Configuring SSL
The Neo4j SSL Framework can be used with Neo4j Helm charts.
You can specify SSL policy objects for bolt, https, cluster, and backup.
SSL public certificates and private keys to use with a Neo4j Helm deployment must be stored in Kubernetes Secrets.
To enable Neo4j SSL policies, configure the ssl.<policy name> object in the Neo4j Helm deployment’s values.yaml file to reference the Kubernetes Secrets containing the SSL certificates and keys to use.
This example shows how to configure the bolt SSL policy:
ssl:
bolt:
privateKey:
secretName: bolt-cert
subPath: private.key
publicCertificate:
secretName: bolt-cert
subPath: public.crtWhen a private key is specified in the values.yaml file, the Neo4j ssl policy is enabled automatically.
To disable a policy, add dbms.ssl.policy.{{ $name }}.enabled: "false" to the config object.
|
Unencrypted |
For more information on configuring SSL policies, see SSL Framework configuration.
The following examples show how to deploy a Neo4j cluster with configured SSL policies.
Create a self-signed certificate
If you do not have a self-signed certificate to use, follow the steps to create one:
-
Create a new folder for the self-signed certificate. This example uses the /neo4j-ssl folder.
mkdir neo4j-ssl cd neo4j-ssl -
Create the
private.keyandpublic.crtfor the self-signed certificate by using theopensslcommand and passing all the values in thesubjargument:openssl req -newkey rsa:2048 -nodes -keyout private.key -x509 -days 365 -out public.crt -subj "/C=GB/ST=London/L=London/O=Neo4j/OU=IT Department" -
Verify that the private.key and public.crt files are created:
ls -lstExample output-rw-r--r-- 1 user staff 1679 28 Dec 15:00 private.key -rw-r--r-- 1 user staff 1679 28 Dec 15:00 public.crt
Create a neo4j namespace and configure it to be used in the current context
kubectl create namespace neo4j
kubectl config set-context --current --namespace=neo4jConfigure an SSL policy using a tls Kubernetes secret
This example shows how to configure an SSL policy for intra-cluster communication using a self-signed certificate stored in a tls Kubernetes secret.
-
Create a Kubernetes TSL secret using the public.crt and private.key files:
You must have a Kubernetes cluster running and the kubectlcommand installed. For more information, see Prerequisites.-
To create a TLS secret, use the
tlsoption and a secret name, e.g.,neo4j-tls:kubectl create secret tls neo4j-tls --cert=/path/to/neo4j-ssl/public.crt --key=/path/to/neo4j-ssl/private.key -
Verify that the secret is created:
kubectl get secretExample outputNAME TYPE DATA AGE neo4j-tls kubernetes.io/tls 2 4s
