symptom MERGE (s:Symptom {name:symptom}) ON CREATE SET s.description = 'Looks ' + toLower(symptom) RETURN s.name, s.description;Result
+-------------------------------+ | s.name | s.description | +-------------------------------+ | "Itchy" | "Looks itchy" | | "Scratchy" | "Looks scratchy" | | "Sore" | "Looks sore" | | "Swollen" | "Looks swollen" | | "Red" | "Looks red" | | "Inflamed" | "Looks inflamed" | | "Angry" | "Looks angry" | | "Sad" | "Looks sad" | | "Pale" | "Looks pale" | | "Dizzy" | "Looks dizzy" | +-------------------------------+ 10 rows ready to start consuming query after 53 ms, results consumed after another 24 ms Added 10 nodes, Set 20 properties, Added 10 labels
-
Create some data for diseases:
WITH ['Argitis','Whatitis','Otheritis','Someitis','Placeboitis','Yellowitis'] AS diseases, ['Chronic','Acute'] AS severity UNWIND diseases AS disease UNWIND severity as sev MERGE (d:Disease {name:sev+' '+disease}) ON CREATE SET d.description = sev + ' ' + toLower(disease) RETURN d.name, d.description;Result
+-----------------------------------------------+ | d.name | d.description | +-----------------------------------------------+ | "Chronic Argitis" | "Chronic argitis" | | "Acute Argitis" | "Acute argitis" | | "Chronic Whatitis" | "Chronic whatitis" | | "Acute Whatitis" | "Acute whatitis" | | "Chronic Otheritis" | "Chronic otheritis" | | "Acute Otheritis" | "Acute otheritis" | | "Chronic Someitis" | "Chronic someitis" | | "Acute Someitis" | "Acute someitis" | | "Chronic Placeboitis" | "Chronic placeboitis" | | "Acute Placeboitis" | "Acute placeboitis" | | "Chronic Yellowitis" | "Chronic yellowitis" | | "Acute Yellowitis" | "Acute yellowitis" | +-----------------------------------------------+ 12 rows ready to start consuming query after 56 ms, results consumed after another 7 ms Added 12 nodes, Set 24 properties, Added 12 labels
-
Create relationships between symptoms and diseases:
MATCH (s:Symptom) WITH collect(s) as symptoms WITH symptoms, size(symptoms) / 2 as maxsym MATCH (d:Disease) UNWIND range(0,maxsym) as symi WITH d, symi, symptoms, toInteger(size(symptoms) * rand()) as si, rand()/2 + 0.5 AS prob WITH d, symptoms[si] AS s, prob MERGE (s)-[o:OF]->(d) ON CREATE SET o.probability = prob RETURN d.name, o.probability, s.name;Result
+---------------------------------------------------------+ | d.name | o.probability | s.name | +---------------------------------------------------------+ | "Chronic Argitis" | 0.5488344602870381 | "Scratchy" | | "Chronic Argitis" | 0.660404649462915 | "Itchy" | | "Chronic Argitis" | 0.6905998399032373 | "Angry" | | "Chronic Argitis" | 0.660404649462915 | "Itchy" | | "Chronic Argitis" | 0.8740581222813869 | "Red" | | "Chronic Argitis" | 0.7456909803542418 | "Sore" | | "Acute Argitis" | 0.607200508350778 | "Pale" | | "Acute Argitis" | 0.5772236253537283 | "Red" | | "Acute Argitis" | 0.7268375663608245 | "Inflamed" | | "Acute Argitis" | 0.847011132303783 | "Itchy" | | "Acute Argitis" | 0.8025327549974599 | "Sore" | | "Acute Argitis" | 0.5772236253537283 | "Red" | | "Chronic Whatitis" | 0.9185112224896539 | "Sore" | | "Chronic Whatitis" | 0.8220811592705012 | "Dizzy" | | "Chronic Whatitis" | 0.8220811592705012 | "Dizzy" | | "Chronic Whatitis" | 0.9947532896439784 | "Scratchy" | | "Chronic Whatitis" | 0.5479749642339755 | "Red" | | "Chronic Whatitis" | 0.9466973516593605 | "Inflamed" | | "Acute Whatitis" | 0.7217509679510017 | "Inflamed" | | "Acute Whatitis" | 0.7217509679510017 | "Inflamed" | | "Acute Whatitis" | 0.7073350047270233 | "Scratchy" | | "Acute Whatitis" | 0.7217509679510017 | "Inflamed" | | "Acute Whatitis" | 0.6800748332507602 | "Red" | | "Acute Whatitis" | 0.6953854679660172 | "Itchy" | | "Chronic Otheritis" | 0.5570795327063996 | "Scratchy" | | "Chronic Otheritis" | 0.7615506655612736 | "Swollen" | | "Chronic Otheritis" | 0.7147549568270981 | "Angry" | | "Chronic Otheritis" | 0.9309059023795485 | "Red" | | "Chronic Otheritis" | 0.8339105187862091 | "Dizzy" | | "Chronic Otheritis" | 0.7147549568270981 | "Angry" | | "Acute Otheritis" | 0.7449502448640619 | "Red" | | "Acute Otheritis" | 0.6635390850482914 | "Sad" | | "Acute Otheritis" | 0.6488764428922569 | "Itchy" | | "Acute Otheritis" | 0.7642990617862074 | "Pale" | | "Acute Otheritis" | 0.5532690807468361 | "Scratchy" | | "Acute Otheritis" | 0.8062425062999423 | "Inflamed" | | "Chronic Someitis" | 0.580678012588533 | "Sore" | | "Chronic Someitis" | 0.9569035040624002 | "Red" | | "Chronic Someitis" | 0.9328323008783481 | "Inflamed" | | "Chronic Someitis" | 0.9569035040624002 | "Red" | | "Chronic Someitis" | 0.5492540886308123 | "Pale" | | "Chronic Someitis" | 0.9204301026117075 | "Swollen" | | "Acute Someitis" | 0.9969140989164824 | "Itchy" | | "Acute Someitis" | 0.8756876989165112 | "Swollen" | | "Acute Someitis" | 0.9969140989164824 | "Itchy" | | "Acute Someitis" | 0.6258855371986936 | "Red" | | "Acute Someitis" | 0.9928922186427123 | "Angry" | | "Acute Someitis" | 0.6258855371986936 | "Red" | | "Chronic Placeboitis" | 0.9837947935707738 | "Itchy" | | "Chronic Placeboitis" | 0.7795050137703664 | "Inflamed" | | "Chronic Placeboitis" | 0.680595344835278 | "Sad" | | "Chronic Placeboitis" | 0.8383237671521345 | "Scratchy" | | "Chronic Placeboitis" | 0.7054054618102132 | "Swollen" | | "Chronic Placeboitis" | 0.7795050137703664 | "Inflamed" | | "Acute Placeboitis" | 0.768802727874529 | "Dizzy" | | "Acute Placeboitis" | 0.6645530219645431 | "Scratchy" | | "Acute Placeboitis" | 0.9192262998770437 | "Pale" | | "Acute Placeboitis" | 0.7321327463249545 | "Itchy" | | "Acute Placeboitis" | 0.5768920173860386 | "Sad" | | "Acute Placeboitis" | 0.5467367430608921 | "Sore" | | "Chronic Yellowitis" | 0.657149882924074 | "Dizzy" | | "Chronic Yellowitis" | 0.5274096280530778 | "Swollen" | | "Chronic Yellowitis" | 0.657149882924074 | "Dizzy" | | "Chronic Yellowitis" | 0.9011165844619397 | "Scratchy" | | "Chronic Yellowitis" | 0.5274096280530778 | "Swollen" | | "Chronic Yellowitis" | 0.7267736062002124 | "Sore" | | "Acute Yellowitis" | 0.7764355480097833 | "Swollen" | | "Acute Yellowitis" | 0.9776709262803641 | "Inflamed" | | "Acute Yellowitis" | 0.6495454012653183 | "Red" | | "Acute Yellowitis" | 0.7764355480097833 | "Swollen" | | "Acute Yellowitis" | 0.7395280933743617 | "Dizzy" | | "Acute Yellowitis" | 0.6068906083054821 | "Itchy" | +---------------------------------------------------------+ 72 rows ready to start consuming query after 339 ms, results consumed after another 28 ms Created 59 relationships, Set 59 properties
-
Ensure that the as yet non-existent types can be used:
CALL db.createRelationshipType('DIAGNOSIS'); CALL db.createProperty('by'); CALL db.createProperty('date'); CALL db.createProperty('description'); CALL db.createProperty('created_at'); CALL db.createProperty('updated_at');Result
0 rows ready to start consuming query after 22 ms, results consumed after another 0 ms 0 rows ready to start consuming query after 17 ms, results consumed after another 0 ms 0 rows ready to start consuming query after 7 ms, results consumed after another 0 ms 0 rows ready to start consuming query after 7 ms, results consumed after another 0 ms 0 rows ready to start consuming query after 8 ms, results consumed after another 0 ms 0 rows ready to start consuming query after 7 ms, results consumed after another 0 ms
-
Create some data for patients:
WITH ['Jack','Mary','Sally','Mark','Joe','Jane','Bob','Ally'] AS firstnames, ['Anderson','Jackson','Svensson','Smith','Stone'] AS surnames, ['mymail.com','example.com','other.org','net.net'] AS domains UNWIND range(0,100) AS uid WITH 1234567+uid AS ssn, firstnames[uid%size(firstnames)] AS firstname, surnames[uid%size(surnames)] AS surname, domains[uid%size(domains)] AS domain WITH ssn, firstname, surname, tolower(firstname + '.' + surname + '@' + domain) AS email, toInteger(1500000000000 * rand()) AS ts MERGE (p:Patient {ssn:ssn}) ON CREATE SET p.name = firstname + ' ' + surname, p.email = email, p.address = '1 secret way, downtown', p.dateOfBirth = date(datetime({epochmillis:ts})) RETURN count(p);Result
+----------+ | count(p) | +----------+ | 101 | +----------+ 1 row ready to start consuming query after 49 ms, results consumed after another 38 ms Added 101 nodes, Set 505 properties, Added 101 labels
-
Create relationships between patients and symptoms:
MATCH (s:Symptom) WITH collect(s) as symptoms WITH symptoms, size(symptoms) / 2 as maxsym, 1500000000000 AS base, 75477004177 AS diff MATCH (p:Patient) UNWIND range(0,maxsym) as symi WITH p, symi, symptoms, toInteger(size(symptoms) * rand()) as si, rand()/2 + 0.5 AS prob, base + toInteger(diff * rand()) AS ts WITH p, symptoms[si] AS s, prob, ts MERGE (p)-[h:HAS]->(s) ON CREATE SET h.date = date(datetime({epochmillis:ts})) RETURN p.name, p.dateOfBirth, h.date, s.name;Result