-
Verify that the secret contains the public.crt and private.key files:
kubectl get secret neo4j-tls -o yamlExample outputapiVersion: v1 data: tls.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURLakNDQWhJQ0NRRGRYYVg1Y29mczdEQU5CZ2txaGtpRzl3MEJBUXNGQURCWE1Rc3dDUVlEVlFRR0V3SkgKUWpFUE1BMEdBMVVFQ0F3R1RHOXVaRzl1TVE4d0RRWURWUVFIREFaTWIyNWtiMjR4RGpBTUJnTlZCQW9NQlU1bApielJxTVJZd0ZBWURWUVFMREExSlZDQkVaWEJoY25SdFpXNTBNQjRYRFRJeU1USXlPREl4TURjeU5sb1hEVEl6Ck1USXlPREl4TURjeU5sb3dWekVMTUFrR0ExVUVCaE1DUjBJeER6QU5CZ05WQkFnTUJreHZibVJ2YmpFUE1BMEcKQTFVRUJ3d0dURzl1Wkc5dU1RNHdEQVlEVlFRS0RBVk9aVzgwYWpFV01CUUdBMVVFQ3d3TlNWUWdSR1Z3WVhKMApiV1Z1ZERDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTDBRc0c2Ukwrd3hxZSt3CjJGSWljZldVaUFtdmNqeVdlS0lKaThuT2tBSGIvSTYzUUU2L3ZpR3RNeEI3S28xdUJLNlVPZXBaeU91UzE2bUMKaitpMDAwbmFnWkR3RGNyRXd3UUE1cTBGMC90VXB5UHBaL1p3clhEaGFDOXhzVnFnVms0TXl5aUtTNzRIOUc2UgprUUV4dHBaNFArcTlaRHVFVk1KVGVaL2pQNGZoTkg2MUpSTVdORTJ3NjNUWkx2ZGMyUitXL2U5N3h2TGQ5Y0FnCjlqTm9FMHo5UHRmczB2L2lyUGhuUHpzWHQ5bzE0MWlnOVFZNjNtMzBxQ0NaYnpMRlR6WFgvdTUvTSsycFB3WXoKcUNOTUZYYW1ITlAxdlRPWFlRTG1iYW1JdVplYnVPNEVlUHZ6WUVXSmEyUi9oTmhtUDNvM2tRVFAzdmF1UEFjZQpSQlJZS09NQ0F3RUFBVEFOQmdrcWhraUc5dzBCQVFzRkFBT0NBUUVBWVh6SkIzNU55cExDUEdvQXVJdGt5dHBFCk1ZeSs5YnlrV3BEVnhRaXZLUHQ3d1NUaWZjNU1QdW5NUy9xYmxnaWprWm5IaWVLeEdoU3lQL283QndtMzJDSnAKQUFsSjJ3RjhIVXVSSGpYcUU5dkNQeFdtVlVJS2ExOWN5V0tUYWhySWU1eWZkQWNkbUJmRzJNWnY0dEdFeWxsUgo0Vk81STdRNjVWZDlGQnB0U3JjS3R1WUtBUzg2RTBHZmlmMWxCakdUZTFZbkhvK1RZTVpoVEUvN3RlNHZ1M251CjA4Y1BmbS9RYThSNFBXZDZNbXVDaTJYcDduWVlEMmp3WklCSENtMUU3U1RrdS9JRk5kOWFWRW91VG5KR1pCWFcKeWVzWG9OMXhOb3kvMXZFdElhV2xXZW1GcGo4clJ6VGJQekQ1TEpiNDBSRFVOTXN3NytLUXczV3BBMjVKUHc9PQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg== tls.key: LS0tLS1CRUdJTiBQUklWQVRFIEtFWS0tLS0tCk1JSUV2QUlCQURBTkJna3Foa2lHOXcwQkFRRUZBQVNDQktZd2dnU2lBZ0VBQW9JQkFRQzlFTEJ1a1Mvc01hbnYKc05oU0luSDFsSWdKcjNJOGxuaWlDWXZKenBBQjIveU90MEJPdjc0aHJUTVFleXFOYmdTdWxEbnFXY2pya3RlcApnby9vdE5OSjJvR1E4QTNLeE1NRUFPYXRCZFA3VktjajZXZjJjSzF3NFdndmNiRmFvRlpPRE1zb2lrdStCL1J1CmtaRUJNYmFXZUQvcXZXUTdoRlRDVTNtZjR6K0g0VFIrdFNVVEZqUk5zT3QwMlM3M1hOa2ZsdjN2ZThieTNmWEEKSVBZemFCTk0vVDdYN05MLzRxejRaejg3RjdmYU5lTllvUFVHT3Q1dDlLZ2dtVzh5eFU4MTEvN3VmelB0cVQ4RwpNNmdqVEJWMnBoelQ5YjB6bDJFQzVtMnBpTG1YbTdqdUJIajc4MkJGaVd0a2Y0VFlaajk2TjVFRXo5NzJyandICkhrUVVXQ2pqQWdNQkFBRUNnZ0VBTmF6OVNnYXlJazVmUG90b2Zya0V2WUh6dFR3NEpIZGJ2RFVWbUsrcU5yenIKME9DNXd5R3dxd0x2RW1qRlJlM01Lbnd1alJmOGNOVDVvVWhON3ZVWFgwcEhxb3hjZmdxcWl3SnVld1RDa0FJUwppYUdFUUhUdzZMRTEwUEpvTmFCN29DRUZ0SGErMWk2UCtLd2ZETVcrWHEyNUI3M0pMUlIrczhUYkxNZHBpL3VvCjRmTFNJV0xDV09MZThUTlU0ck5vVDQ0enY0eUhUOXAyV3liSUNrL3F5bVV3bTlhRHFnYzRJRzk4YXVVNG5JYVQKenk2T3NBODdONW9FME0rcHlUdEFJcmxRZFBXUzBBZ28xZUJCcWplL1I3MTI4TmdHVzhOTzVMWDBtNit2YzhyVgpaTHh0N1d0NThucXR2WlI3QTF5SU9lbWtocHl2Q3hrNVRxSmZQRlJxRVFLQmdRRGlOL3NBZncrZ1dvTFpLbTNyCm50WVkyRW9TOTBkQ0wwd293SGFGa0lsL2hIWXduQi9qaWlnMU5ZbEhDNzNPVDdDc2UycS9tS0xhMzZBVHlpTHcKZjN1T0J3NmNFZ2RJZlU5aDBtZjJCNFZXdEVEeDJMSU94MEtZU2VrYldTTVZQZ2w2SkhNb3hLdjNMbEx5R1RiMApZQmtKVmpRdkVLS1dpa1FLMUdPYnZtdzFWUUtCZ1FEVjlJLzc5WFJuN1EzZ3M4Z2JqZWhDejRqNHdtNWdpNFM2CkVsVzVJWkFidDh3QWZPdVIzUm4wQW41NFl0ZW1HUk1seDF0L1ZUM1IzK0J5bmVTZEgzbUJ6eVJEQysvRGhBTlYKNVZPckk5SFhnVTRMSElVMmNwVVZxYVo3N1J1b2JnTmlDenBmOVZPVkNadzdmQzRPYkFqcTMzQ3RtT2taR0hRbAo2dkJtNm1ubFZ3S0JnQ2FnOW95TUplZjA3TGtXcExTQ1ovN1FHRDRLMmJFMGtHVzVEOFFZL1ZHNEZkS1JKbVRkCmQ2WTJZUjJ2cEpheFJ2TDlGQ3BwYncyKzkvL0pHWlJGd0p4dEdoS09oWTNjVUF6ZE9BRnNJVm0vNkFNa1JLdC8KWFNEU0ppc1VXb2hMRXFVM3lpNWcveGh6WVppVHM2MmhKMFZQNGhOVFhPQWw5aDUvVEE4UlFqc05Bb0dBTm84Twp5R2xuTGJrOWVMZGZwK2NmK3ltQS9DNVloellNdW9aQ1pkc3hMR0JLSFRXOXZJeHRPZFFJL0JuNGM5cWhEMWt1CjgrR0F5aXdVeUNXTFRxWGdEa0lNTlN5dUQyVnlsRXpPY1MzSkxQTkVPNEVpVnlnUTdGMCtud3R2cWh1anNUUzcKeGd5Qks5Z3ZodHU3d3VHNXhHc0dDTDZkY2xEU0RYbERwSHJTVmpFQ2dZQWx0STNjMzJxaG5KU2xHSGhjdW1wRwpReGpvYnJBUUxUa3dyOWk2TkNuS0EyNVR1SVFXa1NiN2JUWWtuUi80WDhOT2w2U2EvYm9QK2dncWNJM0haSk05CkxJRnpPUTFWT1luQ2ZYZVd0SmlHQklwUExadFdobnA3NGVhdmJKYW9udlhVVGNZcm5qcytIWGhpaFhjOUhENWsKeEJEaWJKYUlEbXg2T1FpVWI2RndJZz09Ci0tLS0tRU5EIFBSSVZBVEUgS0VZLS0tLS0K kind: Secret metadata: creationTimestamp: "2023-01-04T13:53:14Z" managedFields: - apiVersion: v1 fieldsType: FieldsV1 fieldsV1: f:data: .: {} f:tls.crt: {} f:tls.key: {} f:type: {} manager: kubectl operation: Update time: "2023-01-04T13:53:14Z" name: neo4j-tls namespace: neo4j resourceVersion: "212009" uid: b1be45dd-4cbe-41c9-a6e5-c814c5e39c25 type: kubernetes.io/tls
-
-
Configure
sslobject in the ssl-values.yaml file using the created secret:ssl: # setting per "connector" matching neo4j config bolt: privateKey: secretName: neo4j-tls subPath: tls.key publicCertificate: secretName: neo4j-tls subPath: tls.crt https: privateKey: secretName: neo4j-tls subPath: tls.key publicCertificate: secretName: neo4j-tls subPath: tls.crt trustedCerts: sources: - secret: name: neo4j-tls items: - key: tls.crt path: public.crt cluster: privateKey: secretName: neo4j-tls subPath: tls.key publicCertificate: secretName: neo4j-tls subPath: tls.crt trustedCerts: sources: - secret: name: neo4j-tls items: - key: tls.crt path: public.crt revokedCerts: sources: [ ]
Now you are ready to deploy the Neo4j cluster using the configured ssl-values.yaml file and the Neo4j Helm charts.