+------------------------------------------------------------+ | p.name | p.dateOfBirth | h.date | s.name | +------------------------------------------------------------+ | "Jack Anderson" | 1981-01-10 | 2019-03-03 | "Angry" | | "Jack Anderson" | 1981-01-10 | 2018-05-05 | "Sad" | | "Jack Anderson" | 1981-01-10 | 2018-06-05 | "Sore" | | "Jack Anderson" | 1981-01-10 | 2017-11-17 | "Itchy" | | "Jack Anderson" | 1981-01-10 | 2017-10-02 | "Dizzy" | | "Jack Anderson" | 1981-01-10 | 2019-11-01 | "Red" | | "Mary Jackson" | 1983-05-24 | 2018-03-30 | "Scratchy" | | "Mary Jackson" | 1983-05-24 | 2018-03-08 | "Pale" | | "Mary Jackson" | 1983-05-24 | 2019-05-03 | "Dizzy" | | "Mary Jackson" | 1983-05-24 | 2019-08-16 | "Red" | | "Mary Jackson" | 1983-05-24 | 2018-07-07 | "Inflamed" | | "Mary Jackson" | 1983-05-24 | 2018-07-07 | "Inflamed" | | "Sally Svensson" | 2011-04-03 | 2018-02-12 | "Sore" | | "Sally Svensson" | 2011-04-03 | 2019-07-23 | "Pale" | | "Sally Svensson" | 2011-04-03 | 2019-04-17 | "Sad" | | "Sally Svensson" | 2011-04-03 | 2017-09-25 | "Red" | | "Sally Svensson" | 2011-04-03 | 2017-08-14 | "Swollen" | | "Sally Svensson" | 2011-04-03 | 2017-08-14 | "Swollen" | | "Mark Smith" | 1998-08-26 | 2018-08-25 | "Inflamed" | | "Mark Smith" | 1998-08-26 | 2018-08-25 | "Inflamed" | | "Mark Smith" | 1998-08-26 | 2018-05-14 | "Itchy" | | "Mark Smith" | 1998-08-26 | 2019-07-02 | "Dizzy" | | "Mark Smith" | 1998-08-26 | 2018-02-27 | "Sad" | | "Mark Smith" | 1998-08-26 | 2018-10-07 | "Swollen" | | "Joe Stone" | 1972-10-20 | 2019-05-16 | "Red" | | "Joe Stone" | 1972-10-20 | 2018-08-31 | "Inflamed" | | "Joe Stone" | 1972-10-20 | 2018-08-31 | "Inflamed" | | "Joe Stone" | 1972-10-20 | 2017-07-21 | "Sore" | | "Joe Stone" | 1972-10-20 | 2018-08-31 | "Inflamed" | | "Joe Stone" | 1972-10-20 | 2017-10-21 | "Itchy" | | "Jane Anderson" | 2001-10-18 | 2018-07-04 | "Scratchy" | | "Jane Anderson" | 2001-10-18 | 2019-02-09 | "Dizzy" | | "Jane Anderson" | 2001-10-18 | 2018-05-03 | "Pale" | | "Jane Anderson" | 2001-10-18 | 2019-08-13 | "Angry" | | "Jane Anderson" | 2001-10-18 | 2018-05-03 | "Pale" | | "Jane Anderson" | 2001-10-18 | 2019-11-12 | "Swollen" | | "Bob Jackson" | 1997-08-20 | 2019-05-03 | "Sad" | | "Bob Jackson" | 1997-08-20 | 2019-03-14 | "Red" | | "Bob Jackson" | 1997-08-20 | 2019-03-01 | "Angry" | | "Bob Jackson" | 1997-08-20 | 2018-03-10 | "Sore" | | "Bob Jackson" | 1997-08-20 | 2018-03-10 | "Sore" | | "Bob Jackson" | 1997-08-20 | 2019-05-03 | "Sad" | | "Ally Svensson" | 2008-05-25 | 2019-06-06 | "Sore" | | "Ally Svensson" | 2008-05-25 | 2019-11-04 | "Sad" | | "Ally Svensson" | 2008-05-25 | 2018-10-04 | "Scratchy" | | "Ally Svensson" | 2008-05-25 | 2017-11-28 | "Inflamed" | | "Ally Svensson" | 2008-05-25 | 2018-10-29 | "Itchy" | | "Ally Svensson" | 2008-05-25 | 2019-08-08 | "Angry" | | "Jack Smith" | 1974-07-02 | 2018-01-15 | "Itchy" | | "Jack Smith" | 1974-07-02 | 2019-02-12 | "Angry" | | "Jack Smith" | 1974-07-02 | 2017-10-16 | "Dizzy" | | "Jack Smith" | 1974-07-02 | 2018-01-03 | "Red" | | "Jack Smith" | 1974-07-02 | 2018-01-15 | "Itchy" | | "Jack Smith" | 1974-07-02 | 2017-11-14 | "Pale" | | "Mary Stone" | 1983-09-27 | 2018-01-14 | "Dizzy" | | "Mary Stone" | 1983-09-27 | 2019-03-24 | "Swollen" | | "Mary Stone" | 1983-09-27 | 2018-04-07 | "Angry" | | "Mary Stone" | 1983-09-27 | 2019-03-24 | "Swollen" | | "Mary Stone" | 1983-09-27 | 2018-01-14 | "Dizzy" | | "Mary Stone" | 1983-09-27 | 2017-11-27 | "Sore" | | "Sally Anderson" | 2009-12-14 | 2019-08-21 | "Swollen" | | "Sally Anderson" | 2009-12-14 | 2018-02-23 | "Sore" | | "Sally Anderson" | 2009-12-14 | 2018-06-05 | "Scratchy" | | "Sally Anderson" | 2009-12-14 | 2018-02-23 | "Sore" | | "Sally Anderson" | 2009-12-14 | 2017-08-20 | "Pale" | | "Sally Anderson" | 2009-12-14 | 2019-05-25 | "Itchy" | | "Mark Jackson" | 1970-11-29 | 2018-09-27 | "Sore" | | "Mark Jackson" | 1970-11-29 | 2017-12-27 | "Angry" | | "Mark Jackson" | 1970-11-29 | 2017-12-26 | "Swollen" | | "Mark Jackson" | 1970-11-29 | 2018-09-27 | "Sore" | | "Mark Jackson" | 1970-11-29 | 2018-02-01 | "Inflamed" | | "Mark Jackson" | 1970-11-29 | 2018-12-19 | "Pale" | | "Joe Svensson" | 1972-02-12 | 2017-07-27 | "Sad" | | "Joe Svensson" | 1972-02-12 | 2019-07-27 | "Itchy" | | "Joe Svensson" | 1972-02-12 | 2019-06-20 | "Sore" | | "Joe Svensson" | 1972-02-12 | 2019-11-09 | "Inflamed" | | "Joe Svensson" | 1972-02-12 | 2019-07-27 | "Itchy" | | "Joe Svensson" | 1972-02-12 | 2019-07-27 | "Itchy" | | "Jane Smith" | 2013-04-09 | 2018-12-13 | "Swollen" | | "Jane Smith" | 2013-04-09 | 2018-12-13 | "Swollen" | | "Jane Smith" | 2013-04-09 | 2019-03-13 | "Red" | | "Jane Smith" | 2013-04-09 | 2019-01-25 | "Dizzy" | | "Jane Smith" | 2013-04-09 | 2017-07-25 | "Angry" | | "Jane Smith" | 2013-04-09 | 2018-04-11 | "Inflamed" | | "Bob Stone" | 2012-04-11 | 2018-09-04 | "Inflamed" | | "Bob Stone" | 2012-04-11 | 2017-08-07 | "Red" | | "Bob Stone" | 2012-04-11 | 2019-07-11 | "Swollen" | | "Bob Stone" | 2012-04-11 | 2019-07-11 | "Swollen" | | "Bob Stone" | 2012-04-11 | 2019-07-14 | "Sore" | | "Bob Stone" | 2012-04-11 | 2017-11-18 | "Itchy" | | "Ally Anderson" | 2000-05-24 | 2018-11-27 | "Itchy" | | "Ally Anderson" | 2000-05-24 | 2018-02-10 | "Pale" | | "Ally Anderson" | 2000-05-24 | 2017-07-25 | "Red" | | "Ally Anderson" | 2000-05-24 | 2018-03-19 | "Sad" | | "Ally Anderson" | 2000-05-24 | 2017-07-25 | "Red" | | "Ally Anderson" | 2000-05-24 | 2017-07-25 | "Red" | | "Jack Jackson" | 1988-03-13 | 2018-06-29 | "Sad" | | "Jack Jackson" | 1988-03-13 | 2019-06-25 | "Sore" | | "Jack Jackson" | 1988-03-13 | 2019-05-27 | "Inflamed" | | "Jack Jackson" | 1988-03-13 | 2018-07-09 | "Angry" | | "Jack Jackson" | 1988-03-13 | 2018-04-23 | "Pale" | | "Jack Jackson" | 1988-03-13 | 2019-05-15 | "Dizzy" | | "Mary Svensson" | 2008-01-19 | 2018-03-16 | "Dizzy" | | "Mary Svensson" | 2008-01-19 | 2018-04-14 | "Red" | | "Mary Svensson" | 2008-01-19 | 2018-10-25 | "Pale" | | "Mary Svensson" | 2008-01-19 | 2019-07-15 | "Swollen" | | "Mary Svensson" | 2008-01-19 | 2019-07-15 | "Swollen" | | "Mary Svensson" | 2008-01-19 | 2018-04-14 | "Red" | | "Sally Smith" | 1977-03-20 | 2019-02-23 | "Dizzy" | | "Sally Smith" | 1977-03-20 | 2017-11-28 | "Red" | | "Sally Smith" | 1977-03-20 | 2018-06-23 | "Scratchy" | | "Sally Smith" | 1977-03-20 | 2017-10-28 | "Sad" | | "Sally Smith" | 1977-03-20 | 2017-11-28 | "Red" | | "Sally Smith" | 1977-03-20 | 2018-10-05 | "Inflamed" | | "Mark Stone" | 1986-06-15 | 2019-11-24 | "Pale" | | "Mark Stone" | 1986-06-15 | 2018-07-30 | "Itchy" | | "Mark Stone" | 1986-06-15 | 2018-07-30 | "Itchy" | | "Mark Stone" | 1986-06-15 | 2017-09-10 | "Dizzy" | | "Mark Stone" | 1986-06-15 | 2018-07-18 | "Red" | | "Mark Stone" | 1986-06-15 | 2019-08-15 | "Sore" | | "Joe Anderson" | 1980-09-06 | 2019-06-19 | "Dizzy" | | "Joe Anderson" | 1980-09-06 | 2017-11-28 | "Red" | | "Joe Anderson" | 1980-09-06 | 2019-08-12 | "Scratchy" | | "Joe Anderson" | 1980-09-06 | 2019-08-12 | "Scratchy" | | "Joe Anderson" | 1980-09-06 | 2019-06-19 | "Dizzy" | | "Joe Anderson" | 1980-09-06 | 2017-07-16 | "Inflamed" | | "Jane Jackson" | 2016-02-20 | 2018-04-03 | "Swollen" | | "Jane Jackson" | 2016-02-20 | 2018-02-21 | "Pale" | | "Jane Jackson" | 2016-02-20 | 2018-07-17 | "Angry" | | "Jane Jackson" | 2016-02-20 | 2018-01-22 | "Sore" | | "Jane Jackson" | 2016-02-20 | 2018-01-22 | "Sore" | | "Jane Jackson" | 2016-02-20 | 2017-09-28 | "Dizzy" | | "Bob Svensson" | 1983-08-04 | 2019-02-02 | "Pale" | | "Bob Svensson" | 1983-08-04 | 2018-12-01 | "Dizzy" | | "Bob Svensson" | 1983-08-04 | 2019-08-07 | "Sad" | | "Bob Svensson" | 1983-08-04 | 2018-11-18 | "Swollen" | | "Bob Svensson" | 1983-08-04 | 2018-12-25 | "Scratchy" | | "Bob Svensson" | 1983-08-04 | 2018-04-09 | "Inflamed" | | "Ally Smith" | 2012-03-01 | 2018-03-28 | "Inflamed" | | "Ally Smith" | 2012-03-01 | 2018-03-28 | "Inflamed" | | "Ally Smith" | 2012-03-01 | 2018-06-09 | "Scratchy" | | "Ally Smith" | 2012-03-01 | 2019-01-25 | "Angry" | | "Ally Smith" | 2012-03-01 | 2018-09-06 | "Pale" | | "Ally Smith" | 2012-03-01 | 2018-12-04 | "Dizzy" | | "Jack Stone" | 2009-11-08 | 2019-01-18 | "Pale" | | "Jack Stone" | 2009-11-08 | 2018-03-29 | "Angry" | | "Jack Stone" | 2009-11-08 | 2019-10-22 | "Inflamed" | | "Jack Stone" | 2009-11-08 | 2019-01-18 | "Pale" | | "Jack Stone" | 2009-11-08 | 2017-12-09 | "Itchy" | | "Jack Stone" | 2009-11-08 | 2018-10-27 | "Red" | | "Mary Anderson" | 1991-11-25 | 2018-01-02 | "Angry" | | "Mary Anderson" | 1991-11-25 | 2018-01-02 | "Angry" | | "Mary Anderson" | 1991-11-25 | 2017-11-01 | "Inflamed" | | "Mary Anderson" | 1991-11-25 | 2017-12-16 | "Sore" | | "Mary Anderson" | 1991-11-25 | 2018-01-02 | "Angry" | | "Mary Anderson" | 1991-11-25 | 2018-03-22 | "Red" | | "Sally Jackson" | 2008-11-09 | 2019-07-02 | "Inflamed" | | "Sally Jackson" | 2008-11-09 | 2018-02-24 | "Red" | | "Sally Jackson" | 2008-11-09 | 2019-08-07 | "Swollen" | | "Sally Jackson" | 2008-11-09 | 2019-04-05 | "Sore" | | "Sally Jackson" | 2008-11-09 | 2019-07-02 | "Inflamed" | | "Sally Jackson" | 2008-11-09 | 2019-02-23 | "Scratchy" | | "Mark Svensson" | 1979-06-22 | 2019-08-09 | "Itchy" | | "Mark Svensson" | 1979-06-22 | 2019-05-11 | "Swollen" | | "Mark Svensson" | 1979-06-22 | 2018-08-11 | "Inflamed" | | "Mark Svensson" | 1979-06-22 | 2019-08-09 | "Itchy" | | "Mark Svensson" | 1979-06-22 | 2017-10-11 | "Sad" | | "Mark Svensson" | 1979-06-22 | 2019-09-22 | "Scratchy" | | "Joe Smith" | 2008-07-03 | 2017-08-24 | "Sore" | | "Joe Smith" | 2008-07-03 | 2018-12-03 | "Red" | | "Joe Smith" | 2008-07-03 | 2018-12-03 | "Red" | | "Joe Smith" | 2008-07-03 | 2018-08-20 | "Inflamed" | | "Joe Smith" | 2008-07-03 | 2018-12-03 | "Red" | | "Joe Smith" | 2008-07-03 | 2019-04-17 | "Angry" | | "Jane Stone" | 1977-11-25 | 2018-03-19 | "Scratchy" | | "Jane Stone" | 1977-11-25 | 2017-08-18 | "Dizzy" | | "Jane Stone" | 1977-11-25 | 2017-12-09 | "Red" | | "Jane Stone" | 1977-11-25 | 2018-06-14 | "Swollen" | | "Jane Stone" | 1977-11-25 | 2018-08-22 | "Pale" | | "Jane Stone" | 1977-11-25 | 2018-08-22 | "Pale" | | "Bob Anderson" | 1970-04-27 | 2019-10-17 | "Scratchy" | | "Bob Anderson" | 1970-04-27 | 2018-06-16 | "Red" | | "Bob Anderson" | 1970-04-27 | 2017-11-07 | "Itchy" | | "Bob Anderson" | 1970-04-27 | 2018-12-11 | "Pale" | | "Bob Anderson" | 1970-04-27 | 2017-11-07 | "Itchy" | | "Bob Anderson" | 1970-04-27 | 2019-02-26 | "Swollen" | | "Ally Jackson" | 1982-01-12 | 2019-06-15 | "Sad" | | "Ally Jackson" | 1982-01-12 | 2018-01-12 | "Sore" | | "Ally Jackson" | 1982-01-12 | 2019-06-15 | "Sad" | | "Ally Jackson" | 1982-01-12 | 2018-01-12 | "Sore" | | "Ally Jackson" | 1982-01-12 | 2018-04-19 | "Itchy" | | "Ally Jackson" | 1982-01-12 | 2019-04-06 | "Red" | | "Jack Svensson" | 2012-08-22 | 2017-12-10 | "Scratchy" | | "Jack Svensson" | 2012-08-22 | 2018-08-25 | "Pale" | | "Jack Svensson" | 2012-08-22 | 2017-12-10 | "Scratchy" | | "Jack Svensson" | 2012-08-22 | 2018-12-07 | "Swollen" | | "Jack Svensson" | 2012-08-22 | 2018-08-25 | "Pale" | | "Jack Svensson" | 2012-08-22 | 2018-04-30 | "Red" | | "Mary Smith" | 2002-11-27 | 2018-07-26 | "Red" | | "Mary Smith" | 2002-11-27 | 2018-04-09 | "Dizzy" | | "Mary Smith" | 2002-11-27 | 2018-08-08 | "Pale" | | "Mary Smith" | 2002-11-27 | 2018-08-28 | "Sore" | | "Mary Smith" | 2002-11-27 | 2018-07-26 | "Red" | | "Mary Smith" | 2002-11-27 | 2019-09-16 | "Itchy" | | "Sally Stone" | 2001-04-25 | 2018-02-13 | "Sore" | | "Sally Stone" | 2001-04-25 | 2019-05-03 | "Itchy" | | "Sally Stone" | 2001-04-25 | 2019-09-25 | "Dizzy" | | "Sally Stone" | 2001-04-25 | 2018-05-10 | "Inflamed" | | "Sally Stone" | 2001-04-25 | 2019-09-03 | "Scratchy" | | "Sally Stone" | 2001-04-25 | 2018-05-10 | "Inflamed" | | "Mark Anderson" | 2007-06-19 | 2019-04-22 | "Angry" | | "Mark Anderson" | 2007-06-19 | 2018-09-23 | "Scratchy" | | "Mark Anderson" | 2007-06-19 | 2019-03-10 | "Pale" | | "Mark Anderson" | 2007-06-19 | 2019-03-10 | "Pale" | | "Mark Anderson" | 2007-06-19 | 2018-09-23 | "Scratchy" | | "Mark Anderson" | 2007-06-19 | 2017-11-16 | "Sad" | | "Joe Jackson" | 1991-10-12 | 2018-06-27 | "Red" | | "Joe Jackson" | 1991-10-12 | 2018-10-26 | "Pale" | | "Joe Jackson" | 1991-10-12 | 2018-10-30 | "Sore" | | "Joe Jackson" | 1991-10-12 | 2018-10-30 | "Sore" | | "Joe Jackson" | 1991-10-12 | 2018-10-26 | "Pale" | | "Joe Jackson" | 1991-10-12 | 2019-01-06 | "Swollen" | | "Jane Svensson" | 1982-07-02 | 2019-11-29 | "Red" | | "Jane Svensson" | 1982-07-02 | 2017-12-07 | "Angry" | | "Jane Svensson" | 1982-07-02 | 2019-04-05 | "Swollen" | | "Jane Svensson" | 1982-07-02 | 2019-04-05 | "Swollen" | | "Jane Svensson" | 1982-07-02 | 2018-12-10 | "Sad" | | "Jane Svensson" | 1982-07-02 | 2019-11-09 | "Inflamed" | | "Bob Smith" | 1981-10-29 | 2018-07-21 | "Sad" | | "Bob Smith" | 1981-10-29 | 2019-09-15 | "Itchy" | | "Bob Smith" | 1981-10-29 | 2019-04-18 | "Scratchy" | | "Bob Smith" | 1981-10-29 | 2019-05-12 | "Swollen" | | "Bob Smith" | 1981-10-29 | 2018-07-21 | "Sad" | | "Bob Smith" | 1981-10-29 | 2019-02-04 | "Pale" | | "Ally Stone" | 1980-12-13 | 2018-08-02 | "Red" | | "Ally Stone" | 1980-12-13 | 2017-09-04 | "Dizzy" | | "Ally Stone" | 1980-12-13 | 2017-09-04 | "Dizzy" | | "Ally Stone" | 1980-12-13 | 2017-09-13 | "Pale" | | "Ally Stone" | 1980-12-13 | 2018-01-21 | "Sad" | | "Ally Stone" | 1980-12-13 | 2017-09-04 | "Dizzy" | | "Jack Anderson" | 1998-11-09 | 2019-01-22 | "Swollen" | | "Jack Anderson" | 1998-11-09 | 2019-07-14 | "Red" | | "Jack Anderson" | 1998-11-09 | 2019-05-21 | "Inflamed" | | "Jack Anderson" | 1998-11-09 | 2019-05-21 | "Inflamed" | | "Jack Anderson" | 1998-11-09 | 2019-06-18 | "Itchy" | | "Jack Anderson" | 1998-11-09 | 2019-01-22 | "Swollen" | | "Mary Jackson" | 1974-09-25 | 2018-12-10 | "Itchy" | | "Mary Jackson" | 1974-09-25 | 2017-10-13 | "Swollen" | | "Mary Jackson" | 1974-09-25 | 2018-02-26 | "Red" | | "Mary Jackson" | 1974-09-25 | 2018-01-25 | "Sad" | | "Mary Jackson" | 1974-09-25 | 2017-08-05 | "Inflamed" | | "Mary Jackson" | 1974-09-25 | 2018-09-22 | "Scratchy" | | "Sally Svensson" | 1987-06-05 | 2018-06-23 | "Red" | | "Sally Svensson" | 1987-06-05 | 2017-12-31 | "Sad" | | "Sally Svensson" | 1987-06-05 | 2017-12-25 | "Sore" | | "Sally Svensson" | 1987-06-05 | 2018-08-10 | "Dizzy" | | "Sally Svensson" | 1987-06-05 | 2017-12-31 | "Sad" | | "Sally Svensson" | 1987-06-05 | 2019-10-31 | "Angry" | | "Mark Smith" | 1991-08-30 | 2019-07-28 | "Swollen" | | "Mark Smith" | 1991-08-30 | 2019-01-14 | "Itchy" | | "Mark Smith" | 1991-08-30 | 2018-11-09 | "Sad" | | "Mark Smith" | 1991-08-30 | 2019-07-28 | "Swollen" | | "Mark Smith" | 1991-08-30 | 2019-06-09 | "Red" | | "Mark Smith" | 1991-08-30 | 2017-10-09 | "Scratchy" | | "Joe Stone" | 1999-08-23 | 2017-09-15 | "Itchy" | | "Joe Stone" | 1999-08-23 | 2019-08-12 | "Dizzy" | | "Joe Stone" | 1999-08-23 | 2018-12-06 | "Sore" | | "Joe Stone" | 1999-08-23 | 2018-06-04 | "Swollen" | | "Joe Stone" | 1999-08-23 | 2019-11-14 | "Inflamed" | | "Joe Stone" | 1999-08-23 | 2019-05-19 | "Scratchy" | | "Jane Anderson" | 1988-07-16 | 2019-08-15 | "Red" | | "Jane Anderson" | 1988-07-16 | 2018-09-26 | "Sore" | | "Jane Anderson" | 1988-07-16 | 2018-10-22 | "Pale" | | "Jane Anderson" | 1988-07-16 | 2018-03-20 | "Inflamed" | | "Jane Anderson" | 1988-07-16 | 2019-05-13 | "Dizzy" | | "Jane Anderson" | 1988-07-16 | 2019-05-13 | "Dizzy" | | "Bob Jackson" | 1974-09-23 | 2019-01-07 | "Sore" | | "Bob Jackson" | 1974-09-23 | 2017-10-13 | "Scratchy" | | "Bob Jackson" | 1974-09-23 | 2019-07-20 | "Swollen" | | "Bob Jackson" | 1974-09-23 | 2017-11-23 | "Red" | | "Bob Jackson" | 1974-09-23 | 2019-04-07 | "Sad" | | "Bob Jackson" | 1974-09-23 | 2019-08-23 | "Itchy" | | "Ally Svensson" | 2006-11-13 | 2018-07-22 | "Pale" | | "Ally Svensson" | 2006-11-13 | 2018-10-13 | "Itchy" | | "Ally Svensson" | 2006-11-13 | 2017-10-07 | "Sad" | | "Ally Svensson" | 2006-11-13 | 2018-10-13 | "Itchy" | | "Ally Svensson" | 2006-11-13 | 2018-06-20 | "Dizzy" | | "Ally Svensson" | 2006-11-13 | 2019-10-08 | "Scratchy" | | "Jack Smith" | 2017-05-17 | 2018-03-20 | "Red" | | "Jack Smith" | 2017-05-17 | 2019-01-13 | "Swollen" | | "Jack Smith" | 2017-05-17 | 2018-08-06 | "Itchy" | | "Jack Smith" | 2017-05-17 | 2018-07-18 | "Scratchy" | | "Jack Smith" | 2017-05-17 | 2018-06-10 | "Sore" | | "Jack Smith" | 2017-05-17 | 2018-03-20 | "Red" | | "Mary Stone" | 2011-06-20 | 2019-02-07 | "Pale" | | "Mary Stone" | 2011-06-20 | 2018-12-07 | "Itchy" | | "Mary Stone" | 2011-06-20 | 2019-09-17 | "Scratchy" | | "Mary Stone" | 2011-06-20 | 2017-08-02 | "Sore" | | "Mary Stone" | 2011-06-20 | 2019-09-17 | "Scratchy" | | "Mary Stone" | 2011-06-20 | 2019-02-07 | "Pale" | | "Sally Anderson" | 1970-12-02 | 2018-10-20 | "Swollen" | | "Sally Anderson" | 1970-12-02 | 2019-02-05 | "Scratchy" | | "Sally Anderson" | 1970-12-02 | 2019-11-12 | "Pale" | | "Sally Anderson" | 1970-12-02 | 2018-03-21 | "Angry" | | "Sally Anderson" | 1970-12-02 | 2019-07-21 | "Inflamed" | | "Sally Anderson" | 1970-12-02 | 2019-07-21 | "Inflamed" | | "Mark Jackson" | 2003-07-09 | 2018-12-20 | "Sore" | | "Mark Jackson" | 2003-07-09 | 2018-04-13 | "Itchy" | | "Mark Jackson" | 2003-07-09 | 2018-11-08 | "Inflamed" | | "Mark Jackson" | 2003-07-09 | 2019-09-17 | "Swollen" | | "Mark Jackson" | 2003-07-09 | 2018-04-11 | "Dizzy" | | "Mark Jackson" | 2003-07-09 | 2018-12-20 | "Sore" | | "Joe Svensson" | 2000-03-07 | 2019-01-31 | "Angry" | | "Joe Svensson" | 2000-03-07 | 2018-03-29 | "Sore" | | "Joe Svensson" | 2000-03-07 | 2019-10-26 | "Pale" | | "Joe Svensson" | 2000-03-07 | 2019-01-31 | "Angry" | | "Joe Svensson" | 2000-03-07 | 2018-01-01 | "Scratchy" | | "Joe Svensson" | 2000-03-07 | 2018-03-29 | "Sore" | | "Jane Smith" | 2012-05-14 | 2019-03-18 | "Pale" | | "Jane Smith" | 2012-05-14 | 2018-08-15 | "Swollen" | | "Jane Smith" | 2012-05-14 | 2018-01-16 | "Sore" | | "Jane Smith" | 2012-05-14 | 2018-03-14 | "Scratchy" | | "Jane Smith" | 2012-05-14 | 2018-05-23 | "Inflamed" | | "Jane Smith" | 2012-05-14 | 2019-07-06 | "Red" | | "Bob Stone" | 2011-06-07 | 2018-03-12 | "Itchy" | | "Bob Stone" | 2011-06-07 | 2018-05-20 | "Sad" | | "Bob Stone" | 2011-06-07 | 2017-08-12 | "Red" | | "Bob Stone" | 