Configure an SSL policy using a generic Kubernetes secret
This example shows how to configure an SSL policy for intra-cluster communication using a self-signed certificate stored in a generic Kubernetes secret.
-
Create a Kubernetes
genericsecret using the public.crt and private.key files:You must have a Kubernetes cluster running and the kubectlcommand installed. For more information, see Prerequisites.-
Get the Base64-encoded value of your public.crt and private.key:
cat public.crt| base64cat private.key| base64 -
Using the Base64-encoded values of your public.crt and private.key, create a secret.yaml file:
apiVersion: v1 data: public.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURLakNDQWhJQ0NRRGRYYVg1Y29mczdEQU5CZ2txaGtpRzl3MEJBUXNGQURCWE1Rc3dDUVlEVlFRR0V3SkgKUWpFUE1BMEdBMVVFQ0F3R1RHOXVaRzl1TVE4d0RRWURWUVFIREFaTWIyNWtiMjR4RGpBTUJnTlZCQW9NQlU1bApielJxTVJZd0ZBWURWUVFMREExSlZDQkVaWEJoY25SdFpXNTBNQjRYRFRJeU1USXlPREl4TURjeU5sb1hEVEl6Ck1USXlPREl4TURjeU5sb3dWekVMTUFrR0ExVUVCaE1DUjBJeER6QU5CZ05WQkFnTUJreHZibVJ2YmpFUE1BMEcKQTFVRUJ3d0dURzl1Wkc5dU1RNHdEQVlEVlFRS0RBVk9aVzgwYWpFV01CUUdBMVVFQ3d3TlNWUWdSR1Z3WVhKMApiV1Z1ZERDQ0FTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBTDBRc0c2Ukwrd3hxZSt3CjJGSWljZldVaUFtdmNqeVdlS0lKaThuT2tBSGIvSTYzUUU2L3ZpR3RNeEI3S28xdUJLNlVPZXBaeU91UzE2bUMKaitpMDAwbmFnWkR3RGNyRXd3UUE1cTBGMC90VXB5UHBaL1p3clhEaGFDOXhzVnFnVms0TXl5aUtTNzRIOUc2UgprUUV4dHBaNFArcTlaRHVFVk1KVGVaL2pQNGZoTkg2MUpSTVdORTJ3NjNUWkx2ZGMyUitXL2U5N3h2TGQ5Y0FnCjlqTm9FMHo5UHRmczB2L2lyUGhuUHpzWHQ5bzE0MWlnOVFZNjNtMzBxQ0NaYnpMRlR6WFgvdTUvTSsycFB3WXoKcUNOTUZYYW1ITlAxdlRPWFlRTG1iYW1JdVplYnVPNEVlUHZ6WUVXSmEyUi9oTmhtUDNvM2tRVFAzdmF1UEFjZQpSQlJZS09NQ0F3RUFBVEFOQmdrcWhraUc5dzBCQVFzRkFBT0NBUUVBWVh6SkIzNU55cExDUEdvQXVJdGt5dHBFCk1ZeSs5YnlrV3BEVnhRaXZLUHQ3d1NUaWZjNU1QdW5NUy9xYmxnaWprWm5IaWVLeEdoU3lQL283QndtMzJDSnAKQUFsSjJ3RjhIVXVSSGpYcUU5dkNQeFdtVlVJS2ExOWN5V0tUYWhySWU1eWZkQWNkbUJmRzJNWnY0dEdFeWxsUgo0Vk81STdRNjVWZDlGQnB0U3JjS3R1WUtBUzg2RTBHZmlmMWxCakdUZTFZbkhvK1RZTVpoVEUvN3RlNHZ1M251CjA4Y1BmbS9RYThSNFBXZDZNbXVDaTJYcDduWVlEMmp3WklCSENtMUU3U1RrdS9JRk5kOWFWRW91VG5KR1pCWFcKeWVzWG9OMXhOb3kvMXZFdElhV2xXZW1GcGo4clJ6VGJQekQ1TEpiNDBSRFVOTXN3NytLUXczV3BBMjVKUHc9PQotLS0tLUVORCBDRVJUSUZJQ0FURS0tLS0tCg== private.key: LS0tLS1CRUdJTiBQUklWQVRFIEtFWS0tLS0tCk1JSUV2QUlCQURBTkJna3Foa2lHOXcwQkFRRUZBQVNDQktZd2dnU2lBZ0VBQW9JQkFRQzlFTEJ1a1Mvc01hbnYKc05oU0luSDFsSWdKcjNJOGxuaWlDWXZKenBBQjIveU90MEJPdjc0aHJUTVFleXFOYmdTdWxEbnFXY2pya3RlcApnby9vdE5OSjJvR1E4QTNLeE1NRUFPYXRCZFA3VktjajZXZjJjSzF3NFdndmNiRmFvRlpPRE1zb2lrdStCL1J1CmtaRUJNYmFXZUQvcXZXUTdoRlRDVTNtZjR6K0g0VFIrdFNVVEZqUk5zT3QwMlM3M1hOa2ZsdjN2ZThieTNmWEEKSVBZemFCTk0vVDdYN05MLzRxejRaejg3RjdmYU5lTllvUFVHT3Q1dDlLZ2dtVzh5eFU4MTEvN3VmelB0cVQ4RwpNNmdqVEJWMnBoelQ5YjB6bDJFQzVtMnBpTG1YbTdqdUJIajc4MkJGaVd0a2Y0VFlaajk2TjVFRXo5NzJyandICkhrUVVXQ2pqQWdNQkFBRUNnZ0VBTmF6OVNnYXlJazVmUG90b2Zya0V2WUh6dFR3NEpIZGJ2RFVWbUsrcU5yenIKME9DNXd5R3dxd0x2RW1qRlJlM01Lbnd1alJmOGNOVDVvVWhON3ZVWFgwcEhxb3hjZmdxcWl3SnVld1RDa0FJUwppYUdFUUhUdzZMRTEwUEpvTmFCN29DRUZ0SGErMWk2UCtLd2ZETVcrWHEyNUI3M0pMUlIrczhUYkxNZHBpL3VvCjRmTFNJV0xDV09MZThUTlU0ck5vVDQ0enY0eUhUOXAyV3liSUNrL3F5bVV3bTlhRHFnYzRJRzk4YXVVNG5JYVQKenk2T3NBODdONW9FME0rcHlUdEFJcmxRZFBXUzBBZ28xZUJCcWplL1I3MTI4TmdHVzhOTzVMWDBtNit2YzhyVgpaTHh0N1d0NThucXR2WlI3QTF5SU9lbWtocHl2Q3hrNVRxSmZQRlJxRVFLQmdRRGlOL3NBZncrZ1dvTFpLbTNyCm50WVkyRW9TOTBkQ0wwd293SGFGa0lsL2hIWXduQi9qaWlnMU5ZbEhDNzNPVDdDc2UycS9tS0xhMzZBVHlpTHcKZjN1T0J3NmNFZ2RJZlU5aDBtZjJCNFZXdEVEeDJMSU94MEtZU2VrYldTTVZQZ2w2SkhNb3hLdjNMbEx5R1RiMApZQmtKVmpRdkVLS1dpa1FLMUdPYnZtdzFWUUtCZ1FEVjlJLzc5WFJuN1EzZ3M4Z2JqZWhDejRqNHdtNWdpNFM2CkVsVzVJWkFidDh3QWZPdVIzUm4wQW41NFl0ZW1HUk1seDF0L1ZUM1IzK0J5bmVTZEgzbUJ6eVJEQysvRGhBTlYKNVZPckk5SFhnVTRMSElVMmNwVVZxYVo3N1J1b2JnTmlDenBmOVZPVkNadzdmQzRPYkFqcTMzQ3RtT2taR0hRbAo2dkJtNm1ubFZ3S0JnQ2FnOW95TUplZjA3TGtXcExTQ1ovN1FHRDRLMmJFMGtHVzVEOFFZL1ZHNEZkS1JKbVRkCmQ2WTJZUjJ2cEpheFJ2TDlGQ3BwYncyKzkvL0pHWlJGd0p4dEdoS09oWTNjVUF6ZE9BRnNJVm0vNkFNa1JLdC8KWFNEU0ppc1VXb2hMRXFVM3lpNWcveGh6WVppVHM2MmhKMFZQNGhOVFhPQWw5aDUvVEE4UlFqc05Bb0dBTm84Twp5R2xuTGJrOWVMZGZwK2NmK3ltQS9DNVloellNdW9aQ1pkc3hMR0JLSFRXOXZJeHRPZFFJL0JuNGM5cWhEMWt1CjgrR0F5aXdVeUNXTFRxWGdEa0lNTlN5dUQyVnlsRXpPY1MzSkxQTkVPNEVpVnlnUTdGMCtud3R2cWh1anNUUzcKeGd5Qks5Z3ZodHU3d3VHNXhHc0dDTDZkY2xEU0RYbERwSHJTVmpFQ2dZQWx0STNjMzJxaG5KU2xHSGhjdW1wRwpReGpvYnJBUUxUa3dyOWk2TkNuS0EyNVR1SVFXa1NiN2JUWWtuUi80WDhOT2w2U2EvYm9QK2dncWNJM0haSk05CkxJRnpPUTFWT1luQ2ZYZVd0SmlHQklwUExadFdobnA3NGVhdmJKYW9udlhVVGNZcm5qcytIWGhpaFhjOUhENWsKeEJEaWJKYUlEbXg2T1FpVWI2RndJZz09Ci0tLS0tRU5EIFBSSVZBVEUgS0VZLS0tLS0K kind: Secret metadata: name: neo4j-tls namespace: neo4j type: Opaque -
Create the generic secret using the
kubectl createcommand and the secret.yaml file:kubectl create -f /path/to/secret.yamlExample outputsecret/neo4j-tls created
-
Verify that the secret is created:
kubectl get secretExample outputNAME TYPE DATA AGE neo4j-tls Opaque 2 85s
-
-
Configure the
sslobject in the ssl-values.yaml file using the created secret:ssl: # setting per "connector" matching neo4j config bolt: privateKey: secretName: neo4j-tls subPath: private.key publicCertificate: secretName: neo4j-tls subPath: public.crt https: privateKey: secretName: neo4j-tls subPath: private.key publicCertificate: secretName: neo4j-tls subPath: public.crt trustedCerts: sources: - secret: name: neo4j-tls items: - key: public.crt path: public.crt cluster: privateKey: secretName: neo4j-tls subPath: private.key publicCertificate: secretName: neo4j-tls subPath: public.crt trustedCerts: sources: - secret: name: neo4j-tls items: - key: public.crt path: public.crt revokedCerts: sources: [ ]
Now you are ready to deploy the Neo4j cluster using the ssl-values.yaml file and the Neo4j Helm charts.
Deploy a Neo4j cluster with SSL certificates
Deploy a Neo4j cluster using the Neo4j Helm chart and the ssl-values.yaml file.
-
Install server-1:
helm install server-1 neo4j/neo4j --namespace neo4j --set neo4j.acceptLicenseAgreement=yes --set neo4j.password=my-password --set neo4j.name="my-cluster" --set neo4j.minimumClusterSize=3 --set neo4j.edition="enterprise" --set volumes.data.mode=defaultStorageClass -f ~/Documents/neo4j-ssl/ssl-values.yaml -
Repeat the command from the previous step for
server-2andserver-3. -
Verify that the Neo4j cluster is running:
kubectl get podsExample outputNAME READY STATUS RESTARTS AGE server-1-0 1/1 Running 0 2m server-2-0 1/1 Running 0 2m server-3-0 1/1 Running 0 2m
-
Connect to one of the servers and verify that the /certificates/cluster directory contains the certificates:
kubectl exec -it server-1-0 -- bashneo4j@server-1-0:~$ cd certificates/ neo4j@server-1-0:~/certificates$ ls -lstExample outputtotal 12 4 drwxr-xr-x 2 root root 4096 Jan 4 13:55 bolt 4 drwxr-xr-x 3 root root 4096 Jan 4 13:55 cluster 4 drwxr-xr-x 3 root root 4096 Jan 4 13:55 https
neo4j@server-1-0:~/certificates$ cd cluster/ neo4j@server-1-0:~/certificates/cluster$ ls -lstExample outputtotal 8 0 drwxrwsrwt 3 root neo4j 100 Jan 4 13:56 trusted 4 -rw-r--r-- 1 root neo4j 1704 Jan 4 13:56 private.key 4 -rw-r--r-- 1 root neo4j 1159 Jan 4 13:56 public.crt
neo4j@server-1-0:~/certificates/cluster$ cd trusted/ neo4j@server-1-0:~/certificates/cluster/trusted$ ls -lstExample outputtotal 0 0 lrwxrwxrwx 1 root neo4j 17 Jan 4 13:56 public.crt -> ..data/public.crt
-
Exit the pod:
exit -
Check that the LoadBalancer service is available using the
neo4j.nameused for the installation:export NEO4J_NAME=my-cluster kubectl get service ${NEO4J_NAME}-lb-neo4jExample outputNAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE my-cluster-lb-neo4j LoadBalancer 10.0.134.210 20.237.50.207 7474:31168/TCP,7473:31045/TCP,7687:32708/TCP 3m30s
-
Connect to the Neo4j cluster using one of the following options:
-
Neo4j Browser:
-
Open a web browser and type https://lb-EXTERNAL_IP:7473 (in this example, https://20.237.50.207:7473/browser/). You should see the Neo4j browser.