2011-06-07 | 2018-01-13 | "Swollen" | | "Bob Stone" | 2011-06-07 | 2019-01-13 | "Angry" | | "Bob Stone" | 2011-06-07 | 2018-03-12 | "Itchy" | | "Ally Anderson" | 1972-05-20 | 2018-09-27 | "Pale" | | "Ally Anderson" | 1972-05-20 | 2017-08-11 | "Inflamed" | | "Ally Anderson" | 1972-05-20 | 2017-08-23 | "Sad" | | "Ally Anderson" | 1972-05-20 | 2019-06-09 | "Dizzy" | | "Ally Anderson" | 1972-05-20 | 2018-10-08 | "Scratchy" | | "Ally Anderson" | 1972-05-20 | 2018-06-13 | "Swollen" | | "Jack Jackson" | 1985-09-11 | 2019-01-06 | "Red" | | "Jack Jackson" | 1985-09-11 | 2018-02-05 | "Sore" | | "Jack Jackson" | 1985-09-11 | 2018-09-10 | "Scratchy" | | "Jack Jackson" | 1985-09-11 | 2019-10-17 | "Dizzy" | | "Jack Jackson" | 1985-09-11 | 2018-07-07 | "Angry" | | "Jack Jackson" | 1985-09-11 | 2018-02-05 | "Sore" | | "Mary Svensson" | 1987-09-18 | 2018-08-06 | "Red" | | "Mary Svensson" | 1987-09-18 | 2018-03-03 | "Scratchy" | | "Mary Svensson" | 1987-09-18 | 2018-10-13 | "Sad" | | "Mary Svensson" | 1987-09-18 | 2019-02-03 | "Sore" | | "Mary Svensson" | 1987-09-18 | 2018-08-06 | "Red" | | "Mary Svensson" | 1987-09-18 | 2018-08-06 | "Red" | | "Sally Smith" | 2005-07-05 | 2018-05-26 | "Dizzy" | | "Sally Smith" | 2005-07-05 | 2018-11-02 | "Sad" | | "Sally Smith" | 2005-07-05 | 2018-05-26 | "Dizzy" | | "Sally Smith" | 2005-07-05 | 2017-10-26 | "Inflamed" | | "Sally Smith" | 2005-07-05 | 2018-07-24 | "Angry" | | "Sally Smith" | 2005-07-05 | 2018-05-26 | "Dizzy" | | "Mark Stone" | 2011-01-01 | 2019-01-24 | "Red" | | "Mark Stone" | 2011-01-01 | 2018-02-26 | "Scratchy" | | "Mark Stone" | 2011-01-01 | 2018-11-11 | "Swollen" | | "Mark Stone" | 2011-01-01 | 2017-12-16 | "Sore" | | "Mark Stone" | 2011-01-01 | 2018-02-26 | "Scratchy" | | "Mark Stone" | 2011-01-01 | 2019-09-13 | "Sad" | | "Joe Anderson" | 1981-12-16 | 2017-11-29 | "Pale" | | "Joe Anderson" | 1981-12-16 | 2018-12-13 | "Dizzy" | | "Joe Anderson" | 1981-12-16 | 2018-06-05 | "Swollen" | | "Joe Anderson" | 1981-12-16 | 2018-09-27 | "Sad" | | "Joe Anderson" | 1981-12-16 | 2017-09-12 | "Inflamed" | | "Joe Anderson" | 1981-12-16 | 2019-10-10 | "Sore" | | "Jane Jackson" | 1989-10-16 | 2019-04-22 | "Dizzy" | | "Jane Jackson" | 1989-10-16 | 2019-04-30 | "Swollen" | | "Jane Jackson" | 1989-10-16 | 2018-04-19 | "Red" | | "Jane Jackson" | 1989-10-16 | 2018-09-28 | "Inflamed" | | "Jane Jackson" | 1989-10-16 | 2019-07-19 | "Scratchy" | | "Jane Jackson" | 1989-10-16 | 2018-05-19 | "Sad" | | "Bob Svensson" | 2003-05-06 | 2019-11-05 | "Sore" | | "Bob Svensson" | 2003-05-06 | 2018-08-09 | "Scratchy" | | "Bob Svensson" | 2003-05-06 | 2018-11-22 | "Inflamed" | | "Bob Svensson" | 2003-05-06 | 2018-02-14 | "Angry" | | "Bob Svensson" | 2003-05-06 | 2018-11-22 | "Inflamed" | | "Bob Svensson" | 2003-05-06 | 2018-02-25 | "Itchy" | | "Ally Smith" | 1979-08-06 | 2019-10-25 | "Pale" | | "Ally Smith" | 1979-08-06 | 2019-11-25 | "Sore" | | "Ally Smith" | 1979-08-06 | 2019-10-19 | "Dizzy" | | "Ally Smith" | 1979-08-06 | 2018-01-06 | "Sad" | | "Ally Smith" | 1979-08-06 | 2019-03-12 | "Red" | | "Ally Smith" | 1979-08-06 | 2019-05-25 | "Itchy" | | "Jack Stone" | 2003-12-08 | 2019-04-29 | "Swollen" | | "Jack Stone" | 2003-12-08 | 2018-09-02 | "Scratchy" | | "Jack Stone" | 2003-12-08 | 2019-07-06 | "Itchy" | | "Jack Stone" | 2003-12-08 | 2019-07-06 | "Itchy" | | "Jack Stone" | 2003-12-08 | 2018-04-16 | "Pale" | | "Jack Stone" | 2003-12-08 | 2018-02-10 | "Sore" | | "Mary Anderson" | 1974-07-22 | 2018-06-08 | "Dizzy" | | "Mary Anderson" | 1974-07-22 | 2018-06-08 | "Dizzy" | | "Mary Anderson" | 1974-07-22 | 2019-12-02 | "Pale" | | "Mary Anderson" | 1974-07-22 | 2018-09-08 | "Angry" | | "Mary Anderson" | 1974-07-22 | 2018-07-05 | "Swollen" | | "Mary Anderson" | 1974-07-22 | 2018-03-08 | "Itchy" | | "Sally Jackson" | 1994-02-20 | 2019-07-19 | "Dizzy" | | "Sally Jackson" | 1994-02-20 | 2019-06-29 | "Pale" | | "Sally Jackson" | 1994-02-20 | 2019-06-14 | "Angry" | | "Sally Jackson" | 1994-02-20 | 2018-07-27 | "Red" | | "Sally Jackson" | 1994-02-20 | 2019-01-21 | "Sad" | | "Sally Jackson" | 1994-02-20 | 2018-10-25 | "Swollen" | | "Mark Svensson" | 1985-09-07 | 2018-01-06 | "Inflamed" | | "Mark Svensson" | 1985-09-07 | 2018-01-06 | "Inflamed" | | "Mark Svensson" | 1985-09-07 | 2019-04-04 | "Red" | | "Mark Svensson" | 1985-09-07 | 2018-04-02 | "Angry" | | "Mark Svensson" | 1985-09-07 | 2018-11-12 | "Itchy" | | "Mark Svensson" | 1985-09-07 | 2018-11-12 | "Itchy" | | "Joe Smith" | 1980-06-17 | 2018-10-23 | "Sore" | | "Joe Smith" | 1980-06-17 | 2018-03-19 | "Angry" | | "Joe Smith" | 1980-06-17 | 2018-03-19 | "Angry" | | "Joe Smith" | 1980-06-17 | 2019-02-12 | "Itchy" | | "Joe Smith" | 1980-06-17 | 2019-02-12 | "Itchy" | | "Joe Smith" | 1980-06-17 | 2019-09-17 | "Pale" | | "Jane Stone" | 2015-11-26 | 2019-04-27 | "Scratchy" | | "Jane Stone" | 2015-11-26 | 2017-09-21 | "Itchy" | | "Jane Stone" | 2015-11-26 | 2017-07-18 | "Inflamed" | | "Jane Stone" | 2015-11-26 | 2018-04-05 | "Pale" | | "Jane Stone" | 2015-11-26 | 2017-07-18 | "Inflamed" | | "Jane Stone" | 2015-11-26 | 2019-01-12 | "Swollen" | | "Bob Anderson" | 2007-02-06 | 2018-08-16 | "Itchy" | | "Bob Anderson" | 2007-02-06 | 2019-08-23 | "Inflamed" | | "Bob Anderson" | 2007-02-06 | 2018-08-31 | "Dizzy" | | "Bob Anderson" | 2007-02-06 | 2019-01-16 | "Sore" | | "Bob Anderson" | 2007-02-06 | 2018-08-31 | "Dizzy" | | "Bob Anderson" | 2007-02-06 | 2018-02-14 | "Angry" | | "Ally Jackson" | 1997-12-29 | 2018-03-10 | "Pale" | | "Ally Jackson" | 1997-12-29 | 2019-11-21 | "Red" | | "Ally Jackson" | 1997-12-29 | 2018-03-10 | "Pale" | | "Ally Jackson" | 1997-12-29 | 2019-11-21 | "Red" | | "Ally Jackson" | 1997-12-29 | 2018-09-20 | "Dizzy" | | "Ally Jackson" | 1997-12-29 | 2018-03-12 | "Itchy" | | "Jack Svensson" | 1974-04-26 | 2018-07-04 | "Sore" | | "Jack Svensson" | 1974-04-26 | 2019-06-15 | "Angry" | | "Jack Svensson" | 1974-04-26 | 2019-09-04 | "Inflamed" | | "Jack Svensson" | 1974-04-26 | 2017-08-12 | "Swollen" | | "Jack Svensson" | 1974-04-26 | 2018-07-04 | "Sore" | | "Jack Svensson" | 1974-04-26 | 2019-11-06 | "Itchy" | | "Mary Smith" | 2007-06-30 | 2018-06-13 | "Sad" | | "Mary Smith" | 2007-06-30 | 2019-06-21 | "Itchy" | | "Mary Smith" | 2007-06-30 | 2019-02-04 | "Dizzy" | | "Mary Smith" | 2007-06-30 | 2018-03-15 | "Angry" | | "Mary Smith" | 2007-06-30 | 2018-03-15 | "Angry" | | "Mary Smith" | 2007-06-30 | 2018-12-07 | "Sore" | | "Sally Stone" | 1999-06-21 | 2018-01-05 | "Sore" | | "Sally Stone" | 1999-06-21 | 2018-02-19 | "Angry" | | "Sally Stone" | 1999-06-21 | 2018-01-05 | "Sore" | | "Sally Stone" | 1999-06-21 | 2018-01-05 | "Sore" | | "Sally Stone" | 1999-06-21 | 2018-04-08 | "Scratchy" | | "Sally Stone" | 1999-06-21 | 2018-01-18 | "Dizzy" | | "Mark Anderson" | 1995-09-26 | 2018-03-04 | "Scratchy" | | "Mark Anderson" | 1995-09-26 | 2018-10-14 | "Sad" | | "Mark Anderson" | 1995-09-26 | 2019-05-16 | "Pale" | | "Mark Anderson" | 1995-09-26 | 2017-12-09 | "Swollen" | | "Mark Anderson" | 1995-09-26 | 2019-04-17 | "Inflamed" | | "Mark Anderson" | 1995-09-26 | 2019-05-16 | "Pale" | | "Joe Jackson" | 1973-06-05 | 2019-01-03 | "Scratchy" | | "Joe Jackson" | 1973-06-05 | 2018-08-29 | "Itchy" | | "Joe Jackson" | 1973-06-05 | 2019-07-06 | "Angry" | | "Joe Jackson" | 1973-06-05 | 2018-08-29 | "Itchy" | | "Joe Jackson" | 1973-06-05 | 2018-04-21 | "Dizzy" | | "Joe Jackson" | 1973-06-05 | 2018-06-21 | "Sore" | | "Jane Svensson" | 1970-05-24 | 2018-05-03 | "Sore" | | "Jane Svensson" | 1970-05-24 | 2019-02-12 | "Inflamed" | | "Jane Svensson" | 1970-05-24 | 2018-04-18 | "Angry" | | "Jane Svensson" | 1970-05-24 | 2019-04-12 | "Swollen" | | "Jane Svensson" | 1970-05-24 | 2018-12-08 | "Red" | | "Jane Svensson" | 1970-05-24 | 2017-11-17 | "Itchy" | | "Bob Smith" | 2014-07-07 | 2018-04-05 | "Dizzy" | | "Bob Smith" | 2014-07-07 | 2018-01-21 | "Red" | | "Bob Smith" | 2014-07-07 | 2018-04-05 | "Dizzy" | | "Bob Smith" | 2014-07-07 | 2018-04-05 | "Dizzy" | | "Bob Smith" | 2014-07-07 | 2018-02-04 | "Sad" | | "Bob Smith" | 2014-07-07 | 2019-05-01 | "Pale" | | "Ally Stone" | 1994-08-11 | 2017-10-17 | "Inflamed" | | "Ally Stone" | 1994-08-11 | 2017-08-20 | "Red" | | "Ally Stone" | 1994-08-11 | 2017-10-17 | "Inflamed" | | "Ally Stone" | 1994-08-11 | 2019-03-15 | "Angry" | | "Ally Stone" | 1994-08-11 | 2019-03-15 | "Angry" | | "Ally Stone" | 1994-08-11 | 2018-08-26 | "Swollen" | | "Jack Anderson" | 1994-08-22 | 2017-09-25 | "Inflamed" | | "Jack Anderson" | 1994-08-22 | 2019-10-18 | "Sad" | | "Jack Anderson" | 1994-08-22 | 2018-11-12 | "Swollen" | | "Jack Anderson" | 1994-08-22 | 2019-10-18 | "Sad" | | "Jack Anderson" | 1994-08-22 | 2018-11-12 | "Swollen" | | "Jack Anderson" | 1994-08-22 | 2018-09-29 | "Sore" | | "Mary Jackson" | 1993-02-17 | 2017-07-18 | "Scratchy" | | "Mary Jackson" | 1993-02-17 | 2019-09-15 | "Red" | | "Mary Jackson" | 1993-02-17 | 2018-05-28 | "Itchy" | | "Mary Jackson" | 1993-02-17 | 2018-05-28 | "Itchy" | | "Mary Jackson" | 1993-02-17 | 2018-09-28 | "Inflamed" | | "Mary Jackson" | 1993-02-17 | 2017-08-19 | "Sad" | | "Sally Svensson" | 2015-04-19 | 2017-11-15 | "Sad" | | "Sally Svensson" | 2015-04-19 | 2018-07-30 | "Sore" | | "Sally Svensson" | 2015-04-19 | 2017-11-15 | "Sad" | | "Sally Svensson" | 2015-04-19 | 2018-10-05 | "Pale" | | "Sally Svensson" | 2015-04-19 | 2019-06-14 | "Dizzy" | | "Sally Svensson" | 2015-04-19 | 2018-03-09 | "Scratchy" | | "Mark Smith" | 2012-08-01 | 2018-09-27 | "Swollen" | | "Mark Smith" | 2012-08-01 | 2018-06-25 | "Angry" | | "Mark Smith" | 2012-08-01 | 2019-01-08 | "Sore" | | "Mark Smith" | 2012-08-01 | 2018-09-20 | "Pale" | | "Mark Smith" | 2012-08-01 | 2019-09-30 | "Scratchy" | | "Mark Smith" | 2012-08-01 | 2018-09-20 | "Pale" | | "Joe Stone" | 2003-12-31 | 2018-01-29 | "Sore" | | "Joe Stone" | 2003-12-31 | 2017-10-01 | "Angry" | | "Joe Stone" | 2003-12-31 | 2019-07-16 | "Scratchy" | | "Joe Stone" | 2003-12-31 | 2018-03-03 | "Red" | | "Joe Stone" | 2003-12-31 | 2017-10-14 | "Dizzy" | | "Joe Stone" | 2003-12-31 | 2017-08-18 | "Pale" | | "Jane Anderson" | 2010-06-04 | 2019-12-02 | "Sore" | | "Jane Anderson" | 2010-06-04 | 2018-03-24 | "Scratchy" | | "Jane Anderson" | 2010-06-04 | 2018-07-20 | "Sad" | | "Jane Anderson" | 2010-06-04 | 2019-06-17 | "Swollen" | | "Jane Anderson" | 2010-06-04 | 2018-12-21 | "Red" | | "Jane Anderson" | 2010-06-04 | 2019-12-02 | "Sore" | | "Bob Jackson" | 1979-11-07 | 2018-05-03 | "Sore" | | "Bob Jackson" | 1979-11-07 | 2018-04-20 | "Angry" | | "Bob Jackson" | 1979-11-07 | 2018-05-10 | "Pale" | | "Bob Jackson" | 1979-11-07 | 2018-02-09 | "Swollen" | | "Bob Jackson" | 1979-11-07 | 2019-10-14 | "Scratchy" | | "Bob Jackson" | 1979-11-07 | 2018-04-23 | "Dizzy" | | "Ally Svensson" | 2004-12-14 | 2019-03-13 | "Scratchy" | | "Ally Svensson" | 2004-12-14 | 2019-03-13 | "Scratchy" | | "Ally Svensson" | 2004-12-14 | 2018-02-22 | "Inflamed" | | "Ally Svensson" | 2004-12-14 | 2018-05-16 | "Dizzy" | | "Ally Svensson" | 2004-12-14 | 2018-07-09 | "Pale" | | "Ally Svensson" | 2004-12-14 | 2019-04-30 | "Itchy" | | "Jack Smith" | 2010-09-23 | 2018-11-27 | "Angry" | | "Jack Smith" | 2010-09-23 | 2018-04-18 | "Pale" | | "Jack Smith" | 2010-09-23 | 2019-03-05 | "Itchy" | | "Jack Smith" | 2010-09-23 | 2018-09-29 | "Sore" | | "Jack Smith" | 2010-09-23 | 2019-02-08 | "Red" | | "Jack Smith" | 2010-09-23 | 2019-02-22 | "Sad" | | "Mary Stone" | 2009-07-14 | 2017-11-22 | "Pale" | | "Mary Stone" | 2009-07-14 | 2018-09-21 | "Scratchy" | | "Mary Stone" | 2009-07-14 | 2018-09-30 | "Angry" | | "Mary Stone" | 2009-07-14 | 2019-06-17 | "Itchy" | | "Mary Stone" | 2009-07-14 | 2017-11-22 | "Pale" | | "Mary Stone" | 2009-07-14 | 2019-08-14 | "Sore" | | "Sally Anderson" | 1972-01-23 | 2017-09-13 | "Dizzy" | | "Sally Anderson" | 1972-01-23 | 2018-09-09 | "Itchy" | | "Sally Anderson" | 1972-01-23 | 2018-06-23 | "Sad" | | "Sally Anderson" | 1972-01-23 | 2018-06-23 | "Sad" | | "Sally Anderson" | 1972-01-23 | 2019-12-03 | "Sore" | | "Sally Anderson" | 1972-01-23 | 2019-12-03 | "Sore" | | "Mark Jackson" | 2006-12-17 | 2018-08-02 | "Scratchy" | | "Mark Jackson" | 2006-12-17 | 2018-01-28 | "Sore" | | "Mark Jackson" | 2006-12-17 | 2018-08-02 | "Scratchy" | | "Mark Jackson" | 2006-12-17 | 2018-05-26 | "Itchy" | | "Mark Jackson" | 2006-12-17 | 2017-11-27 | "Sad" | | "Mark Jackson" | 2006-12-17 | 2017-07-17 | "Red" | | "Joe Svensson" | 2001-01-14 | 2019-02-20 | "Dizzy" | | "Joe Svensson" | 2001-01-14 | 2018-07-12 | "Angry" | | "Joe Svensson" | 2001-01-14 | 2018-08-08 | "Itchy" | | "Joe Svensson" | 2001-01-14 | 2018-03-30 | "Pale" | | "Joe Svensson" | 2001-01-14 | 2019-02-20 | "Dizzy" | | "Joe Svensson" | 2001-01-14 | 2018-03-30 | "Pale" | | "Jane Smith" | 1992-03-12 | 2017-10-07 | "Dizzy" | | "Jane Smith" | 1992-03-12 | 2019-03-07 | "Inflamed" | | "Jane Smith" | 1992-03-12 | 2019-05-30 | "Red" | | "Jane Smith" | 1992-03-12 | 2017-07-15 | "Pale" | | "Jane Smith" | 1992-03-12 | 2019-04-14 | "Sore" | | "Jane Smith" | 1992-03-12 | 2019-09-30 | "Angry" | | "Bob Stone" | 2015-09-07 | 2018-09-11 | "Sore" | | "Bob Stone" | 2015-09-07 | 2018-03-19 | "Dizzy" | | "Bob Stone" | 2015-09-07 | 2019-01-01 | "Scratchy" | | "Bob Stone" | 2015-09-07 | 2019-01-01 | "Scratchy" | | "Bob Stone" | 2015-09-07 | 2017-12-27 | "Sad" | | "Bob Stone" | 2015-09-07 | 2019-01-01 | "Scratchy" | | "Ally Anderson" | 1978-12-20 | 2018-08-20 | "Inflamed" | | "Ally Anderson" | 1978-12-20 | 2018-03-23 | "Sad" | | "Ally Anderson" | 1978-12-20 | 2017-09-05 | "Itchy" | | "Ally Anderson" | 1978-12-20 | 2018-01-07 | "Angry" | | "Ally Anderson" | 1978-12-20 | 2018-02-08 | "Pale" | | "Ally Anderson" | 1978-12-20 | 2018-02-08 | "Pale" | | "Jack Jackson" | 1975-06-08 | 2018-10-10 | "Red" | | "Jack Jackson" | 1975-06-08 | 2019-09-16 | "Pale" | | "Jack Jackson" | 1975-06-08 | 2019-09-16 | "Pale" | | "Jack Jackson" | 1975-06-08 | 2019-09-16 | "Pale" | | "Jack Jackson" | 1975-06-08 | 2019-01-06 | "Angry" | | "Jack Jackson" | 1975-06-08 | 2018-02-21 | "Scratchy" | | "Mary Svensson" | 2002-01-09 | 2018-09-24 | "Pale" | | "Mary Svensson" | 2002-01-09 | 2018-03-03 | "Itchy" | | "Mary Svensson" | 2002-01-09 | 2017-12-29 | "Swollen" | | "Mary Svensson" | 2002-01-09 | 2019-11-01 | "Sad" | | "Mary Svensson" | 2002-01-09 | 2018-03-03 | "Itchy" | | "Mary Svensson" | 2002-01-09 | 2018-03-03 | "Itchy" | | "Sally Smith" | 1973-12-03 | 2018-01-06 | "Itchy" | | "Sally Smith" | 1973-12-03 | 2018-01-06 | "Itchy" | | "Sally Smith" | 1973-12-03 | 2019-02-13 | "Dizzy" | | "Sally Smith" | 1973-12-03 | 2019-10-21 | "Pale" | | "Sally Smith" | 1973-12-03 | 2017-10-26 | "Scratchy" | | "Sally Smith" | 1973-12-03 | 2017-12-21 | "Red" | | "Mark Stone" | 1988-06-07 | 2018-06-07 | "Swollen" | | "Mark Stone" | 1988-06-07 | 2019-09-06 | "Scratchy" | | "Mark Stone" | 1988-06-07 | 2018-08-09 | "Itchy" | | "Mark Stone" | 1988-06-07 | 2019-09-06 | "Scratchy" | | "Mark Stone" | 1988-06-07 | 2019-06-12 | "Dizzy" | | "Mark Stone" | 1988-06-07 | 2019-09-06 | "Scratchy" | | "Joe Anderson" | 2010-10-05 | 2018-01-05 | "Pale" | | "Joe Anderson" | 2010-10-05 | 2017-12-26 | "Scratchy" | | "Joe Anderson" | 2010-10-05 | 2018-01-05 | "Pale" | | "Joe Anderson" | 2010-10-05 | 2019-04-11 | "Inflamed" | | "Joe Anderson" | 2010-10-05 | 2019-01-02 | "Sore" | | "Joe Anderson" | 2010-10-05 | 2019-02-28 | "Dizzy" | +------------------------------------------------------------+ 606 rows ready to start consuming query after 91 ms, results consumed after another 60 ms Created 491 relationships, Set 491 properties
Manage authorization and access control
Unlike applications which often require users to be modeled within the application itself, databases provide user management resources such as roles and privileges. This allows users to be created entirely within the database security model, a strategy that allows the separation of access to the data and the data itself. For more information, see Authentication and authorization.
In this tutorial, consider five users of the healthcare database:
-
Alice, the doctor.
-
Daniel, the nurse.
-
Bob, the receptionist.
-
Charlie, the researcher.
-
Tina, the IT administrator.
You can create these users by using the CREATE USER command (from the system database):
CREATE USER charlie SET PASSWORD 'secretpassword1' CHANGE NOT REQUIRED;
CREATE USER alice SET PASSWORD 'secretpassword2' CHANGE NOT REQUIRED;
CREATE USER daniel SET PASSWORD 'secretpassword3' CHANGE NOT REQUIRED;
CREATE USER bob SET PASSWORD 'secretpassword4' CHANGE NOT REQUIRED;
CREATE USER tina SET PASSWORD 'secretpassword5' CHANGE NOT REQUIRED;At this point, the users cannot interact with the database, so these capabilities need to be granted by using roles. There are two different ways of doing this either by using built-in roles and privileges or by using more advanced resources with fine-grained privileges for sub-graph access control.
Access control using built-in roles
Neo4j comes with built-in roles that cover a number of common needs:
-
PUBLIC- All users have this role. They can by default access the home database, load data, and run all procedures and user-defined functions. -
reader- Can read data from all databases. -
editor- Can read and update all databases, but not expand the schema with new labels, relationship types, or property names. -
publisher- Can read and edit, as well as add new labels, relationship types, and property names. -
architect- Has all the capabilities of the publisher as well as the ability to manage indexes and constraints. -
admin- Can perform architect actions as well as load data and manage databases, users, roles, and privileges.
Consider Charlie from the example of users.
As a researcher, they do not need write access to the database, so they are assigned the reader role.
On the other hand, Alice (the doctor), Daniel (the nurse), and Bob (the receptionist) all need to update the database with new patient information but do not need to expand the schema with new labels, relationship types, property names, or indexes.