-
Authenticate using the user
neo4jand the password you set when deploying the cores, in this example,my-password. -
Verify that the cluster is online by running
:sysinfoorSHOW SERVERS: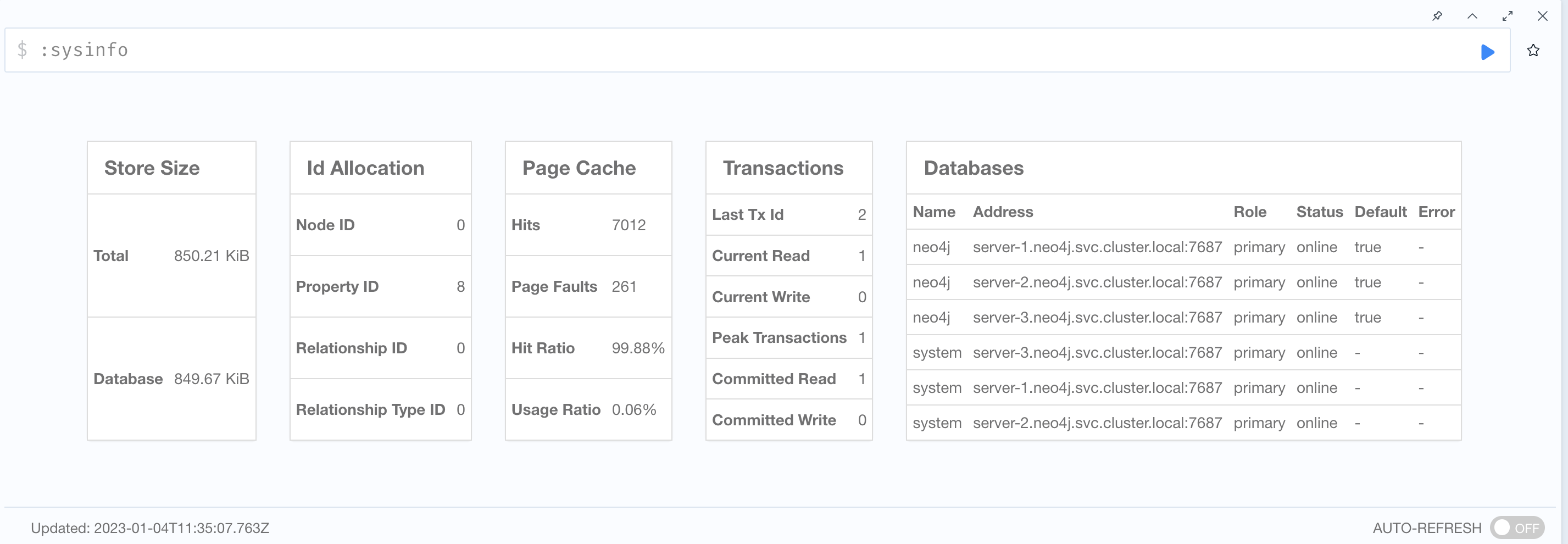
-
Run
SHOW SETTINGS YIELD name, value WHERE name CONTAINS 'ssl'to verify that the configuration is deployed as expected.