For this reason, they are all assigned the editor role.
Tina, the IT administrator who installs and manages the database, needs to be assigned the admin role.
Here is how to grant roles to the users (from the system database):
GRANT ROLE reader TO charlie;
GRANT ROLE editor TO alice;
GRANT ROLE editor TO daniel;
GRANT ROLE editor TO bob;
GRANT ROLE admin TO tina;Sub-graph access control using privileges
A limitation of the previously described approach is that it does allow all users to see all the data on the database. In many real-world scenarios though, it would be preferable to establish some access restrictions.
For example, you may want to limit the researcher’s access to the patients' personal information or restrict the receptionist from writing new labels on the database. While these restrictions could be coded into the application layer, it is possible and more secure to enforce fine-grained restrictions directly within the Neo4j security model by creating custom roles and assigning specific privileges to them.
Since new custom roles will be created, it is important to first revoke the current roles from the users assigned to them.
Run the following command against the system database:
REVOKE ROLE reader FROM charlie;
REVOKE ROLE editor FROM alice;
REVOKE ROLE editor FROM daniel;
REVOKE ROLE editor FROM bob;
REVOKE ROLE admin FROM tina;Now you can create custom roles based on the concept of privileges, which allows more control over what each user is capable of doing. To properly assign those privileges, start by identifying each type of user:
- Doctor
-
Should be able to read and write most of the graph, but be prevented from reading the patients' address. Has the permission to save diagnoses to the database, but not expand the schema with new concepts.
- Receptionist
-
Should be able to read and write all patient data, but not be able to see the symptoms, diseases, or diagnoses.
- Researcher
-
Should be able to perform statistical analysis of all data, except patients’ personal information, to which they should have restricted access. To illustrate two different ways of setting up the same effective privileges, two roles are created for comparison.
- Nurse
-
Should be able to perform all tasks that both the doctor and the receptionist can do. Granting both roles (doctor and receptionist) to the nurse does not work as expected. This is explained in the section dedicated to the creation of the
nurserole. - Junior nurse
-
While the senior nurse is able to save diagnoses just as a doctor can, some (junior) nurses might not be allowed to do that. Creating another role from scratch is an option, but the same output can be achieved by combining the
nurserole with a newdisableDiagnosesrole that specifically restricts that activity. - IT administrator
-
This role is very similar to the built-in
adminrole, except that it should not allow access to the patients'SSNor be able to save a diagnosis, a privilege restricted to medical professionals. To achieve this, the built-inadminrole can be copied and modified accordingly. - User manager
-
This user should have similar access as the IT administrator, but with more restrictions. To achieve that, a new role can be created from scratch and only specific administrative capabilities can be assigned to it.
Before creating the new roles and assigning them to Alice, Bob, Daniel, Charlie, and Tina, it is important to define the privileges each role should have.
Since all users need ACCESS privilege to the healthcare database, this can be set through the PUBLIC role instead of all the individual roles:
Run the following command against the system database:
GRANT ACCESS ON DATABASE healthcare TO PUBLIC;Privileges of itadmin
This role can be created as a copy of the built-in admin role:
CREATE ROLE itadmin AS COPY OF admin;Then you need to deny the two specific actions this role is not supposed to perform:
-
Read any patients' social security number (
SSN). -
Submit medical diagnoses.
As well as the ability for the itadmin to amend their own privileges.
DENY READ {ssn} ON GRAPH healthcare NODES Patient TO itadmin;
DENY CREATE ON GRAPH healthcare RELATIONSHIPS DIAGNOSIS TO itadmin;
DENY ROLE MANAGEMENT ON DBMS TO itadmin;
DENY PRIVILEGE MANAGEMENT ON DBMS TO itadmin;The complete set of privileges available to users assigned the itadmin role can be viewed using the following command:
SHOW ROLE itadmin PRIVILEGES AS COMMANDS;Result
+-------------------------------------------------------------------------+
| command |
+-------------------------------------------------------------------------+
| "DENY CREATE ON GRAPH `healthcare` RELATIONSHIP DIAGNOSIS TO `itadmin`" |
| "DENY PRIVILEGE MANAGEMENT ON DBMS TO `itadmin`" |
| "DENY READ {ssn} ON GRAPH `healthcare` NODE Patient TO `itadmin`" |
| "DENY ROLE MANAGEMENT ON DBMS TO `itadmin`" |
| "GRANT ACCESS ON DATABASE * TO `itadmin`" |
| "GRANT ALL DBMS PRIVILEGES ON DBMS TO `itadmin`" |
| "GRANT CONSTRAINT MANAGEMENT ON DATABASE * TO `itadmin`" |
| "GRANT INDEX MANAGEMENT ON DATABASE * TO `itadmin`" |
| "GRANT LOAD ON ALL DATA TO `itadmin`" |
| "GRANT MATCH {*} ON GRAPH * NODE * TO `itadmin`" |
| "GRANT MATCH {*} ON GRAPH * RELATIONSHIP * TO `itadmin`" |
| "GRANT NAME MANAGEMENT ON DATABASE * TO `itadmin`" |
| "GRANT SHOW CONSTRAINT ON DATABASE * TO `itadmin`" |
| "GRANT SHOW INDEX ON DATABASE * TO `itadmin`" |
| "GRANT START ON DATABASE * TO `itadmin`" |
| "GRANT STOP ON DATABASE * TO `itadmin`" |
| "GRANT TRANSACTION MANAGEMENT (*) ON DATABASE * TO `itadmin`" |
| "GRANT WRITE ON GRAPH * TO `itadmin`" |
+-------------------------------------------------------------------------+
18 rows
ready to start consuming query after 29 ms, results consumed after another 1 ms
|
Privileges that were granted or denied earlier can be revoked using the |
To provide the IT administrator tina these privileges, they must be assigned the new role itadmin.
Run the following command against the system database:
GRANT ROLE itadmin TO tina;To demonstrate that Tina is not able to see the patients' SSN, you can log into Cypher Shell as tina and run the following query against the healthcare database:
MATCH (n:Patient)
WHERE n.dateOfBirth < date('1972-06-12')
RETURN n.name, n.ssn, n.address, n.dateOfBirth;+---------------------------------------------------------------------+ | n.name | n.ssn | n.address | n.dateOfBirth | +---------------------------------------------------------------------+ | "Mark Jackson" | NULL | "1 secret way, downtown" | 1970-11-29 | | "Joe Svensson" | NULL | "1 secret way, downtown" | 1972-02-12 | | "Bob Anderson" | NULL | "1 secret way, downtown" | 1970-04-27 | | "Sally Anderson" | NULL | "1 secret way, downtown" | 1970-12-02 | | "Ally Anderson" | NULL | "1 secret way, downtown" | 1972-05-20 | | "Jane Svensson" | NULL | "1 secret way, downtown" | 1970-05-24 | | "Sally Anderson" | NULL | "1 secret way, downtown" | 1972-01-23 | +---------------------------------------------------------------------+ 7 rows ready to start consuming query after 49 ms, results consumed after another 2 ms
The results make it seem as if these nodes do not even have an SSN field.
This is a key feature of the security model: users cannot tell the difference between data that does not exist and data that is hidden using fine-grained read privileges.
Now recall that the itadmin role was denied the ability to save diagnoses (as this is a critical medical function reserved for only doctors and senior medical staff), you can test this by trying to create DIAGNOSIS relationships:
MATCH (n:Patient), (d:Disease)
CREATE (n)-[:DIAGNOSIS]->(d);Create relationship with type 'DIAGNOSIS' on database 'healthcare' is not allowed for user 'tina' with roles [PUBLIC, itadmin].
|
Restrictions to reading data do not result in errors, they only make it appear as if the data is not there. However, restrictions on updating the graph do output an appropriate error when the user attempts to perform an action they are not allowed to. |
Privileges of researcher
The researcher Charlie was previously a read-only user.
To assign them the desired permissions, you can do something similar to what was done with the itadmin role, this time copying and modifying the reader role.
Another way to do it is by creating a new role from scratch and then either granting or denying a list of privileges:
-
Denying privileges:
You can grant the role
researcherthe ability to find all nodes and read all properties (much like thereaderrole), but deny read access to thePatientproperties. This way, the researcher is unable to see patients' information such asname,SSN, andaddress. This approach has a problem though: if more properties are added to thePatientnodes after the restrictions were assigned to theresearcherrole, these new properties will automatically be visible to the researcher — a possibly undesirable outcome.To avoid that, you can rather deny specific privileges by running the following commands against the
systemdatabase. You must be logged in as a user with theadminrole to be able to execute these commands:// First create the role CREATE ROLE researcherB; // Then grant access to everything GRANT MATCH {*} ON GRAPH healthcare TO researcherB; // And deny read on specific node properties DENY READ {name, address, ssn} ON GRAPH healthcare NODES Patient TO researcherB; // And finally deny traversal of the doctors diagnosis DENY TRAVERSE ON GRAPH healthcare RELATIONSHIPS DIAGNOSIS TO researcherB; -
Granting privileges:
Another alternative is to only provide specific access to the properties the researcher is allowed to see. This way, the addition of new properties (for instance, to a
Patientnode) does not automatically make them visible to users assigned with this role. In case you wish to make them visible though, you need to explicitly grant read access. Run the following commands against thesystemdatabase. You must be logged in as a user with theadminrole to be able to execute these commands:// Create the role first CREATE ROLE researcherW // Allow the researcher to find all nodes GRANT TRAVERSE ON GRAPH healthcare NODES * TO researcherW; // Now only allow the researcher to traverse specific relationships GRANT TRAVERSE ON GRAPH healthcare RELATIONSHIPS HAS, OF TO researcherW; // Allow reading of all properties of medical metadata GRANT READ {*} ON GRAPH healthcare NODES Symptom, Disease TO researcherW; // Allow reading of all properties of the disease-symptom relationship GRANT READ {*} ON GRAPH healthcare RELATIONSHIPS OF TO researcherW; // Only allow reading dateOfBirth for research purposes GRANT READ {dateOfBirth} ON GRAPH healthcare NODES Patient TO researcherW;In order to test that the researcher Charlie now has the specified privileges, assign them the
researcherBrole (with specifically denied privileges):GRANT ROLE researcherB TO charlie;You can also use a version of the
SHOW PRIVILEGEScommand to see Charlie’s access rights, which are a combination of those assigned to theresearcherBandPUBLICroles:SHOW USER charlie PRIVILEGES AS COMMANDS;Result+-----------------------------------------------------------------------+ | command | +-----------------------------------------------------------------------+ | "DENY READ {address} ON GRAPH `healthcare` NODE Patient TO $role" | | "DENY READ {name} ON GRAPH `healthcare` NODE Patient TO $role" | | "DENY READ {ssn} ON GRAPH `healthcare` NODE Patient TO $role" | | "DENY TRAVERSE ON GRAPH `healthcare` RELATIONSHIP DIAGNOSIS TO $role" | | "GRANT ACCESS ON DATABASE `healthcare` TO $role" | | "GRANT ACCESS ON HOME DATABASE TO $role" | | "GRANT EXECUTE FUNCTION * ON DBMS TO $role" | | "GRANT EXECUTE PROCEDURE * ON DBMS TO $role" | | "GRANT LOAD ON ALL DATA TO $role" | | "GRANT MATCH {*} ON GRAPH `healthcare` NODE * TO $role" | | "GRANT MATCH {*} ON GRAPH `healthcare` RELATIONSHIP * TO $role" | +-----------------------------------------------------------------------+ 11 rows ready to start consuming query after 17 ms, results consumed after another 2 msNow when Charlie logs into Cypher Shell and tries to execute the following command against the
healthcaredatabase, even though the command is similar to the one previously used by theitadmin, they will see different results:MATCH (n:Patient) WHERE n.dateOfBirth < date('1972-06-12') RETURN n.name, n.ssn, n.address, n.dateOfBirth;Result+--------------------------------------------+ | n.name | n.ssn | n.address | n.dateOfBirth | +--------------------------------------------+ | NULL | NULL | NULL | 1970-11-29 | | NULL | NULL | NULL | 1972-02-12 | | NULL | NULL | NULL | 1970-04-27 | | NULL | NULL | NULL | 1970-12-02 | | NULL | NULL | NULL | 1972-05-20 | | NULL | NULL | NULL | 1970-05-24 | | NULL | NULL | NULL | 1972-01-23 | +--------------------------------------------+ 7 rows ready to start consuming query after 5 ms, results consumed after another 4 ms
Only the date of birth is available, so that the researcher Charlie may perform statistical analysis, for example. Another query Charlie could try is to find the ten diseases a patient younger than 25 is most likely to be diagnosed with, listed by probability:
WITH datetime() - duration({years:25}) AS timeLimit MATCH (n:Patient) WHERE n.dateOfBirth > date(timeLimit) MATCH (n)-[h:HAS]->(s:Symptom)-[o:OF]->(d:Disease) WITH d.name AS disease, o.probability AS prob RETURN disease, sum(prob) AS score ORDER BY score DESC LIMIT 10;Result+-------------------------------------------+ | disease | score | +-------------------------------------------+ | "Acute Placeboitis" | 98.08269474672981 | | "Chronic Whatitis" | 92.7601237335886 | | "Acute Otheritis" | 87.61578906815608 | | "Chronic Someitis" | 81.68350008637253 | | "Chronic Placeboitis" | 81.18800771016768 | | "Acute Argitis" | 80.94323685188083 | | "Chronic Argitis" | 80.06685163653665 | | "Chronic Otheritis" | 76.06538667789484 | | "Acute Yellowitis" | 70.74589062185173 | | "Acute Someitis" | 70.3238679154795 | +-------------------------------------------+ 10 rows ready to start consuming query after 171 ms, results consumed after another 23 ms
If the
researcherBrole is revoked to Charlie, butresearcherWis granted, when re-running these queries, the same results will be obtained.Privileges that were granted or denied earlier can be revoked using the
REVOKEcommand.
Privileges of doctor
Doctors should be given the ability to read and write almost everything, except the patients' address property, for instance.
This role can be built from scratch by assigning full read and write access, and then specifically denying access to the address property.
Switch to the system database and run the following commands:
CREATE ROLE doctor;
GRANT TRAVERSE ON GRAPH healthcare TO doctor;
GRANT READ {*} ON GRAPH healthcare TO doctor;
GRANT WRITE ON GRAPH healthcare TO doctor;
DENY READ {address} ON GRAPH healthcare NODES Patient TO doctor;
DENY SET PROPERTY {address} ON GRAPH healthcare NODES Patient TO doctor;To allow the doctor Alice to have these privileges, grant the user alice this new role:
GRANT ROLE doctor TO alice;To demonstrate that Alice is not able to see patient addresses, log in as alice and run the following query against the healthcare database:
MATCH (n:Patient)
WHERE n.dateOfBirth < date('1972-06-12')
RETURN n.name, n.ssn, n.address, n.dateOfBirth;+--------------------------------------------------------+ | n.name | n.ssn | n.address | n.dateOfBirth | +--------------------------------------------------------+ | "Mark Jackson" | 1234578 | NULL | 1970-11-29 | | "Joe Svensson" | 1234579 | NULL | 1972-02-12 | | "Bob Anderson" | 1234597 | NULL | 1970-04-27 | | "Sally Anderson" | 1234617 | NULL | 1970-12-02 | | "Ally Anderson" | 1234622 | NULL | 1972-05-20 | | "Jane Svensson" | 1234644 | NULL | 1970-05-24 | | "Sally Anderson" | 1234657 | NULL | 1972-01-23 | +--------------------------------------------------------+ 7 rows ready to start consuming query after 5 ms, results consumed after another 3 ms
As a result, the doctor has the expected privileges, including being able to see the patients' SSN, but not their address.
The doctor is also able to see all other node types:
MATCH (n) WITH labels(n) AS labels
RETURN labels, count(*);+------------------------+ | labels | count(*) | +------------------------+ | ["Symptom"] | 10 | | ["Disease"] | 12 | | ["Patient"] | 101 | +------------------------+ 3 rows ready to start consuming query after 29 ms, results consumed after another 1 ms
In addition, the doctor can traverse the graph, finding symptoms and diseases connected to patients:
MATCH (n:Patient)-[:HAS]->(s:Symptom)-[:OF]->(d:Disease)
WHERE n.ssn = 1234657
RETURN n.name, d.name, count(s) AS score ORDER BY score DESC;The resulting table shows which are the most likely diagnoses based on symptoms. The doctor can use this table to facilitate further questioning and testing of the patient in order to decide on the final diagnosis.
+--------------------------------------------------+ | n.name | d.name | score | +--------------------------------------------------+ | "Sally Anderson" | "Acute Placeboitis" | 4 | | "Sally Anderson" | "Chronic Argitis" | 2 | | "Sally Anderson" | "Acute Argitis" | 2 | | "Sally Anderson" | "Acute Otheritis" | 2 | | "Sally Anderson" | "Chronic Placeboitis" | 2 | | "Sally Anderson" | "Acute Yellowitis" | 2 | | "Sally Anderson" | "Chronic Whatitis" | 2 | | "Sally Anderson" | "Chronic Yellowitis" | 2 | | "Sally Anderson" | "Acute Whatitis" | 1 | | "Sally Anderson" | "Acute Someitis" | 1 | | "Sally Anderson" | "Chronic Someitis" | 1 | | "Sally Anderson" | "Chronic Otheritis" | 1 | +--------------------------------------------------+ 12 rows ready to start consuming query after 48 ms, results consumed after another 2 ms
Once the doctor has investigated further, they would be able to decide on the diagnosis and save that result to the database:
WITH datetime({epochmillis:timestamp()}) AS now
WITH now, date(now) as today
MATCH (p:Patient)
WHERE p.ssn = 1234657
MATCH (d:Disease)
WHERE d.name = "Chronic Placeboitis"
MERGE (p)-[i:DIAGNOSIS {by: 'Alice'}]->(d)
ON CREATE SET i.created_at = now, i.updated_at = now, i.date = today
ON MATCH SET i.updated_at = now
RETURN p.name, d.name, i.by, i.date, duration.between(i.created_at, i.updated_at) AS updated;This allows the doctor to record their diagnosis as well as take note of previous diagnoses:
+---------------------------------------------------------------------------+ | p.name | d.name | i.by | i.date | updated | +---------------------------------------------------------------------------+ | "Sally Anderson" | "Chronic Placeboitis" | "Alice" | 2025-02-14 | PT0S | +---------------------------------------------------------------------------+ 1 row ready to start consuming query after 73 ms, results consumed after another 6 ms Created 1 relationships, Set 4 properties
|
Creating the |
Privileges of receptionist
Receptionists should only be able to manage patient information.
They are not allowed to find or read any other parts of the graph.
In addition, they should be able to create and delete patients, but not any other nodes.
Switch to the system database and run the following commands:
CREATE ROLE receptionist;
GRANT MATCH {*} ON GRAPH healthcare NODES Patient TO receptionist;
GRANT CREATE ON GRAPH healthcare NODES Patient TO receptionist;
GRANT DELETE ON GRAPH healthcare NODES Patient TO receptionist;
GRANT SET PROPERTY {*} ON GRAPH healthcare NODES Patient TO receptionist;It would have been simpler to grant global WRITE privileges to the receptionist Bob.
However, this would have the unfortunate side effect of allowing them the ability to create other nodes, like new Symptom nodes, even though they would subsequently be unable to find or read those same nodes.
While there are use cases in which it is desirable to have roles able to create data they cannot read, that is not the case of this model.
With that in mind, grant the receptionist Bob their new receptionist role:
GRANT ROLE receptionist TO bob;With these privileges, if Bob tries to read the entire database, he will still only see the patients:
MATCH (n) WITH labels(n) AS labels
RETURN labels, count(*);+------------------------+ | labels | count(*) | +------------------------+ | ["Patient"] | 101 | +------------------------+ 1 row ready to start consuming query after 2 ms, results consumed after another 3 ms
However, Bob is able to see all fields of the patients' records:
MATCH (n:Patient)
WHERE n.dateOfBirth < date('1972-06-12')
RETURN n.name, n.ssn, n.address, n.dateOfBirth;+-----------------------------------------------------------------------+ | n.name | n.ssn | n.address | n.dateOfBirth | +-----------------------------------------------------------------------+ | "Mark Jackson" | 1234578 | "1 secret way, downtown" | 1970-11-29 | | "Joe Svensson" | 1234579 | "1 secret way, downtown" | 1972-02-12 | | "Bob Anderson" | 1234597 | "1 secret way, downtown" | 1970-04-27 | | "Sally Anderson" | 1234617 | "1 secret way, downtown" | 1970-12-02 | | "Ally Anderson" | 1234622 | "1 secret way, downtown" | 1972-05-20 | | "Jane Svensson" | 1234644 | "1 secret way, downtown" | 1970-05-24 | | "Sally Anderson" | 1234657 | "1 secret way, downtown" | 1972-01-23 | +-----------------------------------------------------------------------+ 7 rows ready to start consuming query after 2 ms, results consumed after another 1 ms
With the receptionist role, Bob can delete any new patient nodes they have just created, but they are not able to delete patients that have already received diagnoses since those are connected to parts of the graph that Bob cannot see.
Here is a demonstration of both scenarios:
CREATE (n:Patient {
ssn:87654321,
name: 'Another Patient',
email: 'another@example.com',
address: '1 secret way, downtown',
dateOfBirth: date('2001-01-20')
})
RETURN n.name, n.dateOfBirth;+-----------------------------------+ | n.name | n.dateOfBirth | +-----------------------------------+ | "Another Patient" | 2001-01-20 | +-----------------------------------+ 1 row ready to start consuming query after 36 ms, results consumed after another 1 ms Added 1 nodes, Set 5 properties, Added 1 labels
The receptionist is able to modify any patient record:
MATCH (n:Patient)
WHERE n.ssn = 87654321
SET n.address = '2 streets down, uptown'
RETURN n.name, n.dateOfBirth, n.address;+--------------------------------------------------------------+ | n.name | n.dateOfBirth | n.address | +--------------------------------------------------------------+ | "Another Patient" | 2001-01-20 | "2 streets down, uptown" | +--------------------------------------------------------------+ 1 row ready to start consuming query after 22 ms, results consumed after another 3 ms Set 1 properties
The receptionist is also able to delete this recently created patient because it is not connected to any other records:
MATCH (n:Patient)
WHERE n.ssn = 87654321
DETACH DELETE n;0 rows ready to start consuming query after 17 ms, results consumed after another 0 ms Deleted 1 nodes
However, if the receptionist attempts to delete a patient that has existing diagnoses, this will fail:
MATCH (n:Patient)
WHERE n.ssn = 1234610
DETACH DELETE n;Cannot delete node<65>, because it still has relationships. To delete this node, you must first delete its relationships.
The reason why this query fails is that, while Bob can find the (:Patient) node, he does not have sufficient traverse rights to find nor the rights to delete the outgoing relationships from it.
Either they need to ask Tina the itadmin for help for this task, or more privileges can be added to the receptionist role.
Switch to the system database and run the following commands:
GRANT TRAVERSE ON GRAPH healthcare NODES Symptom, Disease TO receptionist;
GRANT TRAVERSE ON GRAPH healthcare RELATIONSHIPS HAS, DIAGNOSIS TO receptionist;
GRANT DELETE ON GRAPH healthcare RELATIONSHIPS HAS, DIAGNOSIS TO receptionist;|
Privileges that were granted or denied earlier can be revoked using the |
Privileges of nurse
Nurses should have the capabilities of both doctors and receptionists, but assigning them both the doctor and receptionist roles might not have the expected effect.
If those two roles were created with GRANT privileges only, combining them would be simply cumulative.
But if the doctor role contains some DENY privileges, these always overrule GRANT.
This means that the nurse will still have the same restrictions as a doctor, which is not what is intended here.
To demonstrate this, you can assign the doctor role to the nurse Daniel.
Switch to the system database and run the following commands:
GRANT ROLE doctor, receptionist TO daniel;Daniel should now have a combined set of privileges:
SHOW USER daniel PRIVILEGES AS COMMANDS;+---------------------------------------------------------------------------+
| command |
+---------------------------------------------------------------------------+
| "DENY READ {address} ON GRAPH `healthcare` NODE Patient TO $role" |
| "DENY SET PROPERTY {address} ON GRAPH `healthcare` NODE Patient TO $role" |
| "GRANT ACCESS ON DATABASE `healthcare` TO $role" |
| "GRANT ACCESS ON HOME DATABASE TO $role" |
| "GRANT CREATE ON GRAPH `healthcare` NODE Patient TO $role" |
| "GRANT DELETE ON GRAPH `healthcare` NODE Patient TO $role" |
| "GRANT DELETE ON GRAPH `healthcare` RELATIONSHIP DIAGNOSIS TO $role" |
| "GRANT DELETE ON GRAPH `healthcare` RELATIONSHIP HAS TO $role" |
| "GRANT EXECUTE FUNCTION * ON DBMS TO $role" |
| "GRANT EXECUTE PROCEDURE * ON DBMS TO $role" |
| "GRANT LOAD ON ALL DATA TO $role" |
| "GRANT MATCH {*} ON GRAPH `healthcare` NODE Patient TO $role" |
| "GRANT READ {*} ON GRAPH `healthcare` NODE * TO $role" |
| "GRANT READ {*} ON GRAPH `healthcare` RELATIONSHIP * TO $role" |
| "GRANT SET PROPERTY {*} ON GRAPH `healthcare` NODE Patient TO $role" |
| "GRANT TRAVERSE ON GRAPH `healthcare` NODE * TO $role" |
| "GRANT TRAVERSE ON GRAPH `healthcare` NODE Disease TO $role" |
| "GRANT TRAVERSE ON GRAPH `healthcare` NODE Symptom TO $role" |
| "GRANT TRAVERSE ON GRAPH `healthcare` RELATIONSHIP * TO $role" |
| "GRANT TRAVERSE ON GRAPH `healthcare` RELATIONSHIP DIAGNOSIS TO $role" |
| "GRANT TRAVERSE ON GRAPH `healthcare` RELATIONSHIP HAS TO $role" |
| "GRANT WRITE ON GRAPH `healthcare` TO $role" |
+---------------------------------------------------------------------------+
22 rows
ready to start consuming query after 10 ms, results consumed after another 1 ms
|
Privileges that were granted or denied earlier can be revoked using the |
Now the intention is that a nurse can perform the actions of a receptionist, which means they should be able to read and write the address field of the Patient nodes.