-
-
Cypher Shell:
-
Open a terminal and connect to one of the cluster pods:
kubectl exec -it server-1-0 -- bash -
Navigate to the bin directory and connect to server-1 using
cypher-shell:neo4j@server-1-0:~$ cd bin neo4j@server-1-0:~/bin$ ./cypher-shell -u neo4j -p my-password -a neo4j+ssc://server-1.neo4j.svc.cluster.local:7687Example outputConnected to Neo4j using Bolt protocol version 5.26 at neo4j+ssc://server-1.neo4j.svc.cluster.local:7687 as user neo4j. Type :help for a list of available commands or :exit to exit the shell. Note that Cypher queries must end with a semicolon. neo4j@neo4j>
-
Verify that the cluster is online by running
SHOW SERVERS:neo4j@server-1-0:~/bin$ SHOW SERVERS;Example output+-----------------------------------------------------------------------------------------------------------------------------------+ | name | address | state | health | hosting | +-----------------------------------------------------------------------------------------------------------------------------------+ | "1c5946b1-0eb5-43b9-a549-5601087c57f2" | "server-3.neo4j.svc.cluster.local:7687" | "Enabled" | "Available" | ["neo4j", "system"] | | "ba63cd32-3e7d-4042-9935-c8eba925a98f" | "server-1.neo4j.svc.cluster.local:7687" | "Enabled" | "Available" | ["neo4j", "system"] | | "cbad7ed6-0c13-4ba7-b6a1-f20c5552dfcd" | "server-2.neo4j.svc.cluster.local:7687" | "Enabled" | "Available" | ["neo4j", "system"] | +-----------------------------------------------------------------------------------------------------------------------------------+
-
Run
SHOW SETTINGS YIELD name, value WHERE name CONTAINS 'ssl'to verify that the configuration is deployed as expected.Example output+----------------------------------------------------------------------------------------------------+ | name | value | +----------------------------------------------------------------------------------------------------+ | "dbms.netty.ssl.provider" | "JDK" | | "dbms.ssl.policy.bolt.base_directory" | "/var/lib/neo4j/certificates/bolt" | | "dbms.ssl.policy.bolt.ciphers" | "No Value" | | "dbms.ssl.policy.bolt.client_auth" | "NONE" | | "dbms.ssl.policy.bolt.enabled" | "true" | | "dbms.ssl.policy.bolt.private_key" | "/var/lib/neo4j/certificates/bolt/private.key" | | "dbms.ssl.policy.bolt.private_key_password" | "No Value" | | "dbms.ssl.policy.bolt.public_certificate" | "/var/lib/neo4j/certificates/bolt/public.crt" | | "dbms.ssl.policy.bolt.revoked_dir" | "/var/lib/neo4j/certificates/bolt/revoked" | | "dbms.ssl.policy.bolt.tls_versions" | "TLSv1.2" | | "dbms.ssl.policy.bolt.trust_all" | "false" | | "dbms.ssl.policy.bolt.trusted_dir" | "/var/lib/neo4j/certificates/bolt/trusted" | | "dbms.ssl.policy.bolt.verify_hostname" | "true" | | "dbms.ssl.policy.cluster.base_directory" | "/var/lib/neo4j/certificates/cluster" | | "dbms.ssl.policy.cluster.ciphers" | "No Value" | | "dbms.ssl.policy.cluster.client_auth" | "REQUIRE" | | "dbms.ssl.policy.cluster.enabled" | "true" | | "dbms.ssl.policy.cluster.private_key" | "/var/lib/neo4j/certificates/cluster/private.key" | | "dbms.ssl.policy.cluster.private_key_password" | "No Value" | | "dbms.ssl.policy.cluster.public_certificate" | "/var/lib/neo4j/certificates/cluster/public.crt" | | "dbms.ssl.policy.cluster.revoked_dir" | "/var/lib/neo4j/certificates/cluster/revoked" | | "dbms.ssl.policy.cluster.tls_versions" | "TLSv1.2" | | "dbms.ssl.policy.cluster.trust_all" | "false" | | "dbms.ssl.policy.cluster.trusted_dir" | "/var/lib/neo4j/certificates/cluster/trusted" | | "dbms.ssl.policy.cluster.verify_hostname" | "true" | | "dbms.ssl.policy.https.base_directory" | "/var/lib/neo4j/certificates/https" | | "dbms.ssl.policy.https.ciphers" | "No Value" | | "dbms.ssl.policy.https.client_auth" | "NONE" | | "dbms.ssl.policy.https.enabled" | "true" | | "dbms.ssl.policy.https.private_key" | "/var/lib/neo4j/certificates/https/private.key" | | "dbms.ssl.policy.https.private_key_password" | "No Value" | | "dbms.ssl.policy.https.public_certificate" | "/var/lib/neo4j/certificates/https/public.crt" | | "dbms.ssl.policy.https.revoked_dir" | "/var/lib/neo4j/certificates/https/revoked" | | "dbms.ssl.policy.https.tls_versions" | "TLSv1.2" | | "dbms.ssl.policy.https.trust_all" | "false" | | "dbms.ssl.policy.https.trusted_dir" | "/var/lib/neo4j/certificates/https/trusted" | | "dbms.ssl.policy.https.verify_hostname" | "true" | +----------------------------------------------------------------------------------------------------+ 37 rows ready to start consuming query after 212 ms, results consumed after another 11 ms
-
-