Log in as daniel and run the following query against the healthcare database:
MATCH (n:Patient)
WHERE n.dateOfBirth < date('1972-06-12')
RETURN n.name, n.ssn, n.address, n.dateOfBirth;+--------------------------------------------------------+ | n.name | n.ssn | n.address | n.dateOfBirth | +--------------------------------------------------------+ | "Mark Jackson" | 1234578 | NULL | 1970-11-29 | | "Joe Svensson" | 1234579 | NULL | 1972-02-12 | | "Bob Anderson" | 1234597 | NULL | 1970-04-27 | | "Sally Anderson" | 1234617 | NULL | 1970-12-02 | | "Ally Anderson" | 1234622 | NULL | 1972-05-20 | | "Jane Svensson" | 1234644 | NULL | 1970-05-24 | | "Sally Anderson" | 1234657 | NULL | 1972-01-23 | +--------------------------------------------------------+ 7 rows ready to start consuming query after 4 ms, results consumed after another 2 ms
As expected, the address field is invisible to the nurse.
This happens because, as previously described, DENY privileges always overrule GRANT.
Since both roles doctor and receptionist were assigned to the nurse, the DENIED privileges of the doctor role are overruling the GRANTED privileges of the receptionist.
Even if the nurse tries to write the address field, they would receive an error, and that is not what is desired here.
To correct that, you can:
-
Redefine the
doctorrole with only grants and define eachPatientproperty the doctor should be able to read. -
Redefine the
nurserole with the actual intended behavior.
The second option is simpler if you consider that the nurse is essentially the doctor without the address restrictions.
In this case, you need to create a nurse role from scratch.
Switch to the system database and run the following commands:
CREATE ROLE nurse;
GRANT TRAVERSE ON GRAPH healthcare TO nurse;
GRANT READ {*} ON GRAPH healthcare TO nurse;
GRANT WRITE ON GRAPH healthcare TO nurse;Now you assign the nurse role to the nurse Daniel, but remember to revoke the doctor and the receptionist roles so there are no privileges being overridden:
REVOKE ROLE doctor FROM daniel;
REVOKE ROLE receptionist FROM daniel;
GRANT ROLE nurse TO daniel;This time, when the nurse Daniel logs in and runs the following query against the healthcare database, they will see the address fields:
MATCH (n:Patient)
WHERE n.dateOfBirth < date('1972-06-12')
RETURN n.name, n.ssn, n.address, n.dateOfBirth;+-----------------------------------------------------------------------+ | n.name | n.ssn | n.address | n.dateOfBirth | +-----------------------------------------------------------------------+ | "Mark Jackson" | 1234578 | "1 secret way, downtown" | 1970-11-29 | | "Joe Svensson" | 1234579 | "1 secret way, downtown" | 1972-02-12 | | "Bob Anderson" | 1234597 | "1 secret way, downtown" | 1970-04-27 | | "Sally Anderson" | 1234617 | "1 secret way, downtown" | 1970-12-02 | | "Ally Anderson" | 1234622 | "1 secret way, downtown" | 1972-05-20 | | "Jane Svensson" | 1234644 | "1 secret way, downtown" | 1970-05-24 | | "Sally Anderson" | 1234657 | "1 secret way, downtown" | 1972-01-23 | +-----------------------------------------------------------------------+ 7 rows ready to start consuming query after 4 ms, results consumed after another 2 ms
The other main action that the nurse role should be able to perform is the primary doctor action of saving a diagnosis to the database:
WITH date(datetime({epochmillis:timestamp()})) AS today
MATCH (p:Patient)
WHERE p.ssn = 1234657
MATCH (d:Disease)
WHERE d.name = "Chronic Placeboitis"
MERGE (p)-[i:DIAGNOSIS {by: 'Daniel'}]->(d)
ON CREATE SET i.date = today
RETURN p.name, d.name, i.by, i.date;+------------------------------------------------------------------+ | p.name | d.name | i.by | i.date | +------------------------------------------------------------------+ | "Sally Anderson" | "Chronic Placeboitis" | "Daniel" | 2025-02-14 | +------------------------------------------------------------------+ 1 row ready to start consuming query after 49 ms, results consumed after another 2 ms Created 1 relationships, Set 2 properties
Performing this action, otherwise reserved for the doctor role, involves more responsibility for the nurse.
There might be nurses that should not be entrusted with this option, which is why you can divide the nurse role into senior and junior nurses, for example.
Currently, Daniel is a senior nurse.
Privileges of junior nurse
Previously, creating the nurse role by combining the doctor and receptionist roles led to an undesired scenario as the DENIED privileges of the doctor role overrode the GRANTED privileges of the receptionist.
In that case, the objective was to enhance the permissions of the senior nurse, but when it comes to the junior nurse, they should be able to perform the same actions as the senior, except adding diagnoses to the database.
To achieve this, you can create a special role that contains specifically only the additional restrictions.
Switch to the system database and run the following commands:
CREATE ROLE disableDiagnoses;
DENY CREATE ON GRAPH healthcare RELATIONSHIPS DIAGNOSIS TO disableDiagnoses;And then assign this new role to the nurse Daniel, so you can test the behavior:
GRANT ROLE disableDiagnoses TO daniel;If you check what privileges Daniel has now, it is the combination of the two roles nurse and disableDiagnoses:
SHOW USER daniel PRIVILEGES AS COMMANDS;+---------------------------------------------------------------------+
| command |
+---------------------------------------------------------------------+
| "DENY CREATE ON GRAPH `healthcare` RELATIONSHIP DIAGNOSIS TO $role" |
| "GRANT ACCESS ON DATABASE `healthcare` TO $role" |
| "GRANT ACCESS ON HOME DATABASE TO $role" |
| "GRANT EXECUTE FUNCTION * ON DBMS TO $role" |
| "GRANT EXECUTE PROCEDURE * ON DBMS TO $role" |
| "GRANT LOAD ON ALL DATA TO $role" |
| "GRANT READ {*} ON GRAPH `healthcare` NODE * TO $role" |
| "GRANT READ {*} ON GRAPH `healthcare` RELATIONSHIP * TO $role" |
| "GRANT TRAVERSE ON GRAPH `healthcare` NODE * TO $role" |
| "GRANT TRAVERSE ON GRAPH `healthcare` RELATIONSHIP * TO $role" |
| "GRANT WRITE ON GRAPH `healthcare` TO $role" |
+---------------------------------------------------------------------+
11 rows
ready to start consuming query after 4 ms, results consumed after another 1 ms
Daniel can still see the address fields, and can even perform the diagnosis investigation that the doctor can perform:
MATCH (n:Patient)-[:HAS]->(s:Symptom)-[:OF]->(d:Disease)
WHERE n.ssn = 1234650
RETURN n.ssn, n.name, d.name, count(s) AS score ORDER BY score DESC;+--------------------------------------------------------+ | n.ssn | n.name | d.name | score | +--------------------------------------------------------+ | 1234650 | "Mark Smith" | "Chronic Argitis" | 3 | | 1234650 | "Mark Smith" | "Chronic Otheritis" | 3 | | 1234650 | "Mark Smith" | "Acute Placeboitis" | 3 | | 1234650 | "Mark Smith" | "Chronic Yellowitis" | 3 | | 1234650 | "Mark Smith" | "Chronic Someitis" | 3 | | 1234650 | "Mark Smith" | "Chronic Whatitis" | 2 | | 1234650 | "Mark Smith" | "Acute Otheritis" | 2 | | 1234650 | "Mark Smith" | "Chronic Placeboitis" | 2 | | 1234650 | "Mark Smith" | "Acute Argitis" | 2 | | 1234650 | "Mark Smith" | "Acute Someitis" | 2 | | 1234650 | "Mark Smith" | "Acute Whatitis" | 1 | | 1234650 | "Mark Smith" | "Acute Yellowitis" | 1 | +--------------------------------------------------------+ 12 rows ready to start consuming query after 50 ms, results consumed after another 1 ms
But when they try to save a diagnosis to the database, they will be denied that action:
WITH date(datetime({epochmillis:timestamp()})) AS today
MATCH (p:Patient)
WHERE p.ssn = 1234650
MATCH (d:Disease)
WHERE d.name = "Chronic Placeboitis"
MERGE (p)-[i:DIAGNOSIS {by: 'Daniel'}]->(d)
ON CREATE SET i.date = today
RETURN p.name, d.name, i.by, i.date;+---------------------------------+ | p.name | d.name | i.by | i.date | +---------------------------------+ Create relationship with type 'DIAGNOSIS' on database 'healthcare' is not allowed for user 'daniel' with roles [PUBLIC, disableDiagnoses, nurse].
To promote Daniel back to senior nurse, revoke the role that introduced the restriction:
REVOKE ROLE disableDiagnoses FROM daniel;Building a custom administrator role
The itadmin role was originally created by copying the built-in admin role and adding restrictions.
However, there might be cases in which having `DENY`s can be less convenient than only having `GRANT`s.
Instead, you can build the administrator role from the ground up.
The IT administrator Tina is able to create new users and assign them to the product roles as an itadmin, but you can create a more restricted role called userManager and grant it only the appropriate privileges.
Switch to the system database and run the following commands:
CREATE ROLE userManager;
GRANT USER MANAGEMENT ON DBMS TO userManager;
GRANT ROLE MANAGEMENT ON DBMS TO userManager;
GRANT SHOW PRIVILEGE ON DBMS TO userManager;Test the new behavior by revoking the itadmin role from Tina and grant them the userManager role instead:
REVOKE ROLE itadmin FROM tina;
GRANT ROLE userManager TO tina;These are the privileges granted to userManager:
-
USER MANAGEMENTallows creating, updating, and dropping users. -
ROLE MANAGEMENTallows creating, updating, and dropping roles as well as assigning roles to users. -
SHOW PRIVILEGEallows listing the users' privileges.
Listing Tina’s new privileges should now show a much shorter list than when they were a more powerful administrator with the itadmin role:
SHOW USER tina PRIVILEGES AS COMMANDS;+--------------------------------------------------+ | command | +--------------------------------------------------+ | "GRANT ACCESS ON DATABASE `healthcare` TO $role" | | "GRANT ACCESS ON HOME DATABASE TO $role" | | "GRANT EXECUTE FUNCTION * ON DBMS TO $role" | | "GRANT EXECUTE PROCEDURE * ON DBMS TO $role" | | "GRANT LOAD ON ALL DATA TO $role" | | "GRANT ROLE MANAGEMENT ON DBMS TO $role" | | "GRANT SHOW PRIVILEGE ON DBMS TO $role" | | "GRANT USER MANAGEMENT ON DBMS TO $role" | +--------------------------------------------------+ 8 rows ready to start consuming query after 24 ms, results consumed after another 1 ms
|
No other privilege management privileges were granted here.
How much power this role should have would depend on the requirements of the system.
Refer to the section The |
Now Tina should be able to create new users and assign them to roles (from the system database):
CREATE USER sally SET PASSWORD 'secretpassword' CHANGE REQUIRED;
GRANT ROLE receptionist TO sally;
SHOW USER sally PRIVILEGES AS COMMANDS;0 rows
ready to start consuming query after 45 ms, results consumed after another 0 ms
0 rows
ready to start consuming query after 4 ms, results consumed after another 0 ms
+------------------------------------------------------------------------+
| command |
+------------------------------------------------------------------------+
| "GRANT ACCESS ON DATABASE `healthcare` TO $role" |
| "GRANT ACCESS ON HOME DATABASE TO $role" |
| "GRANT CREATE ON GRAPH `healthcare` NODE Patient TO $role" |
| "GRANT DELETE ON GRAPH `healthcare` NODE Patient TO $role" |
| "GRANT DELETE ON GRAPH `healthcare` RELATIONSHIP DIAGNOSIS TO $role" |
| "GRANT DELETE ON GRAPH `healthcare` RELATIONSHIP HAS TO $role" |
| "GRANT EXECUTE FUNCTION * ON DBMS TO $role" |
| "GRANT EXECUTE PROCEDURE * ON DBMS TO $role" |
| "GRANT LOAD ON ALL DATA TO $role" |
| "GRANT MATCH {*} ON GRAPH `healthcare` NODE Patient TO $role" |
| "GRANT SET PROPERTY {*} ON GRAPH `healthcare` NODE Patient TO $role" |
| "GRANT TRAVERSE ON GRAPH `healthcare` NODE Disease TO $role" |
| "GRANT TRAVERSE ON GRAPH `healthcare` NODE Symptom TO $role" |
| "GRANT TRAVERSE ON GRAPH `healthcare` RELATIONSHIP DIAGNOSIS TO $role" |
| "GRANT TRAVERSE ON GRAPH `healthcare` RELATIONSHIP HAS TO $role" |
+------------------------------------------------------------------------+
15 rows
ready to start consuming query after 3 ms, results consumed after another 0 ms